Timestamps PowerPoint PPT Presentations
All Time
Recommended
As transactions read/write, check that what they are doing ... X a value that would have overwritten T's value, negating T responsibility for the value of X. ...
| PowerPoint PPT presentation | free to download
Record category wise exact time of event with datetime location & Note
| PowerPoint PPT presentation | free to download
Freely skewed. d1 d2 d3 d4. Freely skewed = Only add a new ... Freely skewed model. Empirical and theoretical properties of TSGs (e.g., in-degree distribution) ...
| PowerPoint PPT presentation | free to download
Instruction Set Principles Timestamped 4/8/02
| PowerPoint PPT presentation | free to download
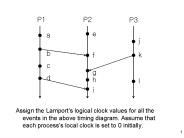
Lamport timestamps for the events shown in Figure 10.5. Dr. Jenhui ... Vector timestamps and variable values for the execution of Figure 10.9. Dr. Jenhui Chen ...
| PowerPoint PPT presentation | free to download
Only about 10% of links' timestamps are off, an effect of revelation process. Generally, BGP timestamps can be used as calibration points to evaluate accuracy ...
| PowerPoint PPT presentation | free to view
Lamport's logical timestamps preserve causality: ... A send (message) event carries its timestamp ... Lamport Timestamps. Logical Time ...
| PowerPoint PPT presentation | free to view
Temporal Databases. Interval Data Type (Timestamps) ... Classified as historical, rollback or bi-temporal ... What are temporal databases? ...
| PowerPoint PPT presentation | free to view
Unix timestamp converter an intuitive and powerful tool for converting Unix timestamps and human-readable times. Try today!
| PowerPoint PPT presentation | free to download
Two basic concurrency control techniques: Locking methods Timestamping Locking Transaction uses locks to deny ... or write (exclusive) lock on a data item before ...
| PowerPoint PPT presentation | free to view
Requirements like pause, record etc. Integration with web architecture ... Normal Play Time (NPT) : seconds, microseconds. SMPTE timestamps: seconds, frames ...
| PowerPoint PPT presentation | free to download
- Project Update - Sony Corporation Hiroki KAMINAGA ... fast-boot-menu Done fast-timestamps (timing-API) Done hrt(hrt-core, hrt-i386, hrt-ppc32) ...
| PowerPoint PPT presentation | free to download
Conservative timestamping delays each operation until there is an assurance that ... Conservative Timestamp Ordering. Distributed DBMS. Page 10-12. 14 ...
| PowerPoint PPT presentation | free to download
receive procedure. Verify integrity, authenticity and consistency ... packet procedure. Process receive and transmit timestamps and ... filter procedure ...
| PowerPoint PPT presentation | free to download
The revised version' of Needham-Schroder nonces replaced by timestamps. A S: A, B ... The core of the Burrows-Abadi-Needham logic: ...
| PowerPoint PPT presentation | free to download
No server or client-side modifications necessary. What are Graybox Techniques? ... Not a static size, no upper-bound. Timestamps: 'jiffies', per page. Approach ...
| PowerPoint PPT presentation | free to download
temporal locality. technique. timestamps hint as to when ... temporal ... temporal locality (time stamps) spatial locality (file location) data recovery ...
| PowerPoint PPT presentation | free to view
3mm spectral-line observing with Mopra. Tony Wong. ATNF & UNSW ... Interpolate to timestamps of spectra in aips reader (or better yet, using ...
| PowerPoint PPT presentation | free to download
Solution: Analyze current Internet table to determine node distribution characteristics ... Consistency among timestamps taken by different devices is a requirement ...
| PowerPoint PPT presentation | free to download
Grid Event Management Using R-GMA Monitoring Framework. ISGC April 27-29, 2005 ... Automatic timestamps. Flexible SQL queries. Planned features. Security ...
| PowerPoint PPT presentation | free to view
... as timestamps. next packet to transmit is one with lowest timestamp ... keep fine-grained timestamps for each packet. check for timeout on first duplicate ACK ...
| PowerPoint PPT presentation | free to download
TCP & HTTP events : Timestamps, sequence number, etc. HTTP headers. Byte counts. Internet ... Use timestamp. Performance effects of the proxy. Hit ratio ...
| PowerPoint PPT presentation | free to view
Uses a global timestamp. Reads virtually all data. Limited only by shaping/conversion time ... are 4 other gammas with timestamps within /- 50ns of Tg. 22nd ...
| PowerPoint PPT presentation | free to download
If timestamps are present within the signature, for each ... e.g. time-stamps. SignatureOK. CertificatePathValidity. CertificateIdentifier. PathValiditySummary ...
| PowerPoint PPT presentation | free to view
Serial number (unique to issuer) ... provided by using sequence numbers or timestamps or challenge/response ... a number of clients and a number of application ...
| PowerPoint PPT presentation | free to download
Decentralized autonomous organizations are typified by the use of blockchain technology to provide a secure ledger to track digital interactions across the internet, hardened against forgery by trusted timestamping and dissemination of a distributed database. In today’s era, the DAO Blockchain development company is used for investing money, charity, fundraising, lending, NFT transactions, and social coordination.
| PowerPoint PPT presentation | free to download
Therefore we recommend that the draft continues with IEEE1588 as MUST, but notes that systems SHOULD be able to read/process timestamps received in NTP format.
| PowerPoint PPT presentation | free to download
Pi timestamps event e with Ci (e) i. Then: Ci (a) i happened before Cj (b) j if and only if: ... message at Pj is queued in queuej, according to its timestamp. ...
| PowerPoint PPT presentation | free to download
With compression, ASCII and HATF close. Representing 64-bit timestamps is expensive ... Is HATF sufficiently better than ASCII? How to separate, hide representation? ...
| PowerPoint PPT presentation | free to download
Feature Extraction. 17. Features to describe update frequency ... Improve timestamps extraction algorithm. Stronger prediction model than linear regression ...
| PowerPoint PPT presentation | free to view
Each time a password is sent in the clear, there is a chance ... Very bad if Authentication Server compromised. Timestamps require hacker to guess in 5 minutes. ...
| PowerPoint PPT presentation | free to download
Read timestamps from quorum. Choose higher, unique timestamp. Read(): Read ... Return highest-timestamp correct value. Porquerolles Spring 03. Dahlia Malkhi. 21 ...
| PowerPoint PPT presentation | free to view
To help you improve your song, solicit feedback from friends or collaborators. To refer to specific sections, such as a bridge or chorus, use timestamps. Begin a project and keep track of all your versions with critiques in one easy-to-access location- Jack Hanson. It's ideal for gathering feedback and collaborating on a work in progress.
| PowerPoint PPT presentation | free to download
at the commit time, assigned new timestamp. Read-only transaction ... Assigning Timestamps. Version List Entries. space for versions is dynamically allocated ...
| PowerPoint PPT presentation | free to download
By A.E.Bailey, CTO, Tantalus. Credit N. McVeity, Lead Programmer, Tantalus. ... Main features from Tantalus point of view. MD5 instead of timestamps. Build Cache ...
| PowerPoint PPT presentation | free to view
Temporal belief updating at T using timestamps associated with information from ... Belief updates depend on the length of the time interval since the observation. ...
| PowerPoint PPT presentation | free to download
Who owns the system? Who manages the system? Is it patched? What ... Stores 3 timestamps (MAC) of target. Uses ObjectID to find file (Distributed Link Service) ...
| PowerPoint PPT presentation | free to view
Calendar Schema ... E.g., given the calendar schema (year, month, Thursday) ... Given a calendar schema R, a set T of timestamped transactions and a match ratio ...
| PowerPoint PPT presentation | free to view
... one cannot directly compare the timestamps of two events to determine their ... FLC4: Values in the timestamp vectors are never decremented. ...
| PowerPoint PPT presentation | free to download
Use timestamps as replacement metric. Uppsala ... Elbow cache, 7-step feedback, 5-bit timestamp. Uppsala Architecture Research Team ... Timestamps are useful. ...
| PowerPoint PPT presentation | free to download
Casual order with logical timestamps. Casual order with vector ... Casual multicast and consistent cuts. Total order. Sync. order. Research Direction ...
| PowerPoint PPT presentation | free to download
SAN DIEGO SUPERCOMPUTER CENTER. A National Laboratory for Computational Science & Engineering ... time-period (start and expire timestamps) number of access (count) ...
| PowerPoint PPT presentation | free to view
2507 is not enough: Options like SACK, timestamps. Need to compress ECN bits well! ... SACK, timestamp, ECN, Diffserv, Initial TCP negotiation, etc ...
| PowerPoint PPT presentation | free to download
Record timestamps modulo N (the window size), so we can represent any relevant ... overlap in timestamps. Buckets are sorted ... End timestamp = current time. ...
| PowerPoint PPT presentation | free to view
to run GIMPS signaling along a chain of GIMPS nodes without the need for a full-fledged NSLP ... Currently, IP addresses and timestamps (to calculate RTTs) ...
| PowerPoint PPT presentation | free to download
Continuously monitoring and detecting changes is crucial ... Filters out changes to images, advertisements, and other mundane content such as timestamps ...
| PowerPoint PPT presentation | free to download
Multipoint measurement system. GPS timestamping enables breaking-down the one-way delays ... Practical, hands-on work with new technologies and prototypes ...
| PowerPoint PPT presentation | free to download
The physical level: efficient storage and indexing ... Financial: Stock market data ... Scientific: Timestamping satellite images. Dating archeological finds ...
| PowerPoint PPT presentation | free to download
Trust anchors (TAs) are trusted public keys with with associated information ... of signed objects, including firmware, timestamps, OCSP responses, keys, etc. ...
| PowerPoint PPT presentation | free to download
The basic idea is to interpolate the camera during the period of two timestamps, ... The cameras are interpolated along the track of the transformation from a ...
| PowerPoint PPT presentation | free to view
have location aware devices (GPS, cell-tower/wifi-antenna triangulation) with ... positional updates are timepoints (locations with timestamps) accompanied with ...
| PowerPoint PPT presentation | free to view
Performance degrades gradually if more server faults are tolerated ... Single Phase Updates in normal execution ... Timestamps contain clientID, operation, OHS ...
| PowerPoint PPT presentation | free to view
... not assume any fixed type of movements. Otherwise, we miss the other types. ... How many past timestamps should be considered (f=5 captures all movements tested) ...
| PowerPoint PPT presentation | free to view
Many results for various network/communication/fault models ... Tu=Tl Td (Td is upper bound on propagation delay and timestamping delay) ...
| PowerPoint PPT presentation | free to view
Leap seconds are introduced when necessary to keep in phase with the sun. ... The time daemon tells everyone how to adjust their clock. Lamport Timestamps ...
| PowerPoint PPT presentation | free to view
Sir John Tenniel; Alice's Adventures in Wonderland,Lewis Carroll ... Transmit timestamps are captured shortly before the beginning of the packet; ...
| PowerPoint PPT presentation | free to download