SAP Security Interview Question and Answers in Chennai
Title:
SAP Security Interview Question and Answers in Chennai
Description:
SAP Security is providing correct access to business users with respect to their authority or responsibility and giving permission in keeping with their roles.list of SAP security training courses are provided by SAPVITS in Chennai. – PowerPoint PPT presentation
Number of Views:69
Title: SAP Security Interview Question and Answers in Chennai
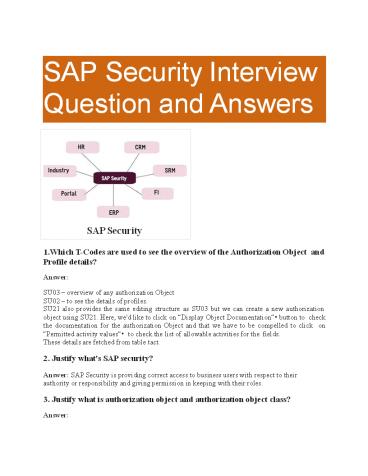
1
SAP Security Interview Question and Answers
- SAP Security
- Which T-Codes are used to see the overview of the
Authorization Object and Profile details? - Answer
- SU03 overview of any authorization Object SU02
to see the details of profiles. - SU21 also provides the same editing structure as
SU03 but we can create a new authorization - object using SU21. Here, we'd like to click on
Display Object Documentation button to check
the documentation for the authorization Object
and that we have to be compelled to click on
Permitted activity values to check the list
of allowable activities for the fields. - These details are fetched from table tact.
- Justify what's SAP security?
- Answer SAP Security is providing correct access
to business users with respect to their
authority or responsibility and giving permission
in keeping with their roles. - Justify what is authorization object and
authorization object class? - Answer
2
- Authorization Object Authorization objects are
teams of authorization field that regulates
specific activity. Authorization relates to
explicit action whereas Authorization field
relates for security administrators to assemble
specific values therein particular action. - Authorization object class Authorization object
comes under authorization object categories, and
that they are sorted by function area like
finance, accounting, HR, etc - Whats the basic difference in between SU22
SU24? - Answer
- SU22 displays and updates the values in tables
USOBT and USOBX, while SU24 does the same in
tables USOBT_C and USOBX_C. The _C stands for
Customer. The profile generator gets its
information from the _C tables. within the USOBT
and USOBX tables, the values are the SAP
standard values as shown in SU24. With SU25 one
will (initially) transfer the USOBT values to
the USOBT_C table. - Explain what is roles in SAP security?
- Answer Roles is referred to a group of
t-codes, which is assigned to execute the
particular business task. Each role in SAP
requires particular privileges to execute a
function in SAP that is called AUTHORIZATIONS. - Explain how you can delete various roles from
Production System, QA, and DEV? - Answer To delete various roles from Production
System, QA, and DEV you have to follow below
steps - Place the roles to be deleted in a transport (in
DEV) - Delete the roles
- Push the transport through to QA and production
- 7. What authorization is required to create
and maintain user master records? - Answer The following authorization objects are
required to create and maintain user master
records - S_USER_GRP User Master Maintenance Assign user
groups - S_USER_PRO User Master Maintenance Assign
authorization profile
3
4. A Reference user is sort of a general,
non-personally connected, client, a System user.
further authorizations are often allotted within
the system employing a reference user. A
reference user for added rights is often
assigned to every user within the Roles tab. 8.
How to remove duplicate roles with different
start and end date from user master? Answer You
can use PRGN_COMPRESS_TIMES to do this.
Vintage IT Solutions provide SAP Online Training
in Hyderabad, India. SAPVITS have an excellent
facility for training. We provide Individual and
Corporate training.SAPVITS provides Server
Access Services. We provide SAP Remote Access and
SAP Ides Access Services. We also provide SAP
Security Training in Chennai, SAP Simple Finance
Online Training SAP FIORI Training in Pune, SAP
Simple Logistics Online Training, SAP FICO
Training in Noida, SAP BASIS Online Training, SAP
SD Training in Delhi etc. Contact us Website
http//www.sapvits.com/ Email id
info_at_sapvits.com IND 91 992 284 8898 USA 1
678 389 8898 UK 44 141 416 8898