Learning outcomes - PowerPoint PPT Presentation
1 / 25
Title:
Learning outcomes
Description:
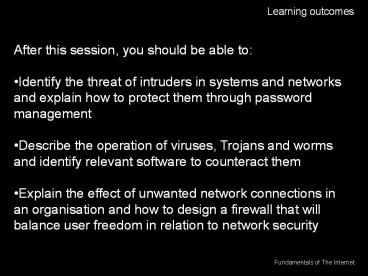
Learning outcomes After this session, you should be able to: Identify the threat of intruders in systems and networks and explain how to protect them through password ... – PowerPoint PPT presentation
Number of Views:73
Avg rating:3.0/5.0
Title: Learning outcomes
1
Learning outcomes
- After this session, you should be able to
- Identify the threat of intruders in systems and
networks and explain how to protect them through
password management - Describe the operation of viruses, Trojans and
worms and identify relevant software to
counteract them - Explain the effect of unwanted network
connections in an organisation and how to design
a firewall that will balance user freedom in
relation to network security
2
Taxanomy of Malicious Programs
Malicious Programs
Need Host Program
Independent
Trapdoors
Logic Bombs
Trojan Horses
Viruses
Zombie
Worms
3
Definitions
- Trojan Horse - instructions in an otherwise good
program that cause bad things to happen (sending
your data or password to an attacker over the
net). - Logic Bomb - malicious code that activates on an
event (e.g., date, specific key sequence, absence
of a file etc ). - Trap Door (or Back Door) - undocumented entry
point written into code for debugging that can
allow unwanted users.
4
Definitions
- Virus - code that infects other executable files
by copying itself. - A Bacteria replicates until it fills all disk
space, or CPU cycles. - Payload - harmful things the malicious program
does, after it has had time to spread. - Worm - a program that replicates itself across
the network (usually riding on email messages or
attached documents (e.g., macro viruses). - Zombie a program that takes over other
Internet-attached computers to launch attacks
that are difficult to trace back to the original
creator of the program. Typically used in
Denial-of-Service Attacks
5
Virus Phases
Four different phases exist for a virus. However,
not all viruses have all of these four phases.
- Dormant phase - the virus is idle
- Propagation phase - the virus places an identical
copy of itself into other programs - Triggering phase the virus is activated to
perform the function for which it was intended - Execution phase the function is performed
6
Virus Protection
Have a well-known virus protection program,
configured to scan disks and downloads
automatically for known viruses.
Do not execute programs (or "macro's") from
unknown sources (e.g., PS files, Hypercard files,
MS Office documents). Do not download .dll,
.lib., .hlp, .obj files from unknown sources.
Avoid the most common operating systems and email
programs, if possible.
7
Virus Structure
Increases the length of the host program !!
And, this segment will be the same in all
infected files !! It is called the signature of
the virus.
8
A Compression Virus
9
Types of Viruses
- Parasitic Virus - attaches itself to executable
files as part of their code. Runs whenever the
host program runs. - Memory-resident Virus - Lodges in main memory as
part of the residual operating system. - Boot Sector Virus - infects the boot sector of a
disk, and spreads when the operating system boots
up (original DOS viruses). - Stealth Virus - explicitly designed to hide from
Virus Scanning programs. Compression and
controlling disk I/O are the most common
techniques. - Polymorphic Virus - mutates with every new host
to prevent signature detection. It is achieved
either by randomly shuffling independent
instructions in the virus, or by adding
superfluous instructions, or by encryption.
10
Macro Viruses
- Microsoft Office applications allow macros to
be part of the document. The macro could run
whenever the document is opened, or when a
certain command is selected (Save File). - Platform independent.
- Infect documents, delete files, generate email
and edit letters.
11
Antivirus Approaches
1st Generation, Scanners searched files for any
of a library of known virus signatures. Checked
executable files for length changes. 2nd
Generation, Heuristic Scanners looks for more
general signs than specific signatures (code
segments common to many viruses). Checked files
for checksum or hash changes. 3rd Generation,
Activity Traps stay resident in memory and look
for certain patterns of software behavior (e.g.,
scanning files). 4th Generation, Full Featured
combine the best of the techniques above.
12
Advanced Antivirus Techniques
- Generic Decryption (GD)
- CPU Emulator
- Virus Signature Scanner
- Emulation Control Module
- If the virus is encrypted it will decrypt and
reveal itself. - Key question how long should a GD scanner run
each interpretation?
13
Firewall Design Principles
- Too many computers with different Operating
Systems exist in corporate networks today. - They all need Internet access.
- The firewall is inserted between the premises
network and the Internet - Aims
- Establish a controlled link
- Protect the premises network from Internet-based
attacks - Provide a single choke point
14
Firewall Characteristics
- Design goals
- All traffic from inside to outside must pass
through the firewall (physically blocking all
access to the local network except via the
firewall). - Only authorized traffic (defined by the local
security policy) will be allowed to pass. - The firewall itself is immune to penetration (use
of trusted system with a secure operating system).
15
Firewall Characteristics
Four general techniques
- User control
- Controls access to a service according to which
user is attempting to access it (may need
authentication procedures). - Behavior control
- Controls how particular services are used (e.g.
filter e-mail). - Service control
- Determines the types of Internet services that
can be accessed (such as FTP, HTTP) , inbound or
outbound. - Direction control
- Determines the direction in which particular
service requests are allowed to flow.
16
Types of Firewalls
- Three common types of Firewalls
- Packet-filtering routers
- Stateful Inspection Firewalls
- Application-level gateways
- Circuit-level gateway
17
Types of Firewalls
Packet-filtering Router
- Applies a set of rules to each incoming IP packet
and then forwards or discards the packet - Filter packets going in both directions
- The packet filter is typically set up as a list
of rules based on matches to fields in the IP or
TCP header - Two default policies (discard or forward)
18
Types of Firewalls
All these fields can be used in a packet filter
- Source and Destination IP address
- Source and Destination Port Numbers
- IP Protocol field, which defines the higher-level
protocol in the IP packet - MAC address in case there are more than one.
Packet filtering example
action src port dest port comment
block SPIGOT our hosts we dont trust these people
allow our hosts 25 connection to our SMTP port
19
Types of Firewalls
Stateful Inspection Firewalls
A traditional packet filter allows or denies
packet on an individual basis after analysing IP
and TCP packet headers in the arriving packet. A
stateful inspection firewall, on the other hand,
considers the status of ongoing TCP connections
in addition to the header information in the
arriving packets.
Example Stateful Furewall Connection State Table
Source Address Source Port Destination Address Destination Port Connection State
192.168.1.100 1030 210.9.88.29 80 Active
192.168.1.101 80 216.32.42.123 2552 Released
192.168.1.105 1990 192.168.1.6 79 Active
223.43.21.231 2112 192.168.1.6 80 Active
210.99.212.18 3321 192.168.1.6 80 Active
20
Types of Firewalls
Application-level Gateway (proxy)
- Also called proxy server
- Acts as a relay of application-level traffic
- Requires user authentication
- More secure than packet filtering and stateful
inspection - More processing overhead as well.
21
Types of Firewalls
Circuit-level Gateway
- Sets up two TCP connections
- Requires user authentication
- The gateway typically relays TCP segments from
one connection to the other without examining the
contents - The security function consists of determining
which connections will be allowed - Typically use is a situation in which the system
administrator trusts the internal users
22
Firewall Configurations
- In addition to the use of simple configuration of
a single system (single packet filtering router
or single gateway), more complex configurations
are possible. - A Bastion Host (means a well-fortified area)
serves as a platform for an application-level or
circuit-level gateway. - they use a secure operating system,
- only the essential services are installed
(including proxies for Telnet, DNS, FTP, SMTP,
and user authentication), - each proxy module is a very small software
package (fewer than 1000 lines) to minimise any
security flaw - each proxy is independent
- proxies have no disk access and they run as
nonprivileged users
23
Firewall Configurations
Screened host firewall system (single-homed
bastion host)
- Only packets from and to the bastion host are
allowed to pass through the packet filter - The bastion host performs authentication and
proxy functions - Both packet-level and application-level filtering
24
Firewall Configurations
Screened host firewall system (dual-homed bastion
host)
- Traffic between the Internet and other hosts on
the private network has to flow through the
bastion host - Even if the packet filter is compromised, the
private network is physically isolated from the
Internet by the Bastion host
25
Firewall Configurations
Screened-subnet firewall system
- Most secure configuration of the three
- An isolated sub-network is created between the
Internet and the private network - The private network is not visible to the
Internet - The Internet is not visible to the private network