Timing Attack on C mod p - PowerPoint PPT Presentation
1 / 13
Title:
Timing Attack on C mod p
Description:
A Countermeasure. A standard countermeasure is to randomize the parameters. ... Other Countermeasures. These randomization can be combined. However, the ... – PowerPoint PPT presentation
Number of Views:29
Avg rating:3.0/5.0
Title: Timing Attack on C mod p
1
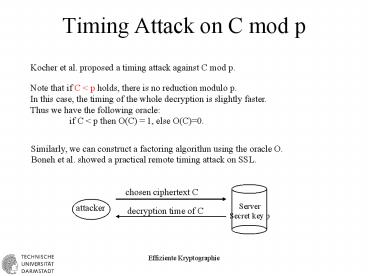
Timing Attack on C mod p
Kocher et al. proposed a timing attack against C
mod p.
Note that if C lt p holds, there is no reduction
modulo p. In this case, the timing of the whole
decryption is slightly faster. Thus we have the
following oracle if C lt p then
O(C) 1, else O(C)0.
Similarly, we can construct a factoring algorithm
using the oracle O. Boneh et al. showed a
practical remote timing attack on SSL.
chosen ciphertext C
Server Secret key p
attacker
decryption time of C
2
A Countermeasure
A standard countermeasure is to randomize the
parameters.
Input c, p, q, dp, dq, p_inv_q Output m
1. generate random integer r in Z/nZ 2.
compute t cre mod n 3. compute s
RSA_CRT_Decryption(t,p,q,dp,dq,p_inv_q) 4.
compute m s r-1 mod n 5. return m.
Correctness s td (cre)d cd red m r mod
n. The ciphertext t to the decryption oracle is
randomized by r, and thus the attacker cannot
manipulate the size of ciphertext t.
Problem The overhead of re mod n, r-1 mod n is
large.
3
Other Countermeasures
(1) Randomization of secret exponent
(2) Randomization of secret prime (3)
Randomization of ciphertext
These randomization can be combined. However, the
overhead is quite large.
4
Advantage of ECC
(1)The security of ECC is based on the discrete
logarithm problem of elliptic curves over
finite fields. (2)There are no sub-exponential
time algorithm to solve it. Thus 1024-bit RSA
is considered as secure as160-bit ECC. (3)ECC
is suitable for the implementation over memory
constraint computing environment like smart
cards.
5
Example of Parameters
RSA e 10001 n 826ed558a0f0cba7ae09485a
bf80c544837efeb7116153f5d6479d5945fdb6c61f50c98444
5d601d85eceb6b ad9f700b90ae28984dd590f5ca
3e6ed968a3ca32a5cf584992d92590ae9ed4f81b70d008a9e4
a16905925dbb 79d82b67dc6b70869a83f037c147
d298c0e2eea5f858f3881ad1071c5c221ecb795d78b68bae78
63 d 21b67db4237d72766beea667b95143c0a22f4f07
b4f25d1b75e400397b45b7c45e108addc4f03a9000d0fb5
c76da4480fef42651830090682b1a0bfadeb92dee04
7626b1417651aa832469b59792e2fc8688d187201d6d
0c7de9301144e003473ecbf859ababa15311adea452d16
0f11b5b5fe2338b00e57728b4b691f43fc1d618df8
1e60b14c23f3e3fff1e9d6d1002aa8c4ce889f6017d6d90b
c4cbfb5386 ECC p ffffffff ffffffff ffffffff
ffffffff 7fffffff a ffffffff ffffffff
ffffffff ffffffff 7ffffffC b 1c97befc
54bd7a8b 65acf89f 81d4d4ad c565fa45 x
4a96b568 8ef57328 46646989 68c38bb9 13cbfc82 y
23a62855 3168947d 59dcc912 04235137 7ac5fb32
n 01 00000000 00000000 0001f4c8 f927aed3
ca752257 h 01 s 203370bf 41c7ca08
22e2ccd8 f4d4a011 91977373
6
Elliptic Curves
(Weierstrass-form of an elliptic curve)
p is a primegt3, discriminant
The set of points on the
curve and the point of infinity O
has an additive group structure with identiy
element O.
The inverse of P (x,y) in E(GF(p)) is P
(x,-y). We have addition formula for computing
PQ for P,Q in E(GF(p)).
We set P O O P P and P (-P) O for
each E(GF(p)).
y2 x3 ax b is called the definition
equation. GF(p) is called the definition field.
a,b are called the coefficient of the curve.
7
Standard Formula
(Weierstraß-form of an elliptic curve)
Standard Formula
ECADD
ECDBL
8
Example
(Weierstraß-form of an elliptic curve)
a 1, b 6, p 11. E(1,6)/GF(11) O, (2,4),
(2,7), (3,5), (3,6), (5,2), (5,9),
(7,2), (7,9), (8,3), (8,8),
(10,2), (10,9)
ECADD (2,4) (10,9) ((r2 - x1 - x2), r(x1 -
x3) - y1) (3,5) r (y1-y2)/(x1
- x2) (9-4)/(10-2) mod 11 2 ECDBL 2(8,8)
(r2 - (x1 x1), r(x1 - x3) - y1) (7,2)
r (3x12 1)/(2y1) mod 11 10
9
ElGamal Encryption
p, a, b curve parameters of elliptic curve E
n the order of E (it is usually a prime
number) G generator of E, a secret exponent, A
aG in E.
p,a,b,G,A public key, a secret key, M
message in 0,1,2,,p-1.
Encryption choose ephemeral random r (0ltrltn)
C1 rG, C2 M x(rA) in E.
Decryption M C2 x(aC1)
x(P) is the x coordinate of point P (x,y),
namely x(P) x.
10
Scalar Multiplication
To compute
times
6 ECDBLs 2 ECADDs
99 ECADDs
Left-to-right binary method Q0 P for in-2
down to 0 Q0 ECDBL(Q0) if ki1 then
Q0 ECADD(Q0,P) return(Q0)
11
SECG (Standards for Efficient Cryptography Group)
secp160r1 p FFFFFFFF FFFFFFFF FFFFFFFF
FFFFFFFF 7FFFFFFF a FFFFFFFF FFFFFFFF FFFFFFFF
FFFFFFFF 7FFFFFFC b 1C97BEFC 54BD7A8B 65ACF89F
81D4D4AD C565FA45 x 4A96B568 8EF57328 46646989
68C38BB9 13CBFC82 y 23A62855 3168947D 59DCC912
04235137 7AC5FB32 n 01 00000000 00000000
0001F4C8 F927AED3 CA752257 h 01
http//www.secg.org/
12
Affine Coordinate
Addition formulae (ECADD, ECDBL) can be assembled
by the basic arithmetic of the base field GF(p).
ECADD Input x1, y1, x2, y2 Output x3, y3 1.
R1 x1 - x2 2. R2 y1 - y2 3. R3 R2-1 4.
R4 R3R2 5. R5 R4R4 6. R6 R5 - x1 7.
R7 R6 - x2 8. R8 x1 - R7 9. R9
R4R8 10. R10 r9 - y1 11. Return x3R7, y3R10
3 M 1 I
ECDBL requires 4 M 1 I.
13
How faster is ECC than RSA?
ECC chooses 160-bit prime p and secret scalar
d. The scalar multiplication requires 160 ECDBL
and 80 ECADD on average. Thus 160 (4M1I) 80
(3M1I) 880M240I 5,680M for I 20M.
RSA chooses 1024-bit modulus n and secret
exponent d. The modular exponentiation requires
1024 512 multiplication on average. Thus 1536
multiplications of 1024 bits, which is about
62,976M of 160 bits
due to (1 multiplications of 1024 bits)/(1
multiplication of 160 bits) 41.
160-bit ECC is about 10 times faster than
1024-bit RSA.