Identity Protection Software PowerPoint PPT Presentations
All Time
Recommended
Traditional password challenges are becoming obsolete with the arrival of biometric identity verification software. With a variety of biometric techniques, users can now easily verify their identities, enhancing security protocols while optimising user experiences. The program's simple incorporation of the phrase guarantees that it will be the main topic of conversation when identity verification is brought up, highlighting its critical role in the ever-changing field of cybersecurity evolution.
| PowerPoint PPT presentation | free to download
To properly address the current and future risks inherent in the Age of ... or to report a potential scam or theft. ... Don't Respond to Email Requests ...
| PowerPoint PPT presentation | free to view
Being a Top Cryptocurrency Exchange Software Development Company, Coinjoker provides white label cryptocurrency exchange software to launch your cryptocurrency exchange platform. Get Affordable Crypto exchange platform development Services at an affordable cost.
| PowerPoint PPT presentation | free to download
Image & Video Protection
| PowerPoint PPT presentation | free to download
Identity theft is a type of fraud that involves stealing valuable personal information like passwords, credit card details or fraudulently accessing secure information.
| PowerPoint PPT presentation | free to download
Software Based Memory Protection For Sensor Nodes Ram Kumar, Eddie Kohler, Mani Srivastava (ram@ee.ucla.edu) CENS Technical Seminar Series
| PowerPoint PPT presentation | free to view
Runtime Verification and Software Fault Protection with Eagle Allen Goldberg Klaus Havelund Kestrel Technology Palo Alto, USA
| PowerPoint PPT presentation | free to download
Pluralism of Operators and Technologies. Human Integration. Consistent Experience Across Contexts ... 'Technical identity systems must only reveal information ...
| PowerPoint PPT presentation | free to view
Have the best protection for your PC only with REVE antivirus. We are a Singapore based conglomerate, advanced in areas such as IP communications, web based software and roaming application. The antivirus we offer is the best antivirus online as it’s enabled with advanced online protection, internet security, fastest scan engine and turbo scan technology and everything that is needed for the best PC performance. So visit our website and download REVE antivirus’s free trial.
| PowerPoint PPT presentation | free to download
EAGLE with data binding has worst case dependent on length of input trace ... Eagle Implementation ... An Eagle compiler ...
| PowerPoint PPT presentation | free to download
Data protection audit and data protection issues in the telecom sector Dr. Katalin Egri Legal advisor Office of the Parliamentary Commissioner for
| PowerPoint PPT presentation | free to download
Self-defending software: Automatically patching errors in deployed software Michael Ernst University of Washington Joint work with: Saman Amarasinghe, Jonathan ...
| PowerPoint PPT presentation | free to download
Object-Oriented Software Engineering. Practical Software Development ... Reel of Film: Class; instances are physical reels. Film reel with serial number SW19876 ...
| PowerPoint PPT presentation | free to download
Best Academic discount software, School software on Sale. Get a Collection of Student discount software! We carry all Lowest price academic, school, college & university software.
Buy cheap software from Softwareexcellent.com and save big on discount software from leading brands like mcafee, norton, webroot and office and many more
Kaspersky Antivirus Software is available with distinct features and functions for Windows-specific and multi-operating gadget programs. The software is designed specifically to protect the device from every malicious threat that can damage the system. The only flaw in this total protection software is that none of its programs consist of a complete VPN or identity theft protection.
Free PC Optimizer Software has security and privacy tools to protect your computer from malware & identity theft & also provides real protection against spyware,trojan & other malware.
| PowerPoint PPT presentation | free to download
... Booch, OOSE(Object-Oriented Software Engineering) Shlare/Mellor, ... (state), (behavior), (identity) .
| PowerPoint PPT presentation | free to view
Cloud security software offers security to cloud-based services or cloud computing architectures. Cloud security software can be standalone solution or a suite of products. It focuses on key parameters such as data protection, compliance, architecture, governance, as well as identity and access. TechNavios analysts forecast the Global Cloud Security Software market to grow at a CAGR of 48.46 percent over the period 2014-2019. See Full Report: http://bit.ly/1Ar3m2i
| PowerPoint PPT presentation | free to download
Online software security involves protecting applications and user data from cyber threats through measures like encryption, firewalls, antivirus, and two-factor authentication to ensure safe and secure online interactions.
| PowerPoint PPT presentation | free to download
Online software security involves protecting applications and user data from cyber threats through measures like encryption, firewalls, antivirus, and two-factor authentication to ensure safe and secure online interactions.
| PowerPoint PPT presentation | free to download
LTS Secure Identity Management provides tools and software solutions that helps protect data from unauthorized access and identity
| PowerPoint PPT presentation | free to download
LTS Secure Identity Management provides tools and software solutions that helps protect data from unauthorized access and identity
| PowerPoint PPT presentation | free to download
Ping Identity Corporation provides cyber security solutions to Fortune 100 companies globally. It offers Ping Identity Platform, a solution for federated access management and federated identity management that includes PingFederate Server, a federation server that provides identity management, web single sign-on (SSO), and API security for customers, partners, and employees
| PowerPoint PPT presentation | free to download
The digital world is undergoing a huge transformation. With newer updates and technology coming up from time to time. Companies who are into making Antivirus software understand the consumer's ever-changing and dynamic pc security needs. There have been several instances of identity theft, data theft, financial fraud, and many more forms of cyber threats in recent times. The highly functional K7 Antivirus Premium, along with its features brings premium security to your fingertips!
| PowerPoint PPT presentation | free to download
Identity and access management from leo technosoft provides tools and software solutions that helps protect data from unauthorized access and identity.
| PowerPoint PPT presentation | free to download
LTS Secure Identity Management provides tools and software solutions that helps protect data from unauthorized access and identity
| PowerPoint PPT presentation | free to download
Powerful AI Technology D-ID’s proprietary algorithm combines the most advanced image processing and deep learning techniques to resynthesize any given photo to a protected version. The protected photos are unrecognizable to face recognition algorithms. However, humans will not notice any difference. The technology is designed to be difficult for AI to overcome.
| PowerPoint PPT presentation | free to download
3rd Int'l Forum on Financial Consumer Protection & Education. Our Identity ... Int'l Forum on Financial Consumer Protection & Education. How Can Identity Theft ...
| PowerPoint PPT presentation | free to view
Identity and access management from leo technosoft provides tools and software solutions that helps protect data from unauthorized access and identity.
| PowerPoint PPT presentation | free to download
For more information on Akamai’s DDoS mitigation software Prolexic and DDoS scrubbing service, you can sign up for a personalized DDoS threat briefing by an Akamai security expert who will walk you through mitigation strategies, personalized for your organization’s attack surfaces.
| PowerPoint PPT presentation | free to download
Cylinder Management Software for use tracking cylinder
| PowerPoint PPT presentation | free to download
The Bundle Identity & Privacy Protection Services safeguards your computer from attacks of threats, and many more.
| PowerPoint PPT presentation | free to download
The Bundle Identity & Privacy Protection Services safeguards your computer from attacks of threats, and many more.
| PowerPoint PPT presentation | free to download
is the foundation and core for all security ... National eIDs, especially the EU's STORK (Secure Identity Across Borders Linked) initiative ...
| PowerPoint PPT presentation | free to download
Once Satawareupon bytehead a time, web development company each mobile app developers stunning app developers near me app you hire flutter developer want to ios app devs apply a software developers started software company near me with a software developers near me concept. good coders An admirable top web designers concept sataware is even software developers az now app development phoenix half of app developers near me the achievement idata scientists but the top app development humblest source bitz period software company near for a app development company near me way to software developement near me the creation app development new york Just software developer los angeles visualize how to create an app
| PowerPoint PPT presentation | free to download
2005 Qwest Communications International, Inc. NOTE: Qwest is providing the above ... Qwest assumes no liability for the use of this information and does not ...
| PowerPoint PPT presentation | free to view
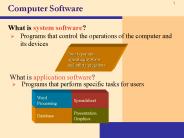
Computer Software What is system software? Programs that control the operations of the computer and its devices Two types are operating systems and utility programs
| PowerPoint PPT presentation | free to download
File-sharing programs such as Kazaa, Napster, Limewire open your entire computer to the world. ... Be very careful about 'Free Wi-Fi' Turn off file sharing ...
| PowerPoint PPT presentation | free to view
Identity and access management from leo technosoft provides tools and software solutions that helps protect data from unauthorized access and identity.
| PowerPoint PPT presentation | free to download
... they apply for a Birth Certificate, new Identification ... Information systems that are compatible with one another. Increased dialogue with one another ...
| PowerPoint PPT presentation | free to view
Onion router type of network use proxies owned by individual operators ... Subscription to Filter Lists. 6/12/09 ... Free open-source disk encryption software ...
| PowerPoint PPT presentation | free to download
CS3773 Software Engineering Lecture 07 Software Architecture Design UTSA CS3773 UTSA CS3773 * UTSA CS3773 * Interpreter Style Examples Programming Language Compilers ...
| PowerPoint PPT presentation | free to view
Antivirus software allows users to protect their system from viruses, malware and other forms of attacks on their operating system. It scans files downloaded from the internet or received as email attachments for viruses, spyware and other types of malicious programs before opening them so users don’t have to worry about downloading harmful items.
| PowerPoint PPT presentation | free to download
RemoteDesk is monitoring real-time employee computer activities from anywhere. Remote desktop software provides data protection for business & home worker. Visit here-
| PowerPoint PPT presentation | free to download
Discover the power of remote identity verification and its numerous benefits. Explore how this cutting-edge technology works seamlessly to enhance security and streamline processes. Elevate your digital identity experience with our insightful guide.
| PowerPoint PPT presentation | free to download
Kicking off Data Privacy Week with Key Insights on the New DPDP Rules! The Digital Personal Data Protection Rules 2025 are here, setting the stage for a new era of data privacy in India. Get ahead of the curve with our #Whitepaper breaking down the DPDP Act 2023 and its key provisions. For Detailed Info Visit our Article - https://www.infosectrain.com/blog/draft-of-indias-digital-personal-data-protection-act-2023/ Highlights: Clear notice and consent requirements • Enhanced security safeguards for personal data • Stronger rights for Data Principals • Detailed data retention and erasure policies Download the Whitepaper now to navigate the evolving digital privacy landscape and stay compliant!
| PowerPoint PPT presentation | free to download
Read the blog and learn about virus protection and how to chose the best antivirus software?
| PowerPoint PPT presentation | free to download
Package design combines creativity, technical skills, and knowledge of consumer behavior. Aspiring designers often study graphic or industrial design to learn about visual communication and product aesthetics. They work in various industries, including food, cosmetics, and electronics, creating attractive and functional packaging that appeals to consumers. Effective package design considers factors like materials, shapes, colors, and typography to ensure products are visually appealing and practical. It not only protects the product but also represents the brand and engages the target audience. Recently, eco-friendly packaging has become more important, emphasizing sustainability by using recyclable or biodegradable materials and reducing waste and carbon footprints.
| PowerPoint PPT presentation | free to download
The ACE, WARP, and X-band software applications are entirely EO-1 specific. ... rebooting from protected EEPROM or writeable EEPROM using hardware discrete ...
| PowerPoint PPT presentation | free to view
Postal Inspectors. Postal Inspectors protect the Postal Service, its employees ... United States Postal Inspection Service. http://usps.com/postalinspectors ...
| PowerPoint PPT presentation | free to view
Description: Cloud-based file transfer software – built with regulatory compliance and security in mind. Partner with Sharetru and share with confidence.
| PowerPoint PPT presentation | free to download
n : the co-option of another person's personal information (e.g., name, social ... Camera phones. Software tools. Credit card 'skimming' ATM spy cameras ' ...
| PowerPoint PPT presentation | free to view
To create a logo for your brand, first decide on the type of design that fits your brand, such as wordmark, lettermark, emblem, or abstract. Once you have your design, use graphic design software like Adobe Illustrator or Canva to convert it into a PDF format. It is important to trademark your logo to legally protect your brand identity. A logo is a visual symbol of your brand, not a watermark, and is crucial for branding and marketing. By following these steps, you can make a unique logo that effectively represents your brand.
| PowerPoint PPT presentation | free to download
Read here the latest Market Insights on “Digital signature software market” published by CMI research team.
| PowerPoint PPT presentation | free to download