Interrupts and Exceptions - PowerPoint PPT Presentation
1 / 19
Title:
Interrupts and Exceptions
Description:
... vectors, IDT, gates, PIC, APIC. Interrupt handling: data ... Possible to 'mask' interrupts at PIC or CPU. Early systems cascaded two 8 input chips (8259A) ... – PowerPoint PPT presentation
Number of Views:388
Avg rating:3.0/5.0
Title: Interrupts and Exceptions
1
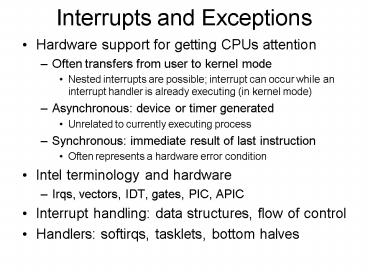
Interrupts and Exceptions
- Hardware support for getting CPUs attention
- Often transfers from user to kernel mode
- Nested interrupts are possible interrupt can
occur while an interrupt handler is already
executing (in kernel mode) - Asynchronous device or timer generated
- Unrelated to currently executing process
- Synchronous immediate result of last instruction
- Often represents a hardware error condition
- Intel terminology and hardware
- Irqs, vectors, IDT, gates, PIC, APIC
- Interrupt handling data structures, flow of
control - Handlers softirqs, tasklets, bottom halves
2
Basic Ideas
- Similar to context switch (but lighter weight)
- Hardware saves a small amount of context on stack
- Includes interrupted instruction if restart
needed - Execution resumes with special iret instruction
- Structure top and bottom halves
- Top-half do minimum work and return
- Bottom-half deferred processing
- Handler code executed in response
- Possible to temporarily mask interrupts
- Handlers need not be reentrant
- But other interrupts can occur, causing nesting
3
Interrupts vs Exceptions
- Varying terminology but for Intel
- Interrupt (synchronous, device generated)
- Maskable device-generated, associated with IRQs
(interrupt request lines) may be temporarily
disabled (still pending) - Nonmaskable some critical hardware failures
- Exceptions (asynchronous)
- Processor-detected
- Faults correctable (restartable) e.g. page
fault - Traps no reexecution needed e.g. breakpoint
- Aborts severe error process usually terminated
(by signal) - Programmed exceptions (software interrupts)
- int (system call), int3 (breakpoint)
- into (overflow), bounds (address check)
4
Vectors, IDT
- Vector index (0-255) into descriptor table (IDT)
- Special register idtr points to table (use lidt
to load) - IDT table of gate descriptors
- Segment selector offset for handler
- Descriptor Privilege Level (DPL)
- Gates (slightly different ways of entering
kernel) - Task gate includes TSS to transfer to (not used
by Linux) - Interrupt gate disables further interrupts
- Trap gate further interrupts still allowed
- Vector assignments
- Exceptions, NMI are fixed
- Maskable interrupts can be assigned as needed
5
PIC
- Programmable Interrupt Controller (PIC)
- chip between devices and cpu
- Fixed number of wires in from devices
- IRQs Interrupt ReQuest lines
- Single wire to CPU some registers
- PIC translates IRQ to vector
- Raises interrupt to CPU
- Vector available in register
- Waits for ack from CPU
- Other interrupts may be pending
- Possible to mask interrupts at PIC or CPU
- Early systems cascaded two 8 input chips (8259A)
6
Interrupt Handling Components
vector
IRQs
Memory Bus
0
PIC
CPU
IDT
0
INTR
idtr
15
Mask points
255
handler
7
IO-APIC, LAPIC
- Advanced PIC for SMP systems
- Used in all modern systems
- Interrupts routed to CPU over system bus
- IPI inter-processor interrupt
- Local APIC versus frontend IO-APIC
- Devices connect to front-end IO-APIC
- IO-APIC communicates (over bus) with Local APIC
- Interrupt routing
- Allows broadcast or selective routing of
interrupts - Need to distribute interrupt handling load
- Routes to lowest priority process
- Special register Task Priority Register (TPR)
- Arbitrates (round-robin) if equal priority
8
Intel Exceptions
- Architecture (processor) dependent
- Intel has about 20 (out of 32 possible)
- Most exceptions send signal to current process
- Default action often just kills process
- Page fault is the one exception very complex
handler - Some examples
- 0 SIGFPE Divide by zero error
- 3 SIGTRAP Breakpoint
- 6 SIGILL Invalid op-code
- 11 SIGBUS Segment not present
- 12 SIGBUS Stack overflow
- 13 SIGSEGV General protection fault (DPL
violation) - 14 SIGSEGV Page fault
9
Hardware Handling
- On entry
- Which vector?
- Get corresponding descriptor in IDT
- Find specified descriptor in GDT (for handler)
- Check privilege levels (CPL, DPL)
- If entering kernel mode, set kernel stack
- Save eflags, cs, (original) eip on stack
- - Jump to appropriate handler
- Assembly code prepares C stack, calls handler
- On return (i.e. iret)
- Restore registers from stack
- If returning to user mode, restore user stack
- Clear segment registers (if privileged selectors)
10
Nested Execution
- Interrupts can be interrupted
- By different interrupts handlers need not be
reentrant - No notion of priority in Linux
- Small portions execute with interrupts disabled
- Interrupts remain pending until acked by CPU
- Exceptions can be interrupted
- By interrupts (devices needing service)
- Exceptions can nest two levels deep
- Exceptions indicate coding error
- Exception code (kernel code) shouldnt have bugs
- Page fault is possible (trying to touch user
data)
11
IDT Initialization
- Initialized once by BIOS in real mode
- Linux re-initializes during kernel init
- Must not expose kernel to user mode access
- start by zeroing all descriptors
- Linux lingo
- Interrupt gate (same as Intel no user access)
- Not accessible from user mode
- System gate (Intel trap gate user access)
- Used for int, int3, into, bounds
- Trap gate (same as Intel no user access)
- Used for exceptions
12
Exception Handling
- Some exceptions push error code on stack
- IDT points to small individual handlers
(assembly) - handler_name pushl 0 // placeholder if no
error code pushl do_handler_name jmp
error_code - Common code sets up for C call
- Pops handler address from stack, calls
- All handlers check if kernel mode
- Exceptions caused by touching bad syscall params
- Return to userland with error code
- Other exceptions- die() // kernel Oops
- Most handlers just generate signal for current
- current-tss.error_code error_code
- current-tss.trap_no vector
- force_sig(sig_number, current)
13
Interrupt Handling
- More complex than exceptions
- Requires registry, deferred processing, etc.
- Some issues
- IRQs are often shared all handlers (ISRs) are
executed so they must query device - IRQs are dynamically allocated to reduce
contention - Example floppy allocates when accessed
- Three types of actions
- Critical Top-half (interrupts disabled
briefly!) - Example acknowledge interrupt
- Non-critical Top-half (interrupts enabled)
- Example read key scan code, add to buffer
- Non-critical deferrable Do it later
(interrupts enabled) - Example copy keyboard buffer to terminal handler
process - Softirqs, tasklets, bottom halves (deprecated)
14
IRQ, Vector Assignment
- PCI bus usually assigns IRQs at boot
- Vectors usually IRQ 32
- Below 32 reserved for non-maskable, execeptions
- Vector 128 used for syscall
- Vectors 251-255 used for IPI
- Some IRQs are fixed by architecture
- IRQ0 interval timer
- IRQ2 cascade pin for 8259A
- See /proc/interrupts for assignments
15
IRQ Data Structures
- irq_desc array of IRQ descriptors
- status (flags), lock, depth (for nested disables)
- handler PIC device driver!
- action linked list of irqaction structs
(containing ISRs) - irqaction ISR info
- handler actual ISR!
- flags
- SA_INTERRUPT interrupts disabled if set
- SA_SHIRQ sharing allowed
- SA_SAMPLE_RANDOM input for /dev/random entropy
pool - name for /proc/interrupts
- dev_id, next
- irq_stat per-cpu counters (for /proc/interrupts)
16
Interrupt Processing
- BUILD_IRQ macro generates
- IRQn_interrupt
- pushl n-256 // negative to distinguish syscalls
- jmp common_interrupt
- Common code
- common_interrupt
- SAVE_ALL // save a few more registers than
hardware - call do_IRQ
- jmp ret_from_intr
- do_IRQ() is C code that handles all interrupts
17
Low-level IRQ Processing
- do_IRQ()
- get vector, index into irq_desc for appropriate
struct - grab per-vector spinlock, ack (to PIC) and mask
line - set flags (IRQ_PENDING)
- really process IRQ? (may be disabled, etc.)
- call handle_IRQ_event()
- some logic for handling lost IRQs on SMP systems
- handle_IRQ_event()
- enable interrupts if needed (SA_INTERRUPT clear)
- execute all ISRs for this vector
- action-handler(irq, action-dev_id, regs)
18
Deferrable Functions
- Bottom-halves (deprecated)
- Old static array of function pointers that are
marked for execution (can be masked temporarily) - Executed on kernel to user transition
- Executed serially (globally) on SMP system
- Mostly for networking code
- Tasklets Different tasklets can execute
concurrently - Softirqs The same softirq can execute
concurrently - Layered implementation
- Bottom-halves implemented using tasklets
- Tasklets implemented using softirqs
- When executed? (pretty frequently)
- When last (nested) interrupt handler terminates
- When network packet receiver
- When idle per-cpu ksoftirqd kernel thread
- Lots of detail in book a bit complex
19
Return Code Path
- Interleaved assembly entry points
- ret_from_exception()
- ret_from_inr()
- ret_from_sys_call()
- ret_from_fork()
- See flowchart in text (Fig 4-5 page 158)
- Things that happen
- Run scheduler if necessary
- Return to user mode if no nested handlers
- Restore context, user-stack, switch mode
- Re-enable interrupts if necessary
- Deliver pending signals
- (Some DOS emulation stuff VM86 Mode)