Active Content - PowerPoint PPT Presentation
Active Content
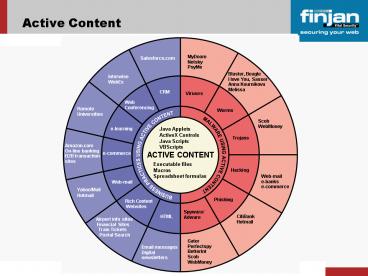
Anna Kournikova. Melissa. Scob. WebMoney. Web-mail. e-banks. e-commerce. CitiBank. Hotmail ... Propagation: Electronic (push/pull) Key Impact: Corporate productivity ... – PowerPoint PPT presentation
Title: Active Content
1
Active Content
2
Evolution Disconnected World
3
Evolution Semi-Connected World
4
Evolution Connected World
5
The Evolutionary Principle Finjans Law
- Every 12-18 months, a new stage takes place
- Exploitation of a new technology
- Refinement of an existing technology
- Blending of several techniques into one attack
- Intervals between stages is shortening as
technology continues to improve at rapid pace
6
The Web A False Feeling
- We know Email messages can be malicious
- . but so can Web pages
- Web threats are serious, even more than Email
ones
- Web threats are here!
7
Web Threats - Infection Methods
- Almost exclusively based on Active Content
- Java Script, VB Script, ActiveX, Java Applets
- Browser vulnerabilities
- Drive-by download
- While visiting Web sites
- While reading emails via web browser
- Piggyback Installation
- Bundled as a hidden component of programs, such
as - Games, P2P, Screen savers
8
Social Engineering is Epidemic
eBay, Yahoo, Microsoft All guide us to click Yes
9
Social Engineering is Epidemic
eBay, Yahoo, Microsoft All guide us to click Yes
and so do Spyware sites
10
Social Engineering is Epidemic
11
Social Engineering is Epidemic
Drag the window to revealthe real information!
12
Drive-by, While visiting Web sites
Innocent Free Games site
13
Drive-by, While visiting Web sites
Innocent Free Games site
14
Finjan Security Without Compromise
Best-of-breed security solutions on a single box
Behavior Blocking, Vulnerability Anti.doteTM,
Anti-Spyware, Anti-Virus, URL Filtering,
Zero-hour protection
PowerShow.com is a leading presentation sharing website. It has millions of presentations already uploaded and available with 1,000s more being uploaded by its users every day. Whatever your area of interest, here you’ll be able to find and view presentations you’ll love and possibly download. And, best of all, it is completely free and easy to use.
You might even have a presentation you’d like to share with others. If so, just upload it to PowerShow.com. We’ll convert it to an HTML5 slideshow that includes all the media types you’ve already added: audio, video, music, pictures, animations and transition effects. Then you can share it with your target audience as well as PowerShow.com’s millions of monthly visitors. And, again, it’s all free.
About the Developers
PowerShow.com is brought to you by CrystalGraphics, the award-winning developer and market-leading publisher of rich-media enhancement products for presentations. Our product offerings include millions of PowerPoint templates, diagrams, animated 3D characters and more.