5a1 - PowerPoint PPT Presentation
1 / 44
Title:
5a1
Description:
0 0 not saw by dest. 1 0 saw but did not copy. 1 1 saw and copied. JK1JK1I E. FS. 5a-13 ... Dual counter-rotating rings. 100 Mbps on optical fibers. Up to 500 nodes ... – PowerPoint PPT presentation
Number of Views:48
Avg rating:3.0/5.0
Title: 5a1
1
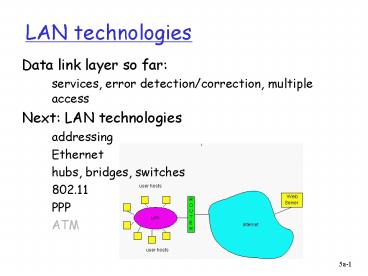
LAN technologies
- Data link layer so far
- services, error detection/correction, multiple
access - Next LAN technologies
- addressing
- Ethernet
- hubs, bridges, switches
- 802.11
- PPP
- ATM
2
Ethernet
- dominant LAN technology
- cheap 20 for 100Mbs!
- first widely used LAN technology
- Simpler, cheaper than token LANs and ATM
- Kept up with speed race 10, 100, 1000 Mbps
Metcalfes Ethernet sketch
3
Ethernet Frame Structure
- Sending adapter encapsulates IP datagram (or
other network layer protocol packet) in Ethernet
frame - Preamble
- 7 bytes with pattern 10101010 followed by one
byte with pattern 10101011 - used to synchronize receiver, sender clock rates
4
Ethernet Frame Structure (more)
- Addresses 6 bytes
- if adapter receives frame with matching
destination address, or with broadcast address
(eg ARP packet), it passes data in frame to
net-layer protocol - otherwise, adapter discards frame
- Type indicates the higher layer protocol, mostly
IP but others may be supported such as Novell IPX
and AppleTalk) - CRC checked at receiver, if error is detected,
the frame is simply dropped
5
Unreliable, connectionless service
- Connectionless No handshaking between sending
and receiving adapter. - Unreliable receiving adapter doesnt send acks
or nacks to sending adapter - stream of datagrams passed to network layer can
have gaps - gaps will be filled if app is using TCP
- otherwise, app will see the gaps
6
Ethernet uses CSMA/CD
- No slots
- adapter doesnt transmit if it senses that some
other adapter is transmitting, that is, carrier
sense - transmitting adapter aborts when it senses that
another adapter is transmitting, that is,
collision detection
- Before attempting a retransmission, adapter waits
a random time, that is, random access
7
Ethernet CSMA/CD algorithm
- 1. Adaptor gets datagram from and creates frame
- 2. If adapter senses channel idle, it starts to
transmit frame. If it senses channel busy, waits
until channel idle and then transmits - 3. If adapter transmits entire frame without
detecting another transmission, the adapter is
done with frame !
- 4. If adapter detects another transmission while
transmitting, aborts and sends jam signal - 5. After aborting, adapter enters exponential
backoff after the mth collision, adapter chooses
a K at random from 0,1,2,,2m-1. Adapter waits
K512 bit times and returns to Step 2
8
Ethernets CSMA/CD (more)
- Jam Signal make sure all other transmitters are
aware of collision 48 bits - Bit time .1 microsec for 10 Mbps Ethernet for
K1023, wait time is about 50 msec
- Exponential Backoff
- Goal adapt retransmission attempts to estimated
current load - heavy load random wait will be longer
- first collision choose K from 0,1 delay is K
x 512 bit transmission times - after second collision choose K from 0,1,2,3
- after ten collisions, choose K from
0,1,2,3,4,,1023
See/interact with Java applet on AWL Web
site highly recommended !
9
Ethernet Technologies 10Base2
- 10 10Mbps 2 under 200 meters max cable length
- thin coaxial cable in a bus topology
- repeaters used to connect up to multiple segments
- repeater repeats bits it hears on one interface
to its other interfaces physical layer device
only! - has become a legacy technology
10
10BaseT and 100BaseT
- 10/100 Mbps rate latter called fast ethernet
- T stands for Twisted Pair
- Nodes connect to a hub star topology 100 m
max distance between nodes and hub - Hubs are essentially physical-layer repeaters
- bits coming in one link go out all other links
- no frame buffering
- no CSMA/CD at hub adapters detect collisions
- provides net management functionality
11
Gbit Ethernet
- use standard Ethernet frame format
- allows for point-to-point links and shared
broadcast channels - in shared mode, CSMA/CD is used short distances
between nodes to be efficient - uses hubs, called here Buffered Distributors
- Full-Duplex at 1 Gbps for point-to-point links
- 10 Gbps now !
12
IEEE 802.5
- Frame format
- Token format
Extra PHY encoding
1 1 1 2-6
2-6 gt 8182 4 1
1
SD
FC
Dest. Addr
Data
Source Addr
FCS
ED
AC
FS
I bit Last frame
E bit Error
JK1JK1I E
SD
AC
ED
A C (d_Addr match, Copy) 0 0 not saw by
dest. 1 0 saw but did not copy 1 1 saw and
copied
Token bit Commands
13
Token Ring
- Physical Topology Ring
- 1 bit copy and send ? 1 bit delay
- (broadcast but different from bus that the
next station could not see the new incoming bit
receive from the previous station)
A send 10011
1
0
A
10
1001
D
B
100
1
0
C
14
Token Ring
- Priority Control
- Every station who want to transmit data must
- Set priority bit (0,2,4,6) in a rotating frame
header (or token) according to the highest
priority nonempty queue if its priority is more - Set Reservation bit
- Next Token holding station must check the
priority bit of the arrival token - Hold the token and Send a frame if it has a
data frame with priority more or equal to the
arrival token - Pass the Token to its successor if its
priority is less - Problem May cause Starving Station
15
Token Ring
- Transmission
- A station can send frames when a token is
received - Receive
- Set A and C bit in FS (Frame Status) field
and I bit in end delimiter instead of send ACK
and NAK frame (cheaper) - Token Passing
- No need to set the successor address in a token
- (order by sequence in the Physical Loop)
16
Token Ring
- Centralized Control
- Monitor Station (plus a Stand-by Monitor
Station) - Monitor Function
- Investigate Token passing
- Maintain Ring-turnaround time
- Destroy damaged frame and un-received frame
- Fix the broken ring
- Stand-by Monitor Function
- Investigate Token passing
- Investigate AMP (Active Monitor Present)
17
Token Ring
- Ring Turnaround Time
- Link of a Ring must capable to hold a total
token size at a time - Token Size 3 byte 24 bit
- Link transmission rate 10 Mbps
- Length of Link 200 meters
- Number of station 10 stations
- Token time 24 / 10 Mbps ? 2.4 microsecond
- Link Latency 200 / (2 x 108) ? 1 microsecond
- So 1 bit delay at each station must be more
than - (2.4 1) / 10 ? 0.14 microsecond
18
Token Ring
- Ring initialization
- First ready station send DAT (Duplicate Address
Test) - Return DAT has bit A 1 inform network
management sublayer to solve duplicated address - Return DAT has bit A 0 become a monitor
- Send SMP (Stand-by Monitor Present) to find
next active station to become stand-by monitor - The next down-stream station record monitor
address as UNA (Up-stream Neighbor Address) and
send its address in the SMP - Monitor record stand-by monitor address and
generate a Token
19
Token Ring
- Stand-by Monitor
- Monitor AMP
- If not found in ?t Send Claim_Token
- If CT with matched source address is returned
- Become a Monitor, and re-initialize the ring by
sending Purge - (and wait for returned Purge with matched
source address) - Send an AMP (the successor become stand-by M)
- Generate a Token
- If CT with un-matched source address is
returned - Let the Higher Address station become a monitor
- And return to stand-by monitor state
20
Token Ring
- Broken Cable
- A Station who could not see a token (or frame)
for a long period become a B_station - B_station continuously send Beacon frame
- If a Beacon with matched source address return
means Problem is cleared and B_station enter
claim_token state - If a Beacon with un-matched source address
return means Problem is cleared and B_station
enter stand-by monitor state - If nothing return notify the network management
sublayer
21
Token Ring
- Fix the broken ring
- Fix by wire center or Trunk Coupling Unit (TCU )
- In case of TCU Must have redundant ring
(stand-by)
A
B
C
TCU
Wire Center
F
G
D
E
22
Token Ring
- Fix the broken ring by wire center
A
B
C
Wire center bypass E
F
G
D
E
23
Token Ring
- Fix the broken ring by TCU
C and B re-config TCU
A
B
C
F
G
D
E
24
Token Ring
- Faulty Station
A
B
C
BYPASS C
F
G
D
E
25
IEEE 802.4
- Token Bus
- Physical Topology Bus, Tree
- Logical Topology Ring
- Algorithm Token Passing
- Distributed Management
- QoS Management (Integrated data service)
26
IEEE 802.4
- Frame format
- Token format
Extra PHY encoding
gt 1 1 1 2-6
2-6 gt 8182 4 1
Preamble
SD
FC
Dest. Addr
Data
Source Addr
FCS
ED
JK0JK000
JK1JK111
Preamble
SD
FC
ED
Dest. Addr
Source Addr
Frame types Commands
27
Token Passing
- Transmission
- Station must have a token
- Station could send n frames in a Token Holding
Time and or under priority control - Frames could be served up to its queue priority
- Station must send a token to its successor
station when - All data was sent
- Timeout Token holding Time
- No time left for low priority
frame in this turn
28
Token Passing
- Receiving
- Copy a frame which its address is matched to the
destination address - Send an ACK frame if the indicator bit was set
- (ACK service)
29
Token Bus
- Priority Control
- Token bus uses priority control to prevent
low-priority data sending while there are much
high priority data wait to send around the ring - High priority data are limited by MHT Maximum
High priority Time - Low priority data are limited by MLWT Maximum
Low priority Waiting Time
30
Priority Control Algorithm (token bus)
- High priority data sending
- The station could send any high priority data
frame only within MHT period - Low priority data sending using Times Token
Rotation Protocol - All hosts agree on a common Token Waiting Time
(TWT).They will aim to make the token rotate
around the network at least once per TWT. Hence,
they can each expect to see the token once TWT. - Each host on the network maintains a timed Token
Rotation (TRT) Timer, that indicates when the
token is next expected to arrive. - TRT is counting down..
- If the token arrives before TRT expired , we say
it is Early.If the token arrives after TRT
expired, we say it is Late. - A host can only transmit if it receives the
token, AND the token is Early.
31
FDDI Timed Token Rotation Protocol
Time 0 Host receives Token and sets TRT TTRT (
8ms in this example)
TRT
Time until next token is expected (TTRT)
8ms
Count down
0ms
Time 5ms Token arrives host wants to
transmit one or more packets
Reset TRT TTRT
Token is Early Host is allowed to transmit up to
3ms (TWT-TRT) is transferred to a new
counter Token Holding Timer (THT) keeps track
of the amount of time host can transmit
TRT
8ms
3ms
THT
3ms
When THT reaches 0 ms host cannot start new packet
Count down
0ms
0ms
32
FDDI Timed Token Rotation Protocol
- All hosts agree on a common Token Waiting Time
(TWT).They will aim to make the token rotate
around the network at leastonce per TWT. Hence,
they can each expect to see the token once TWT. - Each host on the network maintains a timed Token
Rotation (TRT) Timer, that indicates when the
token is next expected to arrive. - TRT is counting down..
- If the token arrives before TRT expired , we say
it is Early.If the token arrives after TRT
expired, we say it is Late. - A host can only transmit if it receives the
token, AND the token is Early.
33
Priority Control (LTRT?TRT)
D9 D7 D5 D1
8
8
8
8
MHT 3 MLWT 8
5
5
5
D9
5
3
D7
2
2
2
5
3
Same Time
6
0
3
0
D5
2
5
0
3
0
D1
3
Round 1
3
5
8
0
D9
0
3
5
3
2
5
D7
5
0
2
2
3
D5
0
8
2
5
2
D1
0
Round 2
3
6
6
0
2
5
0
3
3
Time Axis
8
3
0
D1 and D7 is high priority node
5
Round 3
3
34
Token Bus
- Ring initialization
- First ready station wait for token ?t
- Send ClaimToken If can not see a token in ?t
- If a collision is detected wait for a random
period - Send Token if a collision is not detected
35
Token Bus
- Join the Ring
- Token holding station send a Solicit_Successor
every ?T period - Solicit_Successor frame contains
- Sending station Address (11)
- Its Successor station Address (17)
- New station (15) who has address between 11 and
17 would - send Set_Successor frame contains its own
Address to the sending station - Wait for ACK
- Set its predecessor as 11
- Set its own successor as 17
- Sending station update its successor to 15
36
Token Bus
- Leave the Ring
- Wait for a Token
- Send Set_Successor to its predecessor contains
its own successor address - Send a Token to its successor
37
Token Bus Problem
- Result of broken-ring
- Token will be lost when the predecessor of the
out of order station pass a token to it - Frame will be lost cause by the destination is
not functioning - Token is lost because the out of order station is
the token holding station
38
Token Bus Problem
- Solution
- 1. and 2. Target Station is down
- Sending station must wait for ACK and investigate
for a Token after sending a Frame (or Token) in
?t - In case of token losting Sending station send
Who_Follows_me contains the out of order
station - The Successor station of the out of order station
send Set_Successor to the Sending station - 3. Token Holding Station is down
- Ring Reinitializing
39
FDDI Fiber Distributed Data Interface
- Dual counter-rotating rings
- 100 Mbps on optical fibers
- Up to 500 nodes
- Total length less than or equal to 200 km
MAC
FDDI STANDARD
PHY
PMD
40
FDDI PMD
- Specifies fiber, optical transmitters, receivers,
connectors and optical bypass switches - Optical transmitters are LEDs with wavelength of
1300nm - Three types multi-mode fiber, single-mode fiber,
twisted-pair electrical cable.
41
FDDI PHY
- Specifies the encoding and modulation
- Uses 4B/5B encoding
- Modulation non-return to zero with inversion
(NRZI) - One transition at least every three bit periods
42
FDDI Timed Token Rotation Protocol
Time 0 Host receives Token and sets TRT 0 (
8ms in this example)
TRT
Time until next token is expected (TTRT)
8ms
Count down
0ms
Time 5ms Token arrives host wants to
transmit one or more packets
Reset TRT TTRT
Token is Early Host is allowed to transmit up to
3ms (TWT-TRT) is transferred to a new
counter Token Holding Timer (THT) keeps track
of the amount of time host can transmit
TRT
8ms
3ms
THT
3ms
When THT reaches 0 ms host cannot start new packet
Count down
0ms
0ms
43
Exercise
- Fill the following diagram as the previous
example, in case no priority control are
implement. - What is the purpose of exponential back-off?
44
D9 D7 D5 D1
8
8
8
8
MHT 3 MLWT 8
5
5
3
5
5
D9
2
3
2
5
2
D7
0
0
2
6
3
D5
0
3
0
8
6
D1
D9
D7
D5
D1
D9