RSA Cryptosystem 1977 - PowerPoint PPT Presentation
1 / 16
Title:
RSA Cryptosystem 1977
Description:
RSA Cryptosystem (1977) p, q: primes, n = pq, ed = 1 mod (p-1)(q-1) ... Celeron 500MHz, LiDIA 2.0, TurboLinux 6.0. Novak Attack on RSA-CRT (We assume that q p) ... – PowerPoint PPT presentation
Number of Views:52
Avg rating:3.0/5.0
Title: RSA Cryptosystem 1977
1
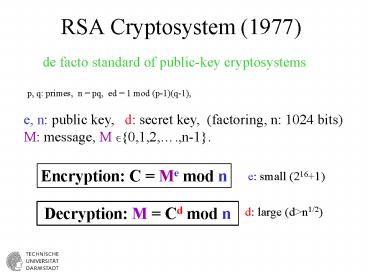
RSA Cryptosystem (1977)
de facto standard of public-key cryptosystems
p, q primes, n pq, ed 1 mod (p-1)(q-1),
e, n public key, d secret key, (factoring,
n 1024 bits) M message, M ?0,1,2,.,n-1.
Encryption C Me mod n
e small (2161)
Decryption M Cd mod n
d large (dgtn1/2)
2
RSA Decryption using Chinese Remainder Theorem
M Cd mod n
n
dp d mod (p-1) Mp Cdp mod p 8 times
faster
dq d mod (q-1) Mq Cdq mod q 8 times
faster
p
q
Garners algorithm
M Mp pv mod n, v (Mq - Mp) p-1 mod q
n
RSA decryption using the CRT can be computed
about 4 times faster than original decryption.
3
Who invented CRT?
Sun Zi (??), Master Suns Mathematical Manual
(????), in about 4th century AD. There are
certain things whose number is unknown.
Repeatedly divided by 3, the remainder is 2 by
5 the remainder is 3 and by 7 the remainder is
2. What will be the number?
Answer 23
http//www.math.sfu.ca/histmath/China/3rdCenturyBC
/STSC.html
4
Fast Factoring Algorithm
There are two types of fast factoring algorithms
to be considered (1) number field sieve
(NFS) - the fastest factoring algorithm,
and the running time is estimated by
the total bit size of the modulus n
(sub-exponential time Ln1/3). The
current fastest implementation record is 530-bit
modulus. (2) elliptic curve method (ECM)
- effective to find the small prime of n, and the
running time is estimated by the size of
the prime p (sub-exponential time Lp1/2).
The current fastest implementation record is
to find 183-bit prime. Other factoring
algorithms have the same or slower running time.
LNs,c exp((co(1)) logs(N) log log1-s(N))
5
Key size of n pqr
Multi-Prime RSA uses the modulus npqr instead of
npq.
256 299 341
768 896 1024
Bit size of prime factor
Bit size of modulus
261 267 273
277 282 288
ECM
NFS
Lp1/2, 21/2
Ln1/3,(64/9)1/3
Currently 1024-bit pq with 512-bit p, q is as
secure as 1024-bit pqr with 341-bit p, q , r.
6
Multi-Prime RSA with n pqr
M Cd mod n
n
dp d mod (p-1) Mp Cdp mod p 27 times
faster
dq d mod (q-1) Mq Cdq mod q 27 times
faster
dr d mod (r-1) Mr Cdr mod r 27 times
faster
p
q
r
Mpq Mp pv mod pq, v (Mq Mp) p-1 mod q
pq
M Mpq pqu mod n, u (Mr Mpq) (pq)-1 mod r
n
The decryption of Multi-Prime RSA can be computed
about 9 times faster than original decryption.
7
Multi-Prime RSA
Algorithm RSA_Decryption_CRT (npqr) Input
C,n,p,q,r,dp,dq,dr,p_inv_q,(pq)_inv_r Output M
1 Mp Cdp mod p Mq Cdq mod q Mr Cdr
mod r 2 v (Mq - Mp)p_inv_q mod q Mpq Mp
pv 3 u (Mr Mpq)(pq)_inv_r mod r M Mpq
pqu 4 Return M
PKCS 1, http//www.rsasecurity.com/rsalabs/pkcs/
8
http//www.rsasecurity.com/rsalabs/pkcs/pkcs-1/ind
ex.html
9
Multi-Exponent RSA with p2q
M Cd mod n
n
dp d mod (p-1) Mp Cdp mod p 27 times
faster
dq d mod (q-1) Mq Cdq mod q 27 times
faster
p
q
Hensel lifting
Mp2 M mod p2
p2
M Mp2 p2u mod n, u (Mq Mp2) (p2)-1 mod q
n
The decryption of Multi-Exponent RSA can be
computed about 13.5 times faster than original
decryption for small e.
10
Hensel Lifting
We can compute M mod p2 from M mod p very fast.
In order to obtain M mod p, we can compute Cdp
mod p, where dp d mod p-1
M mod p2 has p-adic representation M mod p2 M0
p M1, where M0 and M1 are unique mod p (M0 M
mod p).
C Me mod p2 (M0 p M1)e mod p2
M0e epM0e-1M1 mod p2.
Once M0 is known, we can compute M1 by
M1 A(eM0e-1)-1 mod p, A (C-M0e mod p2)/p.
This operation is independent from d, and it is
fast for small e.
11
Lifting without Inversion
A problem Hensel lifting has an inversion and a
division.
Let Xp pM1. We try to compute Xp instead of M1.
C (M0 Xp)e mod p2 M0e eM0e-1Xp mod
p2.
Xp (C-M0e) ((eM0e-1)-1 mod p) mod p2
(C-M0e) (e-1 mod p) (M01-e mod p) mod p2
(C-M0e) (e-1 mod p) (Cdp-1 mod p) mod p2
If we store Cdp-1 mod p during Cdp mod p, we need
no inversion. e-1 mod p is independent from the
ciphertext C, we precompute it.
12
Multi-Exponent RSA
Algorithm RSA_Decryption_CRT (np2q) Input
C,e,n,p,q,dp,dq,(p2)_inv_q, e_inv_p Output M 1
Mq Cdq mod q K Cdp-1 mod p A KC mod p
2 F Ae mod p2 E C - F mod p2 3 B
EK(e_inv_p) mod p2 A A B 4 v (Mq -
A)(p2)_inv_q mod q M A p2v 5 Return M
T.Takagi, Fast RSA-type Cryptosystems Modulo
pkq using Hensel Lifting, Crypto 98, LNCS
2274, LNCS 1462, pp.318-326, 1998. IEICE
Transactions, Vol.E87-A, No1, pp.94-100, 2004.
13
Comparison for 1024 bits
Secret key
Speed Original RSA 1024
bits 1 RSA-CRT
2560 bits 0.25 Multi-Prime RSA
2736 bits 0.11 Multi-Exponent RSA
2052 bits 0.078 (e2161)
Celeron 500MHz, LiDIA 2.0, TurboLinux 6.0
14
Novak Attack on RSA-CRT
Step 4
(We assume that qgtp) Algorithm RSA_Decryption_CRT
(npq) Input C,n,p,q,dp,dq,p_inv_q Output M 1
Mp Cdp mod p 2 Mq Cdq mod q 3 u Mq
Mp 4 if ult0 then u uq 5 v u
p_inv_q mod q 6 M Mp pv 7 Return M
Power Analysis can detect the sign of Step 4.
Thus we have the following oracle
if f(x) lt0, then O(x) 0, else O(x) 1, where
f(x) (x mod q) (x mod p).
Cited from the paper R.Novak, SPA-Based
Adaptive Chosen Ciphertext Attack on RSA
Implementation,'' PKC 2002, LNCS 2274,
pp.252-262, 2002.
15
A Countermeasure
A standard countermeasure is to randomize the
parameters.
Input c, p, q, dp, dq, p_inv_q Output m
1. generate random integer r in Z/nZ 2.
randomization t cre mod n 3. decryption u
RSA_CRT_Decryption(t,p,q,dp,dq,p_inv_q) 4.
remove randomization m u r-1 mod n 5. return
m.
Correctness u td (cre)d cd red m r mod
n. The ciphertext t to the decryption oracle is
randomized by r, and thus the attacker cannot
manipulate the size of ciphertext t.
Problem The overhead of re mod n, r-1 mod n is
large.
16
How to Eliminate r-1 mod n
Input c, p, q, dp, dq, p_inv_q, e, n Output
m 1. generate random integer r in Z/nZ 2.
randomization t rec mod n, s re-1 mod n 3.
compute u RSA_CRT_Decryption(t,p,q,dp-1,dq-1,p_i
nv_q) 4. remove randomization m usc mod n
5. return m.
Correctness usc td-1 sc (rec)d-1 sc
(r1-emc-1) sc m mod n.
the overhead is about 5 for e 2161 (about 20
multiplications).