Kasamis PowerPoint PPT Presentations
All Time
Recommended
... critical section it sends the PRIVILEDGE message containing the token the requesting site. ... the process and send with a PRIVILEDGE message along the edge. ...
| PowerPoint PPT presentation | free to view
4.5 Distributed Mutual Exclusion Presenter: Weiling Li Instructor: Dr. Zhang Overview Part I: Basic Knowledge [1,2,3] * Contention-based Mutual Exclusion * Token ...
| PowerPoint PPT presentation | free to download
Mughal Print Fabric, Kalamkari Fabric, and much more prints form the roots of Indian tradition and culture. Explore a wide range of traditional printed fabric on symplico.com
| PowerPoint PPT presentation | free to download
Dėl informacijos, patarimų arba užklausų prašome kreiptis: T: 8 679 03408 E: info@statvila.lt W: https://www.statvila.lt/
| PowerPoint PPT presentation | free to download
Syntactic Parsing * *
| PowerPoint PPT presentation | free to download
... (1) Book (2) that (3) flight. Earley-Stolcke Parser (1) A state ... Real-time performance. Labeling activities and person-vehicle interactions in a parking lot ...
| PowerPoint PPT presentation | free to download
Title: PowerPoint Presentation Author: Wim van Dam Last modified by: Bala Ravikumar Created Date: 8/27/2001 7:35:01 AM Document presentation format
| PowerPoint PPT presentation | free to download
Case 4: Bifurcation. combining two optimal substructures i, k and k 1, j. k ... pushdown stack is used to deal with bifurcated structures. Traceback Pseudocode ...
| PowerPoint PPT presentation | free to download
Mutual Exclusion Continued Quorum Based Algorithms Each process j requests permission from its quorum Qj Requirement: j, k :: Qj Qk j, k :: Qj Qk Rj ...
| PowerPoint PPT presentation | free to view
Lexical Semantic + Students Presentations ICS 482 Natural Language Processing Lecture 27: Husni Al-Muhtaseb * * * * Lexical Relations in WordNet * * Structure of ...
| PowerPoint PPT presentation | free to download
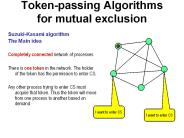
Token-passing Algorithms for mutual exclusion Suzuki-Kasami algorithm The Main idea Completely connected network of processes There is one token in the network.
| PowerPoint PPT presentation | free to download
Token-passing Algorithms Suzuki-Kasami algorithm Completely connected network of processes There is one token in the network. The owner of the token has the ...
| PowerPoint PPT presentation | free to download
LL(1) parsed top-down, left to right scan, leftmost derivation, 1 symbol lookahead ... The leftmost and rightmost derivations for a sentential form may differ, even in ...
| PowerPoint PPT presentation | free to download
(Finite State Automata,Finite State Transducers, Markov ... 'the man saw the girl with the telescope' The girl has the telescope. The man has the telescope ...
| PowerPoint PPT presentation | free to download
Note that the regular grammars are a proper subset of the context-free grammars. ... a node (e.g., S), and then apply that same rule again, and again, ad infinitum. ...
| PowerPoint PPT presentation | free to view
EC 723 Satellite Communication Systems Mohamed Khedr http://webmail.aast.edu/~khedr Syllabus Tentatively Interleaving Convolutional codes are suitable for memoryless ...
| PowerPoint PPT presentation | free to download
Recursive case makes this dynamic programming because we only calculate B and C once ... LOVE JOHN. LOVE MARY. where A B means that B depends on A. 29 ...
| PowerPoint PPT presentation | free to view
for begin=1 to N-span 1. end = begin span 1; for m=begin to end-1; ... begin=1 begin=2 begin=3. span=1. span=2. span=3. Data structures for the chart (1) (2) ...
| PowerPoint PPT presentation | free to download
Lexicalized and Probabilistic Parsing Part 2 ICS 482 Natural Language Processing Lecture 15: Lexicalized and Probabilistic Parsing Part 2
| PowerPoint PPT presentation | free to download
high data rates : (minimum) 144 kb/s in all radio environments and 2 Mb/s in low ... terminals & SIMs will cooperate in requesting, storing and executing ...
| PowerPoint PPT presentation | free to download
... Kasami algorithm or Earley s algorithm Fortunately, Large subclasses of CFGs can be parsed with limited lookahead Most programming language constructs fall ...
| PowerPoint PPT presentation | free to download
Chapter 5 Digital Modulation Systems Spread Spectrum Systems Huseyin Bilgekul EEE 461 Communication Systems II Department of Electrical and Electronic Engineering
| PowerPoint PPT presentation | free to download
Lexical Semantic + Students Presentations ICS 482 Natural Language Processing Lecture 26: Lexical Semantic + Students Presentations Husni Al-Muhtaseb
| PowerPoint PPT presentation | free to download
(viterbi algorithm) ... (earley parsing algorithm) CKY (CKY parsing algorithm, CYK ) ...
| PowerPoint PPT presentation | free to view
Title: Slide 1 Author: srini Last modified by: srini Created Date: 10/29/2005 4:47:42 PM Document presentation format: On-screen Show Company: AT&T Labs Research
| PowerPoint PPT presentation | free to download
Search for the Lepton Flavor Violating Decay meg in the MEG Experiment
| PowerPoint PPT presentation | free to view
A very important property of PN sequences is the periodic auto correlation function ... B-M requires (at most) 2n error-free chips to determine generating polynomial ...
| PowerPoint PPT presentation | free to view
(equivalent to finite automata & HMM's) (equivalent to SCFG's & pushdown automata) ... A in a cell cellA to the two cells cellB and cellC corresponding to B and C in ...
| PowerPoint PPT presentation | free to download
Title: Quick Speech Synthesis Created Date: 4/29/2003 1:19:27 AM Document presentation format: On-screen Show Company: UofC Other titles: Arial Times New Roman ...
| PowerPoint PPT presentation | free to download
CYK Parser. Von Carla und Cornelia Kempa. Overview. CYK Parser ... not only to annoy students ) Perfect grammar for CYK. How CYK works for. a grammar in CNF ...
| PowerPoint PPT presentation | free to download
Wireless: multipath delay, interference, fading. OFDM bwrc.eecs.berkeley.edu ... Rake Receiver. http://www.comlab.hut.fi/opetus/238/lecture4_Intro_to_WCDMA.pdf ...
| PowerPoint PPT presentation | free to view
Block cipher encryption provides confidentiality by ... LUCIFER (author: Horst Feistel) DES (Data Encryption Standard) MISTY1. KASUMI (used in UMTS) ...
| PowerPoint PPT presentation | free to view
Project: IEEE P802.15 Working Group for Wireless Personal Area ... Intercorrelation between. sequences 1 and 2. Jan. 2005. THALES Communications. Slide 16 ...
| PowerPoint PPT presentation | free to download
Chapitre 3 Exclusion mutuelle r partie
| PowerPoint PPT presentation | free to download
Tightly-coupled operating system for multi-processors and homogeneous multicomputers ... This layer is the last part of a basic network protocol stack ...
| PowerPoint PPT presentation | free to download
... of a PP is preposition Each PFCG rule s LHS shares a lexical item with a non-terminal in its RHS Increase in Size of Rule Set in Lexicalized CFG If R is the ...
| PowerPoint PPT presentation | free to download
Let n=10, therefore, N=2n - 1 = 1023 (length of a' ... 1023/33 = 31 which will be the length of a' ... obtain a set of 2n/2 = 32 binary sequences of length 1023 ...
| PowerPoint PPT presentation | free to view
will cover about half the course, supplemented by copies of papers ... If a b and b a, then a and b are concurrent ( a || b) Logical Clock ...
| PowerPoint PPT presentation | free to download
Paula Matuszek. Mary-Angela Papalaskari. Dick Crouch. Tracy Kin. L. ... Abdul Rahman Al Khaldi - Statistical Transliteration for English-Arabic Cross. 9 ...
| PowerPoint PPT presentation | free to view
For a pure random (noise) binary (1,-1) sequence {ck} of period N the periodic ... Data modulator: each LT (Ts) seconds output a tone (from 2L tones) ...
| PowerPoint PPT presentation | free to view
... (Quadrature Phase Shifted Keyed) MSK (Minimum Shifted Keyed) BINARY SHIFT KEYING This technique is implemented with a Balanced Modulator Two basic types ...
| PowerPoint PPT presentation | free to view
Clone Jurassic park! Study evolution of function. Find functional elements within a genome ... More general: Any 4-long stem, 3-5-long loop: S aW1u | gW1u ...
| PowerPoint PPT presentation | free to view
There could be almost 1000 frames on the path to the satellite at any instant in time ... Large satellite antenna footprint (frequency re-use problem) ...
| PowerPoint PPT presentation | free to view
By including a' in the set, we obtain a set of 2n/2 = 32 binary sequences of length 1023 ... DIRECT SEQUENCE SYSTEMS. DSSS is the most common commercially ...
| PowerPoint PPT presentation | free to view
Title: IV-10. . . . Author: Andrej Kibrik Last modified by: Z Created Date
| PowerPoint PPT presentation | free to download
the probability of parse trees rooted at the start nonterminal, exluding the ... if we know the parse tree for each training sequence, learning the SCFG ...
| PowerPoint PPT presentation | free to view
Status of the MEG meg Experiment at PSI
| PowerPoint PPT presentation | free to view
Title: Intelligent Information Retrieval and Web Search Author: Raymond Mooney Last modified by: Ray Mooney Created Date: 5/20/2001 10:11:52 PM Document presentation ...
| PowerPoint PPT presentation | free to download
E-mail : cdma_team@yahoo.com. May 3, 2003. CDMA Team. Contents ... [1] T.S. Rappaport, Wireless communications, Principles and Practice, 2nd Ed., Prentice Hall ...
| PowerPoint PPT presentation | free to view
Secretary of defense was hostile to mathematical research. ... Smith-Waterman for sequence alignment. Bellman-Ford for shortest path routing in networks. ...
| PowerPoint PPT presentation | free to view
Title: Definizioni di base Author: am Last modified by: am Created Date: 9/1/2002 10:16:14 AM Document presentation format: On-screen Show Other titles
| PowerPoint PPT presentation | free to download
Only searches for trees that can be answers ... Use one kind as the control and the other as a filter ... Combine the two to avoid over-generation: Top-Down ...
| PowerPoint PPT presentation | free to view
Dr. Kalpakis. CMSC 621, Advanced Operating Systems. Fall 2003 ... a set of nodes S, a quorum set (coterie) C is a set of subsets of S, called ...
| PowerPoint PPT presentation | free to view
NP British, left, waffles, Falkland, Islands. 5/4/09. Linguistics 406. 26. CYK algorithm ... British left waffles on Falkland Islands. 0 1 2 3 4 5 6. N, A, NP ...
| PowerPoint PPT presentation | free to view