Ciphers PowerPoint PPT Presentations
All Time
Recommended
Blowfish, RC5 Block Ciphers M. Sakalli, Marmara Univ. Chapter 6 of Cryptography and Network Security by William Stallings Modified from the original s of Lawrie ...
| PowerPoint PPT presentation | free to view
Blowfish, RC5 Block Ciphers M. Sakalli, Marmara Univ. Chapter 6 of Cryptography and Network Security by William Stallings Modified from the original s of Lawrie ...
| PowerPoint PPT presentation | free to download
Lecture 07 Subject: Network Security
| PowerPoint PPT presentation | free to download
Intro ... Block Ciphers
| PowerPoint PPT presentation | free to download
Title: No Slide Title Author: Muddy Shoes Software, LLC Last modified by: CSD Created Date: 6/17/1995 11:31:02 PM Document presentation format: On-screen Show
| PowerPoint PPT presentation | free to view
Generalization of one-time pad. Trade provable security for practicality ... ORYX weak cipher, uses shift registers, generates 1 byte/step ...
| PowerPoint PPT presentation | free to download
Write the keyword over the plain text, and then immediately after the keyword, ... a keyword to all of the plain text, you are going to need a tabula recta. ...
| PowerPoint PPT presentation | free to view
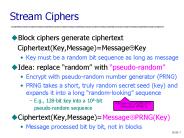
Encrypt with pseudo-random number generator (PRNG) ... To use RC4, usually prepend initialization vector (IV) to the key. IV can be random or a counter ...
| PowerPoint PPT presentation | free to download
Cut and paste is still possible, but more complex (and will cause garbles) ... CN 1 = E(CN 2 PN 1, K) = MAC. MAC sent along with plaintext ...
| PowerPoint PPT presentation | free to download
Codes and Ciphers By the end of this session you will be able to:
| PowerPoint PPT presentation | free to download
If you ask Batman's nemesis, Catwoman, how many cats she has, she answers with a ... How many cats does Catwoman have? In right triangle ABC, with right angle ...
| PowerPoint PPT presentation | free to download
Wheel order The choice of rotors and their order. Initial position of the rotors Chosen by operator, changed for each message ...
| PowerPoint PPT presentation | free to view
Clock-controlled Generators. An LFSR can be clocked by the output of another LFSR. This introduces an irregularity in clocking of the first LFSR, ...
| PowerPoint PPT presentation | free to view
Eve, in theory, can break the PKC they used even though doing so is difficult. ... breaks it, random bits Alice & Bob collected disappeared and Eve can not decrypt ...
| PowerPoint PPT presentation | free to view
Scrambled alphabet starts with keyword (duplicate letters eliminated) followed ... Susceptible to frequency analysis, with guesses at keyword when some letters are ...
| PowerPoint PPT presentation | free to view
Codes, Ciphers, and Cryptography-Ch 3.2 Michael A. Karls Ball State University
| PowerPoint PPT presentation | free to view
Codes and Ciphers. By the end of this session you will ... Practise Questions. 00010. 11111. 10011. 00101. Round 4- Binary Challenge. Round 4- Binary Challenge ...
| PowerPoint PPT presentation | free to view
Encrypting with Block Ciphers CS 470 Introduction to Applied Cryptography Instructor: Ali Aydin Selcuk How to Encrypt with a Block Cipher? Electronic Codebook (ECB ...
| PowerPoint PPT presentation | free to download
... by a different alphabet stream of characters shifted ... is an arrangement of the original order of letters or numbers. E.g. ... of letters from ...
| PowerPoint PPT presentation | free to view
Block cipher is an encryption function that works on fixed size blocks ... Horst Feistel, who came to U.S. in 1934 from Germany, developed Lucifer cipher ...
| PowerPoint PPT presentation | free to view
Write the keyword below the alphabet and fill in the rest of the ... Monoalphabetic and some substitutions for words or phrases. Mary, Queen of Scots. Review ...
| PowerPoint PPT presentation | free to view
Lecture 08 Subject: Network Security
| PowerPoint PPT presentation | free to download
Giovan Batista Belaso. Otherwise unknown. Small booklet in 1553 ... Giovanni Batista Porta. Polyalphabetic cipher. Combined elements of. Alberti scrambled alphabet ...
| PowerPoint PPT presentation | free to view
Section 2.3: Substitution Ciphers Practice HW from Barr Textbook (not to hand in) p. 92 # 1, 2 # 3-5 (Use Internet Site) A substitution cipher is a cipher in which ...
| PowerPoint PPT presentation | free to download
Block Ciphers After the DES CS 470 Introduction to Applied Cryptography Instructor: Ali Aydin Selcuk After the DES DES was designed for h/w; slow in s/w.
| PowerPoint PPT presentation | free to download
In 1854, Charles Babbage used this idea to guess the length of a keyword for a Vigen re cipher! ... Babbage told Thwaites that his cipher was the Vigen re cipher. ...
| PowerPoint PPT presentation | free to view
Example 1: Encipher CHUCK NORRIS IS A TOUGH GUY using a rail fence cipher. Solution: Note To decipher a rail fence cipher, we divide ...
| PowerPoint PPT presentation | free to download
byte re-ordering. One round. S(x) = l(l'(x)-1) in GF(28), where l,l' are GF(2)-linear. and the MDS matrix and byte re-ordering are GF(28)-linear. In this talk: ...
| PowerPoint PPT presentation | free to download
Ciphers and Other fun Things. By Mavis Mather. Outline. Problem. Background. Approach. Task List ... Compile a list what's in a good cipher. Implementation of ...
| PowerPoint PPT presentation | free to view
... 'Wikipedia, the free encyclopedia. http://en.wikipedia.org/wiki ... Wikipedia, the free encyclopedia. http://en.wikipedia.org/wik/Ciphes. (Retrived6 DEC. ...
| PowerPoint PPT presentation | free to view
The algorithms EAK and DAK for fixed K can be considered as transformations of the set An. EAK(DAK(m0m1...mn-1))=m0m1...mn-1. DAK(EAK(m0m1...mn-1))=m0m1...mn-1. ...
| PowerPoint PPT presentation | free to download
Breaking the Vigen re Cipher. Suppose we have intercepted the following ciphertext (handout) ... Thwaites challenged Babbage to break his cipher. Babbage never ...
| PowerPoint PPT presentation | free to view
The Affine Cipher. Cryptography, Jerzy Wojdylo, 5/4/01. Classical Cryptography ... The Affine Cipher. Let P = C = Z26, let. K = {(a, b) Z26 Z26 | gcd(a, 26) = 1} ...
| PowerPoint PPT presentation | free to view
Best Affine Approximation Attack. Correlation Attack by Siegenthaler ... Best Affine Appoximation Attack ... by using an affine approximation of the combination ...
| PowerPoint PPT presentation | free to view
A key is selected by A and sent to B physically. A third party selects a key and sends it to A and B physically. ... Random number generators (cont. ...
| PowerPoint PPT presentation | free to download
S-P networks are based on the two primitive cryptographic operations ... Horst Feistel devised the feistel cipher. based on concept of invertible product cipher ...
| PowerPoint PPT presentation | free to view
The WG cipher has. been designed to produce keystream with guaranteed randomness properties, ... multivariate equation of low degree this complexity can be ...
| PowerPoint PPT presentation | free to view
Blowfish. a symmetric block cipher designed by ... Blowfish Encryption. uses two primitives: addition & XOR ... Very few cryptoanalysis results on blowfish ...
| PowerPoint PPT presentation | free to view
Pilling-Up. If the two random variables are independent, then ... Pilling-Up. By combining representations of S-Boxes we can eliminate some intermediate steps. ...
| PowerPoint PPT presentation | free to view
differential cryptanalysis and its extensions and variants. multiset cryptanalysis. other cryptanalysis. Practical implementation. Design improvement. 27. Conclusion ...
| PowerPoint PPT presentation | free to download
Electronic Code Book (ECB) How to use a block cipher to encrypt a large message? M2 ... padi=e(padi-1,key) k-bit shifting (see pic) advantages ...
| PowerPoint PPT presentation | free to view
Section 2.2: Affine Ciphers; More Modular Arithmetic Shift ciphers use an additive key. To increase security, we can add a multiplicative parameter.
| PowerPoint PPT presentation | free to view
Oregon State University. A Comparative Study of New Block Ciphers. Min Zhuo. ECE 575 ... Oregon State University. Frog Overview. an unorthodox structure, 8 iterations ...
| PowerPoint PPT presentation | free to view
They want to encrypt their message so Trudy who also happens to know a lot about ... Horst Feistel, working at IBM Thomas J Watson Research Labs devised a suitable ...
| PowerPoint PPT presentation | free to view
Methods have been developed to disguise and break secret messages. 3 ... A code is a form of secret communication in which a word or phrase is replaced ...
| PowerPoint PPT presentation | free to view
( no plaintext attack should be better than brute force.) 3. ... This reduces the work required for a brute-force attack from 2120 steps to 2119 steps. ...
| PowerPoint PPT presentation | free to view
Learn about codes and ciphers! Create and decipher coded messages! Crack the code in secret spy cases! CRYPTOLOGY STATION. Ages 8 ...
| PowerPoint PPT presentation | free to download
Section 2.2: Affine Ciphers; More Modular Arithmetic Practice HW (not to hand in) From Barr Textbook p. 80 # 2a, 3e, 3f, 4, 5a, 7, 8 9, 10 (Use affinecipherbreaker ...
| PowerPoint PPT presentation | free to download
Lemma 3.1 (Piling-up lemma) : Let denote the bias of the random variable . Then ... Using Piling-up lemma, has bias equal to 23(1/4)(-1/4)3=-1/32. ...
| PowerPoint PPT presentation | free to view
Doubling the Block Length of a Cipher. Build 2n-bit block cipher using n-bit components ... Patarin [Pat04]: 6-round has O(2n)-sec. ( for CCA) ...
| PowerPoint PPT presentation | free to view
John A Clark and Susan Stepney. Dept. of Computer Science. University of York, UK ... Vernam Cipher works by generating a random bit stream and then XORing that ...
| PowerPoint PPT presentation | free to view
Definition: The Totient function, represented by f(n), is defined as the number ... Explanation: The Totient theorem is a generalized version of Fermat's Little ...
| PowerPoint PPT presentation | free to view
Extending Higher-order Integral: An Efficient Unified Algorithm of Constructing Integral Distinguishers for Block Ciphers Wentao Zhang1, Bozhan Su2, Wenling Wu1
| PowerPoint PPT presentation | free to view
Chapter 2 Symmetric Ciphers Lecture s by Lawrie Brown Modifications by Nguyen Cao Dat * In the late 1960s, IBM set up a research project in computer cryptography ...
| PowerPoint PPT presentation | free to view
Dado un tama o de bloque n y un tama o de clave k ... dados h y x, es f cil calcular h(x) sirve como una representaci n compacta del input ...
| PowerPoint PPT presentation | free to view
one of the most widely used types of cryptographic algorithms ... Horst Feistel devised the feistel cipher. based on concept of invertible product cipher ...
| PowerPoint PPT presentation | free to view