Addressing mode summary - PowerPoint PPT Presentation
Title:
Addressing mode summary
Description:
Some computers, like this old Apple II, have one-address instructions. ... HP calculators and their 'reverse Polish notation' use a stack. ... – PowerPoint PPT presentation
Number of Views:66
Avg rating:3.0/5.0
Title: Addressing mode summary
1
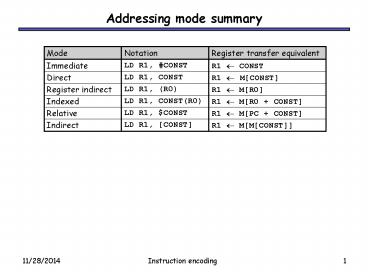
Addressing mode summary
2
Issues in design of ISAs
- Characterization of application programs
- What are typical programs like
- What mix of instructions (ALU, Branch, ..)
- Size of instruction word
- Length of program
- Number of instructions
- Number of bytes
- Number of instructions needed to code the same
program may be different depending on the ISA - Clock period
- Needs to be long enough to do one cycle of
instruction - Single cycle instruction or multi-cycle
instruction - Multi-cycle instructions (we are skipping this)
- Hardwired control vs micro-programmed control
- Pipelined instructions
3
Number of operands
- Another way to classify instruction sets is
according to the number of operands that each
data manipulation instruction can have. - Our example instruction set had three-address
instructions, because each one had up to three
operandstwo sources and one destination. - This provides the most flexibility, but its also
possible to have fewer than three operands.
4
Two-address instructions
- In a two-address instruction, the first operand
serves as both the destination and one of the
source registers. - Some other examples and the corresponding C code
- ADD R3, 1 R3 ? R3 1 R3
- MUL R1, 5 R1 ? R1 5 R1 5
- NOT R1 R1 ? R1 R1 R1
5
One-address instructions
- Some computers, like this old Apple II, have
one-address instructions. - The CPU has a special register called an
accumulator, which implicitly serves as the
destination and one of the sources. - Here is an example sequence which increments
MR0 - LD (R0) ACC ? MR0
- ADD 1 ACC ? ACC 1
- ST (R0) MR0 ? ACC
6
The ultimate zero addresses
- If the destination and sources are all implicit,
then you dont have to specify any operands at
all! - For the ALU instructions
- This is possible with processors that use a stack
architecture. - HP calculators and their reverse Polish
notation use a stack. - The Java Virtual Machine is also stack-based.
- How can you do calculations with a stack?
- Operands are pushed onto a stack. The most
recently pushed element is at the top of the
stack (TOS). - Operations use the topmost stack elements as
their operands. Those values are then replaced
with the operations result.
7
Stack architecture example
- From left to right, here are three stack
instructions, and what the stack looks like after
each example instruction is executed. - This sequence of stack operations corresponds to
one register transfer instruction - TOS ? R1 R2
PUSH R1 PUSH R2 ADD
8
Data movement instructions
- Finally, the types of operands allowed in data
manipulation instructions is another way of
characterizing instruction sets. - So far, weve assumed that ALU operations can
have only register and constant operands. - Many real instruction sets allow memory-based
operands as well. - Well use the books example and illustrate how
the following operation can be translated into
some different assembly languages. - X (A B)(C D)
- Assume that A, B, C, D and X are really memory
addresses.
9
Register-to-register architectures
- Our programs so far assume a register-to-register,
or load/store, architecture, which matches our
datapath from last week nicely. - Operands in data manipulation instructions must
be registers. - Other instructions are needed to move data
between memory and the register file. - With a register-to-register, three-address
instruction set, we might translate X (A B)(C
D) into
LD R1, A R1 ? MA // Use direct addressing LD
R2, B R2 ? MB ADD R3, R1, R2 R3 ? R1 R2 // R3
MA MB LD R1, C R1 ? MC LD R2, D R2 ?
MD ADD R1, R1, R2 R1 ? R1 R2 // R1 MC
MD MUL R1, R1, R3 R1 ? R1 R3 // R1 has the
result ST X, R1 MX ? R1 // Store that into MX
10
Memory-to-memory architectures
- In memory-to-memory architectures, all data
manipulation instructions use memory addresses as
operands. - With a memory-to-memory, three-address
instruction set, we might translate X (A B)(C
D) into simply - How about with a two-address instruction set?
ADD X, A, B MX ? MA MB ADD T, C, D MT ?
MC MD // T is temporary storage MUL X, X,
T MX ? MX MT
MOVE X, A MX ? MA // Copy MA to MX
first ADD X, B MX ? MX MB // Add
MB MOVE T, C MT ? MC // Copy MC to
MT ADD T, D MT ? MT MD // Add MD MUL
X, T MX ? MX MT // Multiply
11
Register-to-memory architectures
- Finally, register-to-memory architectures let the
data manipulation instructions access both
registers and memory. - With two-address instructions, we might do the
following
LD R1, A R1 ? MA // Load MA into R1
first ADD R1, B R1 ? R1 MB // Add MB LD
R2, C R2 ? MC // Load MC into R2 ADD R2, D R2
? R2 MD // Add MD MUL R1, R2 R1 ? R1
R2 // Multiply ST X, R1 MX ? R1 // Store
12
Size and speed
- There are lots of tradeoffs in deciding how many
and what kind of operands and addressing modes to
support in a processor. - These decisions can affect the size of machine
language programs. - Memory addresses are long compared to register
file addresses, so instructions with memory-based
operands are typically longer than those with
register operands. - Permitting more operands also leads to longer
instructions. - There is also an impact on the speed of the
program. - Memory accesses are much slower than register
accesses. - Longer programs require more memory accesses,
just for loading the instructions! - Most newer processors use register-to-register
designs. - Reading from registers is faster than reading
from RAM. - Using register operands also leads to shorter
instructions.
13
Summary
- Instruction sets can be classified along several
lines. - Addressing modes let instructions access memory
in various ways. - Data manipulation instructions can have from 0 to
3 operands. - Those operands may be registers, memory
addresses, or both. - Instruction set design is intimately tied to
processor datapath design.