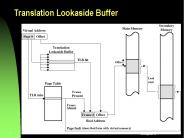
Lookaside PowerPoint PPT Presentations
All Time
Recommended
Page Tables and Virtual Memory Page tables can be very large (32 ... Natural unit for protection purposes No internal fragmentation Disadvantage: ...
| PowerPoint PPT presentation | free to download
An array of page table entries, indexed by virtual page number ... Worst of both worlds, pretty much never used. 11/11/09. 22. Virtually Addressed, Physically Tagged ...
| PowerPoint PPT presentation | free to view
Page size is a power of two typical size is 4kbytes ... the Translation Lookaside Buffer that is overwritten by the allocation itself. ...
| PowerPoint PPT presentation | free to download
First copy all our shell code to a known location ... Zero area will serve as good empty Lookaside space. If Lookaside is remapped over non zero area, we need ...
| PowerPoint PPT presentation | free to view
... still can't find any free entry, extend heap as ... If the chunk 1K and the lookaside is full, put it on the free list ... Heap header cookie calculation ...
| PowerPoint PPT presentation | free to view
Title: Memory Management Author: Mario Marchand Last modified by: hawkey Created Date: 9/19/1996 3:07:26 PM Document presentation format: On-screen Show
| PowerPoint PPT presentation | free to download
Title: Reliable Windows Heap Exploits Author: Ohorovitz Last modified by: blah Created Date: 3/25/2004 6:59:27 AM Document presentation format: On-screen Show
| PowerPoint PPT presentation | free to download
Operating Systems CMPSCI 377 Lecture 2: OS & Architecture Emery Berger University of Massachusetts, Amherst
| PowerPoint PPT presentation | free to download
What we will learn from chapter ? 2. Introduction 3. Moving From An MPU To An MMU 4. ... // Cache and write buffer attribute unsigned int pAddress; ...
| PowerPoint PPT presentation | free to view
If size = 512K, virtual memory is used (not on heap) If 1K, ... Requested size is 1K (to fit the table) ... We must be the first one to allocate that size ...
| PowerPoint PPT presentation | free to view
UT HEAPS. HEAPS ABO. Windows 2003. Windows 2003 SP2. Still most widely used windows server OS ... Still not a lot of heap exploits released. Still not a lot of ...
| PowerPoint PPT presentation | free to view
memory images kept in secondary storage; ... 1-KB subpages for 4-Kbyte pages. Separate instruction and data MMUs. Can be disabled separately ...
| PowerPoint PPT presentation | free to view
Virtual Memory Chapter 8
| PowerPoint PPT presentation | free to download
Energy Efficiency and Storage Flexibility in the Blue File System Edmund B Nightingale Jason Flinn University of Michigan
| PowerPoint PPT presentation | free to view
Energy Efficiency and Storage Flexibility in the Blue File System ... Sobti et al] Cooperative I/O ... Kernel Intercepts Linux VFS calls Communicates with ...
| PowerPoint PPT presentation | free to download
Review CPSC 321 Andreas Klappenecker Announcements Tuesday, November 30, midterm exam Cache Placement strategies direct mapped fully associative set-associative ...
| PowerPoint PPT presentation | free to download
Virtual Memory. Shaheen Gandhi. e-mail: sgandhi@andrew.cmu.edu. Office Hours: ... Virtual Memory and Caches are two separate things, but they draw on the same ideas ...
| PowerPoint PPT presentation | free to download
program relocation. protection. Pages: virtual memory blocks ... have test programs that exercise all instruction. have a full report that explains your design ...
| PowerPoint PPT presentation | free to download
Applications for arbitrary memory overwrite exploitation demos ... DCOM (seems to be the inflection point), Messenger, MSMQ, Script Engine ...
| PowerPoint PPT presentation | free to view
Allocating Memory Ted Baker Andy Wang CIS 4930 / COP 5641
| PowerPoint PPT presentation | free to download
Title: CSE 431. Computer Architecture Subject: Lecture 19 Author: Janie Irwin Last modified by: chi Created Date: 8/19/1997 4:58:46 PM Document presentation format
| PowerPoint PPT presentation | free to view
Title: Cache writes and examples Subject: CS232 @ UIUC Author: Howard Huang Description 2001-2003 Howard Huang Last modified by: cse Created Date
| PowerPoint PPT presentation | free to download
Mondriaan Memory Protection Emmett Witchel Krste Asanovic MIT Lab for Computer Science
| PowerPoint PPT presentation | free to download
CSCI 4717/5717 Computer Architecture Topic: Memory Management Reading: Stallings, Sections 8.3 and 8.4 Recursion Many complex algorithmic functions can be broken into ...
| PowerPoint PPT presentation | free to download
2. Memory may contain parts of program which are not used during a run (ie. ... Catenate. Virtual memory address. Ceng 334 - Operating Systems. 3.2-15 ...
| PowerPoint PPT presentation | free to download
Page table overhead increases with address space size. Page tables get too big to fit in memory! ... Many peta-bytes per process page table. Inverted page tables ...
| PowerPoint PPT presentation | free to download
memset(dptr- data[s_pos], 0, scullc_quantum); To release memory. for (i = 0; i qset; i ) ... memset(dptr- data[s_pos], 0, PAGE_SIZE dptr- order); A scull ...
| PowerPoint PPT presentation | free to download
Operating Systems Memory management
| PowerPoint PPT presentation | free to download
Mikhail Chupilko, Alexander Kamkin, and Dmitry Vorobyev. Institute for System ... the creation of specifications and tests for Verilog designs using CTESK ...
| PowerPoint PPT presentation | free to download
Models of Desktop Portability. Laptops. Roaming profiles. Remote desktop. Laptops. Laptops are ... Fingerprint for every 16K chunk in remote virtual disk ...
| PowerPoint PPT presentation | free to download
(no is serijas nak nosaukums 'Big Blue', i ir daudz gan zagta, gan ' ... 1. Modules that were loaded under the current task (LLEs) 2. The job pack area (JPA) ...
| PowerPoint PPT presentation | free to view
Wolverine. Linux Kernel. Linux File Cache. USBStick ... Communicates with Wolverine through pseudo-device driver ... Operations redirected to Wolverine ...
| PowerPoint PPT presentation | free to view
The task of subdividing the user area is carried out dynamically by the OS -- memory management ... is divided in segments and loaded in dynamic partitions ...
| PowerPoint PPT presentation | free to download
Simple Batch Systems. Resident Monitor program. Users submit jobs to operator. Operator batches jobs. Monitor controls sequence of events to process batch ...
| PowerPoint PPT presentation | free to download
time 0 1 2 3 4 5 6 7 8 9 10. 11/28/09. CHAPTER 8. 13. FIFO ... Processor Utilization. Value L /S = 1. CPU. 11/28/09. CHAPTER 8. 20. FIGURE 8-12. Lifetime Curve ...
| PowerPoint PPT presentation | free to view
Use PC to get VIRTUAL address. Lookup VIRTUAL address in TLB. MISS OS Trap ... Virtual Address Translation. 11/16/09. Comp 120 Fall 2001. 6. 16k direct-mapped cache ...
| PowerPoint PPT presentation | free to download
The flow obeys Darcy's Law. Two-dimensional. Steady state. 6. Mathematical formulation. Darcy's Law: Potential Function: Velocity Components: Continuity Equation: ...
| PowerPoint PPT presentation | free to download
Fast & data sharing is convenient. ... Placing every possibly shared data on its own page is very difficult. ... protection and data sharing. MMP uses linear ...
| PowerPoint PPT presentation | free to download
Not always (small segments may transfer ... Second-chance. Clock. Least recently used (and variants of it) Random. Ageing. Not recently used ... Second-chance ...
| PowerPoint PPT presentation | free to view
DRAM is too slow for many purposes. Compromise. Build a memory hierarchy. Locality ... compromise between the two extremes above. Cache Types. Set Associative Caches ...
| PowerPoint PPT presentation | free to download
Memory Management Fundamentals Virtual Memory ...
| PowerPoint PPT presentation | free to download
Title: Main Tasks Author: Winnie IDA Last modified by: Gert Jervan, ESLAB/SaS/IDA, Link pings Universitet Created Date: 8/31/1998 10:45:28 AM Document presentation ...
| PowerPoint PPT presentation | free to view
Primitive operating systems (such as MS- DOS and CP/M) provide some interfaces ... (b) Best-Fit Strategy. Place job in the smallest possible hole in which it will fit. ...
| PowerPoint PPT presentation | free to download
Memory Hierarchy Page 520 The technology we used to build our memory hierarchy can be divided into ...
| PowerPoint PPT presentation | free to download
huge miss penalty, thus pages should be fairly large (e.g., 4KB) ... Nightmare Scenario: ping pong effect! Capacity Misses: increase cache size. Cache Design Space ...
| PowerPoint PPT presentation | free to download
Title: 08 Operating System Support Author: Adrian J Pullin Last modified by: lcrum Created Date: 4/23/1999 3:59:55 PM Document presentation format
| PowerPoint PPT presentation | free to download
Project 4: Interfacing GNU debugging tool with on-board emulator (Komodo) ... debugging tool with on-board emulator program to facilitate source-level ...
| PowerPoint PPT presentation | free to download
Impact of Java Compressed Heap on Mobile/Wireless Communication ... as of a Jar file: eliminate redundancy) 2. Java bytecode factorization [Clausen et al.'00] ...
| PowerPoint PPT presentation | free to view
Each MULTICS program has a segment table, with one descriptor per segment. ... Conversion of a 2-part MULTICS address into a main memory address ...
| PowerPoint PPT presentation | free to view
Identify the race condition in this version of the consumer/producer problem. ... The race condition occurs when the variable out is accessed since this is now ...
| PowerPoint PPT presentation | free to download
one to fetch the page table. one to fetch the data ... Fetch Policy. Fetch Policy. Determines when a page should be brought into memory ...
| PowerPoint PPT presentation | free to download
Current Systems have only a couple rings of protection ... Protection Check in Parallel with Standard Pipeline ... to represent the delays for protection lookup ...
| PowerPoint PPT presentation | free to download
Miss penalty 40 cycles for all misses ... huge miss penalty, thus pages should be fairly large (e.g., 4KB) ... Incredible high penalty for a page fault ...
| PowerPoint PPT presentation | free to download
Bring photo id. Write name on all answer books. Closed book. Closed notes. ... If in doubt, make an assumption and write it down. Be concise. ...
| PowerPoint PPT presentation | free to view
Explorer 20MB. 40 More Processes! Page the page tables! Have to look up ... 8. What is in the page table? Address = upper bits of physical memory address OR ...
| PowerPoint PPT presentation | free to download
Want to also avoid internal fragmentation. This is when memory is handed out in some fixed way ... Section09-Memory_Management Author: JB Last modified by:
| PowerPoint PPT presentation | free to view