Secure xADL - PowerPoint PPT Presentation
1 / 2
Title: Secure xADL
1
Software Architecture with Security
Secure xADL
principals, privileges, and contexts. Such
constructs enable describing security contracts
of components. Connectors are used to form secure
composites. Our approach supports good security
practices at the architecture level, and provides
tools to support design, analysis, and execution
of secure software. A principal is the user on
whose behalf software executes. Principal is a
key concept in the security community, but it is
missing from traditional software architectures.
We extend the basic component and connector
constructs with the principal for which they
perform, enabling architectural
Motivation Highly networked and componentized
modern software poses significant challenges to
assuring its security. Traditional security
research mostly focuses on formally assuring
monolithic software and low-level supporting
mechanisms. A more comprehensive perspective is
needed to deal with the challenges of modern
software. Traditional software architecture
research provides such a perspective on
decentralized and networked software, but lacks
support for specific properties like securities.
design and analysis based on different security
principals defined by software architects.
Privileges describe what components can do
depending on the executing principals. We model
two types of privileges. The first type handles
the traditional resource access control, such as
which principal has read/write access to which
files. The second type includes architecturally
important privileges, such as execution, creation
and removal of new architectural components,
reading and writing of architecturally critical
information.
We need a solution that can help us design,
analyze, and execute software that is made up of
components coming from and running at different
sources with security as a major concern. Such a
solution enables developers and administrators to
design and maintain secure software. Such a
solution gives them the power to adopt
security-aware design, identify potential
problems, and effectively respond to
attacks. Hypotheses Traditional security
research does not provide a high-level
perspective on the software architecture of a
system.
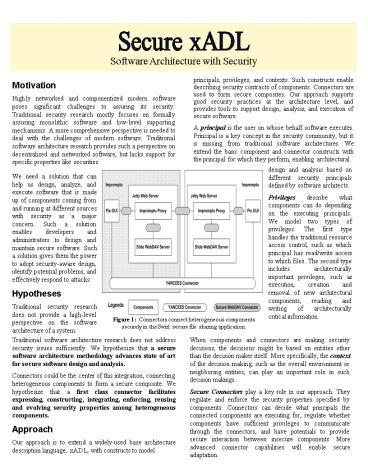
Figure 1 Connectors connect heterogeneous
components securely in the Swirl secure file
sharing application.
When components and connectors are making
security decisions, the decisions might be based
on entities other than the decision maker itself.
More specifically, the context of the decision
making, such as the overall environment or
neighboring entities, can play an important role
in such decision makings. Secure Connectors play
a key role in our approach. They regulate and
enforce the security properties specified by
components. Connectors can decide what principals
the connected components are executing for,
regulate whether components have sufficient
privileges to communicate through the connectors,
and have potentials to provide secure interaction
between insecure components. More advanced
connector capabilities will enable secure
adaptation.
Traditional software architecture research does
not address security issues sufficiently. We
hypothesize that a secure software architecture
methodology advances state of art for secure
software design and analysis. Connectors could
be the center of this integration, connecting
heterogeneous components to form a secure
composite. We hypothesize that a first class
connector facilitates expressing, constructing,
integrating, enforcing, reusing and evolving
security properties among heterogeneous
components. Approach Our approach is to extend a
widely-used base architecture description
language, xADL, with constructs to model
2
ltcomponent type"ProxyType" id"Local"gt
ltprincipalgtMelt/principalgt lt/componentgt ltcomponent
type"ProxyType" id"Remote"gt
ltprincipalgtOtherlt/principalgt lt/componentgt ltcompone
nt type"GUIType" id"GUI"gt
ltprincipalgtMelt/principalgt lt/componentgt ltcomponent
type"SlideType" id"Slide"gt
ltprincipalgtMelt/principalgt lt/componentgt ltconnector
type"SecureWebDAVConnector"
id"GUI_Impromptu"gt ltinterface
signature"WebDAVClient" id"GUI"/gt
ltinterface signature"WebDAVServer"
id"Impromptu"/gt lt/connectorgt ltconnector
type"SecureWebDAVConnector" id"Impromptu_Impro
mptu"gt ltinterface signature"WebDAVClient"
id"Remote"/gt ltinterface
signature"WebDAVServer"
id"Local"/gt lt/connectorgt ltconnector
type"SecureWebDAVConnector"
id"Impromptu_Slide"gt ltinterface
signature"WebDAVClient" id"Local"/gt
ltinterface signature"WebDAVServer"
id"Slide"/gt lt/connectorgt
Case Study Swirl Swirl is a file sharing
application enabling ad-hoc groups to work
collaboratively. The system is based on industry
standards such as HTTP and WebDAV. The system
consists of a proxy that routes between a local
repository and other remote proxies, and a GUI
that accesses the proxy. The secure WebDAV
connector combines three more primitive
connectors the Digest Authentication connector,
the HTTP method authorization connector, and the
WebDAV ACL authorization connector. The combined
connectors enforce different levels of file
access semantics. The file access control
decisions are made based on the context and
principals of the requesting components. For
example, a proxy that acts on behalf of the local
user can perform arbitrary operations on shared
files. A remote proxy that acts on behalf of
another remote user can only modify local files
that are shared as read/write files. A
modification request on a read-only file is
rejected by the secure connector.
ltconnectorType id"DigestAuthenticationConnecto
r"gt lt/connectorTypegt ltconnectorType
id"WebXMLAuthorizationConnector"gt lt/connectorType
gt ltconnectorType id"WebDAVACLConnector"gt lt/con
nectorTypegt ltconnectorType id"SecureWebDAVConn
ector"gt ltsubArchitecturegt ltsequencegt
ltconnector type "DigestAuthenticationConne
ctor"/gt ltconnector type
"WebXMLAuthorizationConnector"/gt ltconnector
type "WebDAVACLConnector"/gt
lt/sequencegt lt/subArchitecturegt lt/connectorTypegt
Figure 3, Secure xADL description of Swirl
On going work We are extending our existing
architectural development environment,
ArchStudio, with a set of tools that enables
designating security principals, specifying
relevant privileges, analyzing conformances, and
signifying any violations. These tools will help
architects to embody best secure software
engineering practices. We are also investigating
two more significant case studies, one for the
distributed Web Service related protocols, and
another one for the security architecture of the
FireFox browser.
Figure 2, A composite connector type combines
authentication and authorization connector types
Contact Information Jie Ren Professor Richard
Taylor Institute for Software Research University
of California Irvine, California 92697-3425 jie,
taylor_at_ics.uci.edu 1-949-824-2776, 6429 Fax
949-824-1715
To learn more about the Swirl project, please
visit the website http//isr.uci.edu/projects/swi
rl/
This material is based upon work sponsored by the
National Science Foundation under grant number
0326105 and by the Intel Corporation. The content
of the work should not be interpreted as
necessarily representing the official policies or
endorsements, either expressed or implied, of
either organization.
June 2005