Clouded PowerPoint PPT Presentations
All Time
Recommended
Cloud security, often known as cloud computing security, is a branch of cybersecurity that focuses on protecting cloud computing platforms. Cloud security refers to the entire bundle of technology, protocols, regulations, and best practices that secure cloud computing environments, cloud-based applications, and cloud-based data. Cloud security, to put it simply, is the discipline of defending cloud-based data, applications, and infrastructure against cyber threats.
| PowerPoint PPT presentation | free to download
Cloud Computing has been a game-changer for businesses of all sizes, but especially for small and medium businesses. Cloud Computing can help you improve your bottom line. With Cloud Backup Solutions, you can lower your IT costs, increase your sales productivity, and improve your marketing campaigns.
| PowerPoint PPT presentation | free to download
Cloud applications are the talk of the town. We often come across terms like cloud-enabled applications and cloud-native applications. The apps initially created to run on-premises but moved to the cloud are called cloud-enabled applications. The applications born on the cloud and designed for a cloud computing environment are called cloud-native apps. They are apt for both public and private clouds and incorporate the concept of DevOps, Microservices, and Containers. Cloud-native development is a way to increase the velocity of your business to take advantage of automation, scalability, and technologies like Kubernetes, which the cloud offers. To know more about cloud migration best suited for your business, reach out to us at: https://www.flentas.com/services/cloud-migration
| PowerPoint PPT presentation | free to download
iFCloud is a secure place in the cloud to easily store, access, and collaborate files from anywhere, anytime.
| PowerPoint PPT presentation | free to download
Clouds are a massive pool of virtualized resources such as hardware, development platforms, and easily usable and accessible services.
| PowerPoint PPT presentation | free to download
Cloud computing is the process of storing, accessing, and managing large amounts of data and software programs through the internet. Because the program and data are stored in global data centers, you can utilize it without using your computer’s hard disc.
| PowerPoint PPT presentation | free to download
iFCloud is a secure place in the cloud to easily store, access, and collaborate files from anywhere, anytime.
| PowerPoint PPT presentation | free to download
The Google Cloud Platform is simply another high-quality offering from Google. As the most well-known name in the Internet sector, Google entered the cloud race in 2011, after AWS and Azure, the current leaders. GCP has grown at an astounding rate since then, and GCP is now used by the majority of Fortune 500 organizations for their cloud needs.
| PowerPoint PPT presentation | free to download
Cloud computing has grown in importance as technology advances and becomes a more integral part of our daily lives. There are many cloud providers to choose from like AWS, Microsoft Azure, GCP, and more. However, Google Cloud Platform (GCP) is a widely used cloud computing platform for several reasons, such as its convenient, easy-to-use tools and services.
| PowerPoint PPT presentation | free to download
There are many threats to cloud security. The main treats arise from account hijacking, data breaches, inadequate cloud security architecture and strategy, insecure interfaces and APIs, insider threats, limited visibility with regard to cloud usage etc.
| PowerPoint PPT presentation | free to download
iFCloud is a secure place in the cloud to easily store, access, and collaborate files from anywhere, anytime.
| PowerPoint PPT presentation | free to download
iFCloud is a secure place in the cloud to easily store, access, and collaborate files from anywhere, anytime.
| PowerPoint PPT presentation | free to download
Various terms are used in cloud technology related services. Hence, it becomes important to know these terms.
| PowerPoint PPT presentation | free to download
To bridge that gap, the (ISC)2 and the Cloud Security Alliance (CSA) teamed up to design the Certified Cloud Security Professional (CCSP) certification, which verifies cloud security professionals’ knowledge and skills while also providing the education needed to provide adequate security in the cloud.
| PowerPoint PPT presentation | free to download
iFCloud is a secure place in the cloud to easily store, access, and collaborate files from anywhere, anytime.
| PowerPoint PPT presentation | free to download
"espousal of Cloud Telephony by small businesses is on the rise and that’s no surprise. With limited investment and resources, small businesses do want to have enough access to the best communication possible with their customers. Each and every call you get might become a potential customer when you’re leading a small business."
| PowerPoint PPT presentation | free to download
iFCloud is a secure place in the cloud to easily store, access, and collaborate files from anywhere, anytime.
| PowerPoint PPT presentation | free to download
The term “Cloud” refers to a collection of services that are meant to offer a cost-effective solution to businesses in order to aid them in increasing their capacity and functionality with regard to their IT services. There are different Cloud Deployment Models and Cloud Service Models.
| PowerPoint PPT presentation | free to download
Rather than owning their own computing infrastructure or data centers, companies can rent access to anything from applications to storage from a cloud service provider. https://www.acem.edu.in/
| PowerPoint PPT presentation | free to download
The Certified Cloud Security Professional Certification, or CCSP, is a joint certification from (ISC)2 and the Cloud Security Alliance (CSA).
| PowerPoint PPT presentation | free to download
The term Cloud hosting refers to creating, manipulating, configuring and finally accessing the websites and applications online. It also provides online data storage and infrastructure to the users. Cloud hosting is the combination of hardware and software computing resources that deliver in the form of network services.
| PowerPoint PPT presentation | free to download
The Certified Cloud Security Professional Certification or CCSP, is a credential offered by (ISC)2 and the Cloud Security Alliance (CSA) in collaboration. For information security practitioners who wish to specialise in cloud computing security, the CCSP is an excellent credential to obtain.
| PowerPoint PPT presentation | free to download
Go2market’s mobile cloud call center is a mobile-accessible platform for maintaining customer calls and interaction. The mobile call center is an extended version of cloud call centers yielding more scalability, reliability & flexibility.
| PowerPoint PPT presentation | free to download
The term Cloud hosting refers to creating, manipulating, configuring and finally accessing the websites and applications online. It also provides online data storage and infrastructure to the users. Cloud hosting is the combination of hardware and software computing resources that deliver in the form of network services.
| PowerPoint PPT presentation | free to download
Cloud computing, like the Covid-19 virus, is all around these days, but in a good way
| PowerPoint PPT presentation | free to download
iFCloud is a secure place in the cloud to easily store, access, and collaborate files from anywhere, anytime.
| PowerPoint PPT presentation | free to download
Information security has become one of the prominent concerns in the modern century. The adoption of cloud computing is increasing exponentially, and so is the dependence of businesses on technology.
| PowerPoint PPT presentation | free to download
Tally cloud is a service which unites the area of your tally and knowledge in high speed powerful virtual machines, this application is distributed using RDP protocol which allows you to get remote working plus easy access in any location or time most of the companies who have many branches want to get access to the tally on cloud.Get More Information about Tally On Cloud.
| PowerPoint PPT presentation | free to download
Get High-Performance Managed cloud computing services from 365Solution. We are a trusted Microsoft cloud partner in the UK. Our services include office365, PowerBI, Azure, EMS & Dynamic 365.
| PowerPoint PPT presentation | free to download
The wall businesses is moving towards the cloud, and we are gradually creating a cloud-native based world. Companies are looking to take advantage of this, and to do this, they must understand how the cloud native service industry world and the ebbs and flows of the industry. Here are the top cloud-native trends for 2021. https://bit.ly/3hmLLTt
| PowerPoint PPT presentation | free to download
Cloud computing is bringing about a paradigm shift by allowing IT administrators to handle infrastructure as a single layer from which they can provide services to users more quickly and cost-effectively.
| PowerPoint PPT presentation | free to download
Cloud hosting is a technology which uses central remote servers through the internet in order to operate and maintain data and applications. Cloud hosting helps to allow its users to use cloud-based applications without sharing any personal information and without providing access to any personal files at any device which has internet connectivity.
| PowerPoint PPT presentation | free to download
Multisoft Viratul Academy offers Cloud Computing Online Certification Training, Amazon Marketplace Web Services Online Training, AWS SysOps Online Certification Training, AWS Solutions Architect Associate Level Online Certification Training, Salesforce (Admin + Developer) Online Certification Training, Salesforce® App Builder (DEV 401) Online Certification Training, and 20 more. https://www.multisoftvirtualacademy.com/cloud-computing/
| PowerPoint PPT presentation | free to download
Myths about cloud hosting persist even after so many years. These myths have the potential to stifle business growth. However, this blog is useful in dispelling such myths and allows you to focus on your business rather than on such myths.
| PowerPoint PPT presentation | free to download
Cloud computing is Internet-based computing, whereby shared resources, software, and information are provided to computers and other devices on demand, like the electricity grid.
| PowerPoint PPT presentation | free to download
CompTIA is the world’s leading provider of vendor-neutral certifications. It has been providing 16 certifications in domains such as PC Support, Linux, Networking, Servers, and others for the past 15 years and is dedicated to constantly enhancing the service it provides to the industry. https://www.infosectrain.com/blog/securing-the-cloud-with-the-new-comptia-cloud-certification/
| PowerPoint PPT presentation | free to download
Avail Foundations of IBM Cloud V1 - C1000-039 - Course from Authorized IBM Global Training Partner Global Knowledge Technologies.
| PowerPoint PPT presentation | free to download
Jamcracker Hybrid Cloud Management provides a unified cloud management solution to integrate the disparate cloud environments. Allows you to control your cloud resources from both Public & Private cloud platforms with automation, orchestration, policy enforcement and management tools.
| PowerPoint PPT presentation | free to download
Customized Cloud ERP Software & System for your Business - Best Cloud ERP Solution
| PowerPoint PPT presentation | free to download
In depth and exhaustive ISO 27001 Checklist covers compliance requirements on Cloud Computing. The Checklist on cloud security Contains downloadable file of 3 Excel Sheets having 499 checklist Questions, complete list of Clauses, and list of 114 Information Security Controls, 35 control objectives, and 14 domains. To obtain the Checklist click/copy the URL link below- https://www.isocertificationtrainingcourse.org/online-store/ISO-27001-Checklist-ISO-27001-Audit-Checklist-ISO-27001-Compliance-checklist-c28241136
| PowerPoint PPT presentation | free to download
These computers can be personal computers or network servers; they can be public or private. This cloud of computers extends beyond a single company or enterprise.
| PowerPoint PPT presentation | free to download
This PPT represents the new features of Acronis Cyber Backup Cloud and Acronic Cyber Protect Cloud.
| PowerPoint PPT presentation | free to download
Cloud ERP Software in Ahmedabad - Best Web based ERP Software in Ahmedabad
| PowerPoint PPT presentation | free to download
Cloud Data Loss Prevention (Cloud DLP) offers many benefits with regard to protecting sensitive data in order to lower the chances of data theft.
| PowerPoint PPT presentation | free to download
Government Community Cloud ensures seamless collaboration between government officials and public, serving government services to be accessible at one place. Here is how GCC is contributing to Digital India Mission.
| PowerPoint PPT presentation | free to download
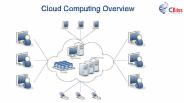
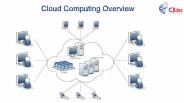
In this presentation, you view the Cloud computing overview. Cloud computing can be called storage and access to data over the Internet instead of your computer's hard drive.
| PowerPoint PPT presentation | free to download
Different types of clouds
| PowerPoint PPT presentation | free to download
Read here the latest Market Insights on “Cloud Based Language Learning Market” published by CMI research team.
| PowerPoint PPT presentation | free to download
Cloud computing has enhanced the education sector by drastically transforming it from student email and mission-critical business to distance learning platforms and ERP portals. Let's dive in to know more about it.
| PowerPoint PPT presentation | free to download
Read this white paper to learn more about hybrid cloud automation, its benefits, use cases, and the factors to be considered while automating it.
| PowerPoint PPT presentation | free to download
if you are still lost in piles of papers and your local office hard disk and computer then it is high time to move on cloud and capitalize the growing opportunities of the highly advanced and fruitful platform.
| PowerPoint PPT presentation | free to download
Cloud computing can be called storage and access to data over the Internet instead of your computer's hard drive. This means that you do not have access to the data from your computer's hard drive or from a dedicated computer network. in this presentation, you view the Cloud computing overview.
| PowerPoint PPT presentation | free to download
Our developers offer application and software development services in Denver, CO. We can help with cloud computing, automation, and more.
| PowerPoint PPT presentation | free to download
Nexii IT Labs is an IT company with expertise in storage, virtualization, automation, DevOps and cloud. With offices in Hyderabad and Bangalore in India, Nexii Labs is seeking to expand its footprint by providing end-to-end business solutions that through product development, IT staffing and services.
| PowerPoint PPT presentation | free to download
Cloud storage is defined as service that renders users the leverage to store, maintain, manage, and collaborate data or content on the cloud or a single ecosystem. Instead of storing or managing data on a local device or personal computer, it can be stored and accessed online through a network of remote servers.
| PowerPoint PPT presentation | free to download
Customized Cloud ERP Software System in India - Find Best Customized Cloud ERP Solution
| PowerPoint PPT presentation | free to download