Algortihms PowerPoint PPT Presentations
All Time
Recommended
10h45 Adaptive programming with hierarchical multiprocessor tasks ... Choice is performed at runtime, depending on resource idleness ...
| PowerPoint PPT presentation | free to download
... framework is the most powerful - advised to be used to improve algortihms and set the cuts. ... Make a cuts scan and find a working' point for. each defect ...
| PowerPoint PPT presentation | free to view
Title: PowerPoint Presentation Author: Sendhoff Last modified by: Bernhard Sendhoff Created Date: 3/22/2003 6:19:35 PM Document presentation format
| PowerPoint PPT presentation | free to download
Lack of expertise and time consuming. Content-based Lecture Video ... data is possible to extract using a foreground model to compare against new content ...
| PowerPoint PPT presentation | free to view
Title: Microarray Data Analysis Author: Kath Last modified by: Janet Murray Created Date: 10/14/2003 5:52:40 PM Document presentation format: On-screen Show
| PowerPoint PPT presentation | free to download
Title: CPSC 367: Parallel Computing Author: Oberta A. Slotterbeck Last modified by: jbaker Created Date: 8/26/2005 1:18:57 AM Document presentation format
| PowerPoint PPT presentation | free to download
Better performing algorithms produce more effective labels. If high performance labeling algorithms can be identified, the effectiveness of ...
| PowerPoint PPT presentation | free to view
If not, at least we have pruned all its supersets. Jump ahead schemes: Bayardo's MaxMine ... Downward closure (frequent sets) is a pruning property ...
| PowerPoint PPT presentation | free to download
Data Mining Tutorial Tomasz Imielinski Rutgers University What is data mining? Finding interesting, useful, unexpected Finding patterns, clusters, associations ...
| PowerPoint PPT presentation | free to download
Title: Pr sentation PowerPoint exemple de r alisation Author: Rohmer Jeremy Last modified by: Rohmer Jeremy Document presentation format: Affichage l' cran (4:3)
| PowerPoint PPT presentation | free to view
This project uses Java to create a functional traffic simulation, focusing on ... They have a restricted amount of commons area on which to graze the cattle. ...
| PowerPoint PPT presentation | free to download
The problem of finding the prime factors of large composite numbers has always ... The Pollard 'rho' algorithm which under plausible assumptions has expected run ...
| PowerPoint PPT presentation | free to view
Introduction of conflict-free and shortest time AGV routing by Broadbent et al. ... Linear path topology basic type of path layouts ...
| PowerPoint PPT presentation | free to view
... fundementally unique properties. ... Sounds familiar? Shor's Algoritm (cont'd) Pick a random ... it possesses unique properties and therefore challanges some ...
| PowerPoint PPT presentation | free to view
Graph Coloring and Chromatic Number Definitions. Let G=(V,E) be ... have different color. ... Optimization graph coloring problem (Find chromatic number for ...
| PowerPoint PPT presentation | free to view
... 1.1.0 available for interested users athttp://hea-www.harvard.edu/~fap/APPHOT ... The ds9 image display program can be used to launch user-defined analysis tasks ...
| PowerPoint PPT presentation | free to download
What is described here actually works in practice, but the implementation is not ... a a set of ( set of algo configurations) corresponding to a specified few TCKs ...
| PowerPoint PPT presentation | free to download
Deux axes : *Traitement du signal et de donn es imparfaites ... Position anatomique de lectrodes. Bouff e diaphragmatique. IBISC valuation AERES 18 ...
| PowerPoint PPT presentation | free to view
Title: CPSC 367: Parallel Computing Author: Oberta A. Slotterbeck Last modified by: jbaker Created Date: 8/26/2005 1:18:57 AM Document presentation format
| PowerPoint PPT presentation | free to download
Lecture 9 Computer Game Design AI and Finite States Machines
| PowerPoint PPT presentation | free to view
... savings if k ' n. ... e-Nash, need t of the order poly(e,2-k) & running time ~ poly(n,1/e,2k) ... No guarantees for the running time. GRAPHICAL GAMES: A SURVEY ...
| PowerPoint PPT presentation | free to view
Applied Fractional Calculus Workshop Series Zhigang, Lian/Link MESA (Mechatronics, Embedded Systems and Automation)Lab School of Engineering, University of California ...
| PowerPoint PPT presentation | free to download
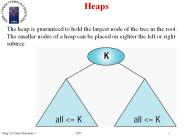
Heaps The heap is guaranteed to hold the largest node of the tree in the root. The smaller nodes of a heap can be placed on eighter the left or right
| PowerPoint PPT presentation | free to download
What is a compiler? - Learning Management System - Virtual ... ... Parsing
| PowerPoint PPT presentation | free to view
Preference Elicitation in Combinatorial Auctions Tuomas Sandholm Carnegie Mellon University Computer Science Department (papers on this topic available via www.cs.cmu ...
| PowerPoint PPT presentation | free to download
Top-k Query Processing Optimal aggregation algorithms for middleware Ronald Fagin, Amnon Lotem, and Moni Naor + Sushruth P. + Arjun Dasgupta
| PowerPoint PPT presentation | free to download
Instructor Neelima Gupta ngupta@cs.du.ac.in
| PowerPoint PPT presentation | free to download
A concept (class) is defined by its set of exemplars: ... BOLERO - medical diagnosis. Althoff/Wess/Richter 93. PATDEX - technical diagnosis ...
| PowerPoint PPT presentation | free to download
Preference Elicitation in Combinatorial Auctions: An Overview Tuomas Sandholm [For an overview, see review article by Sandholm & Boutilier in the textbook ...
| PowerPoint PPT presentation | free to download
Preference Elicitation in Combinatorial Auctions: An Overview Tuomas Sandholm [For an overview, see review article by Sandholm & Boutilier in the textbook ...
| PowerPoint PPT presentation | free to download
Main collaborators: The people from Bern who developed the Data Collection ... Burckart & Giovanna Leeman (CERN), Andrea Negri (Pavia), Serge Suskov (Barcelona) ...
| PowerPoint PPT presentation | free to download
In a locally distributed system, there is a good ... Case Studies. The V-System. The Sprite system. Condor system. The Stealth distributed scheduler ...
| PowerPoint PPT presentation | free to download
Andy Turner On MoSeS
- Andy Turner On MoSeS Andy Turner http://www.geog.leeds.ac.uk/people/a.turner/
Andy Turner On MoSeS Andy Turner http://www.geog.leeds.ac.uk/people/a.turner/
| PowerPoint PPT presentation | free to download
Semantic methods consider special properties of the type of information ... temporal methods compress data in frames over time ...
| PowerPoint PPT presentation | free to download
Top-k Query Processing Optimal aggregation algorithms for middleware Ronald Fagin, Amnon Lotem, and Moni Naor + Sushruth P. + Arjun Dasgupta NRA What if we also want ...
| PowerPoint PPT presentation | free to download
On discovering gliders and glider guns ... This evolutionary algorithm searches for guns emitting a specific glider. ... Glider guns can be used to duplicate ...
| PowerPoint PPT presentation | free to download
Ass. Rules. Episodes. Text Mining. 02.11. 09.11. Clustering. KDD Process. Home Exam. 23.11. ... Most of the sequences are large (85%) = next round is k 5 ...
| PowerPoint PPT presentation | free to download
Twenty years of analysis, modeling and refinement. Splitting the microsecond ... Survey nearby network environment to construct a list of suitable servers ...
| PowerPoint PPT presentation | free to download
A conformational transition from oxygen binding to oxygen releasing protein. ... a very large time step: Formalism and numerical examples', J. Chem. Phys. ...
| PowerPoint PPT presentation | free to view
Title: Exploiting Transition Locality in Automatic Verification Author: Enrico Tronci Last modified by: enrico Created Date: 7/14/2001 7:48:53 PM Document ...
| PowerPoint PPT presentation | free to download
Many multimedia applications are emerging which use multiple audio/video sensors ... as laptops, PDAs, tablets, cellular phones,and camcorders have become pervasive. ...
| PowerPoint PPT presentation | free to download
finance fashion. banking telecommunication. work music. business channel ... requires a lot of work'; 'no schools offer graduate study in interior design' ...
| PowerPoint PPT presentation | free to view
Minimum Spanning Tree Property. 5. Proof of Property ... Return the minimum-spanning tree T. ... Output: A minimum spanning tree T for G. pick any vertex v of G ...
| PowerPoint PPT presentation | free to download
Well over 100,000 NTP peers deployed in the Internet and ... Tutorials, hints and bibliographies. Links to other NTP software. 6/3/09. 29. Further information ...
| PowerPoint PPT presentation | free to download
Usually consists of two subproblems (Han and Kamber, 2001) ... These two subproblems are soleved iteratively until new rules no more emerge ...
| PowerPoint PPT presentation | free to download
System clock is disciplined in time and frequency using an adaptive algorithm ... Over 100,000 Internet secondary servers and clients all over the world ...
| PowerPoint PPT presentation | free to download
An Efficient Algorithm for Large-Scale Detection of Protein ... Mij - probability of ... by favoring more probable walks over less probable walks ...
| PowerPoint PPT presentation | free to view
Trust requires a belief and a commitment ... MoleTrust (Massa and Avesani) TidalTrust (Golbeck) 10 /39. Advogato. Levien 2003. Attack resistant ...
| PowerPoint PPT presentation | free to view
Extract tabular data from all such lists in an unsupervised and domain-independent ... A period ('.') is used both as a delimiter and to terminate abbreviations ...
| PowerPoint PPT presentation | free to view
Provide an intuitive feel for what NN's are and problems for ... Encoding of data can be a 'creative' endeavor. Ensemble Approach. Baysian Networks. Fuzzy NN ...
| PowerPoint PPT presentation | free to view
Connection Establishment in BFCP. draft-ietf-xcon-bfcp-connection-00.txt ... Definition of Error Specific Details for Error Code 10 (DIGEST Attribute Needed) DIGEST ...
| PowerPoint PPT presentation | free to download
Universit degli Studi di Siena. Dottorato di Ricerca in Ingegneria ... Leonardo Rigutini Dipartimento Ingegneria ... used the Winnow (ANN) and Rocchio ...
| PowerPoint PPT presentation | free to view
Programming for Image Processing/Analysis and Visualization using. The Visualization Toolkit ... Custom libraries e.g. to read/write certain medical image formats ...
| PowerPoint PPT presentation | free to download
Ronald Fagin, Amnon Lotem, and Moni Naor ... Example Fagin's Algortihm. Read all grades of an object once seen from a sorted access ...
| PowerPoint PPT presentation | free to view
Belinda Wu is working on the applications beginning with a Toy Model for Leeds ... 3 cells. Alternative Futures ASAP Research Cluster Seminar 16th November 2005 ...
| PowerPoint PPT presentation | free to download