Chapter 42 Key Distribution - PowerPoint PPT Presentation
1 / 14
Title:
Chapter 42 Key Distribution
Description:
Valid lifetime is based on the strength of the keys. 10/1/09. Secret Key Systems. 3 ... Channel. p,a? OK. Ja = 4. Jb = 1. 10/1/09. Secret Key Systems. 13 ... – PowerPoint PPT presentation
Number of Views:20
Avg rating:3.0/5.0
Title: Chapter 42 Key Distribution
1
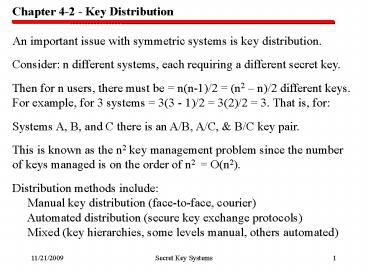
Chapter 4-2 - Key Distribution An important
issue with symmetric systems is key
distribution. Consider n different systems,
each requiring a different secret key. Then for
n users, there must be n(n-1)/2 (n2 n)/2
different keys. For example, for 3 systems 3(3
- 1)/2 3(2)/2 3. That is, for Systems A, B,
and C there is an A/B, A/C, B/C key pair.
This is known as the n2 key management problem
since the number of keys managed is on the order
of n2 O(n2). Distribution methods include
Manual key distribution (face-to-face,
courier) Automated distribution (secure key
exchange protocols) Mixed (key hierarchies,
some levels manual, others automated)
2
Key Distribution Manual methods are costly and
dont scale, but can be used effectively in a
mixed mode of distribution using a key
hierarchy American National Standards Institute
(ANSI) X9.17 uses a multi-level hierarchy of
keys.
System B
System A
KKM Keys
KKM Keys
Manually distribution, long life
KK Keys
KK Keys
Electronic distribution, medium life
DK Keys
DK Keys
Electronic distribution, short life
KKM keys are used to encrypt KK keys for
distribution (e.g., monthly) KK Keys are used to
encrypt DK (data) keys for distribution (e.g., a
single session or a single message) Valid
lifetime is based on the strength of the keys
3
Key Distribution - Diffie/Hellman Key Exchange A
completely new method for all electronic
distribution, actually became the first
asymmetrical (public) key system. Algorithm
proposed Dk1(Ek2(P) P That is, A plaintext
key (P above) could be encrypted (E) with a key
k2 and decrypted (D) with a key k1, where k1 and
k2 are different keys and where only one key had
to be kept secret. This meant one of the keys
could be sent over a network without compromising
the security of the encryption algorithm as long
as it is cryptographically hard to deduce k1
with knowledge of k2. The hard problem is
based on the difficulty of finding discrete logs.
4
Diffie/Hellman Key Exchange - Basics 1 Assume
some prime number p has a primitive root, say a,
and defines a set of numbers that are powers of
a mod p. These numbers generate all the integers
from 1 to p-1. That is a mod p, a2 mod p, a3
mod p, ..ap-1 mod p 0 is not generated since a
prime number has no factors other than 1 and
itself. 0 is not considered a prime number. The
generated list will not be monotonic in the order
numbers are generated. It will generate numbers
in some permuted order, but will generate the
complete set of numbers from 1 to p-1. Consider
the prime number p 17 and a 3
5
Diffie/Hellman Key Exchange - Basics 2 a mod p
3 mod17 3 i.e., 3/17
0, 3 a2 mod p 9 mod 17
9 a3 mod p 27 mod 17 10 a4 mod
p 81 mod 17 13 a5 mod p 243
mod 17 5 a6 mod p 729 mod 17
15 729/17 48, 15 a7 mod p 2187 mod
17 11 a8 mod p 6561 mod 17
16 a9 mod p 19683 mod 17 14 a10 mod p
59049 mod 17 8 a11 mod p 177147 mod
17 7 a12 mod p 531441 mod 17
4 a13 mod p 1594323 mod 17 12 a14 mod p
4782969 mod 17 2 a15 mod p 14348907 mod
17 6 a16 mod p 43046721 mod 17 1
Notice the set is complete up to p - 1
6
Diffie/Hellman Key Exchange - Basics 3 Result
For any integer b lt p and primitive root a for a
prime p, an exponent k can be determined such
that b ak mod p with 0 lt k lt (p-1) (i.e.,
it is a member of the set) 16 a8 mod 17 (p
17, k lt p) The exponent k is called the index of
b. It is also called the discrete logarithm of b
for a mod p. Diffie/Hellman key exchanges uses
two publicly known numbers, a prime number p and
an integer primitive root of p, say a (same a)
and a secret private integer I. Assume Alice
Bob want to exchange keys. They publicly agree on
p and a.
7
Diffie/Hellman Key Exchange Algorithm Assume
they agree on p 29, a 7 Alice now selects a
random integer, Ia lt p and computes Ja aIa mod
p. Bob selects a random integer, Ib lt p and
computes Jb aIb mod p. Assume Alice chooses Ia
8 Ja 78 mod 29 5,764,801 mod 29
5,764,801/29 Q of 198,786 R of 7 So Ja
7 Assume Bob chooses Ib 6 Jb 76 mod 29
117,649 mod 29 117,649/29 Q of 4056 R of 25
So Jb 25 Alice Bob keep Ia and Ib secret,
but publicly exchange Ja Jb. Alice will
compute the secret key K (Jb)Ia mod p and Bob
will compute the secret key (Ja)Ib mod p.
8
Diffie/Hellman Key Exchange Algorithm Alices
secret key computation K (Jb)Ia mod p Ia 8,
Jb 25 258 mod 29 Oops 258 too big for my
calculator 258 mod 29 254 mod 29 x 254 mod 29
390,625 mod 29 x. 390,625/29 Q of 13,469 R of
24 x Q of 13,469 R of 24 Drop Qs. 24 x 24 mod
29 576 mod 29 576/29 and 576/29 Q of 19 R
of 25 Bobs secret key computation K (Ja)Ib
mod p Ib 6, Ja 7 76 mod 29 117,649 mod 29
117,649/29 Q of 4056, R of 25 So. Alice
computes the key 25 and so does Bob!
9
Diffie/Hellman Key Exchange Algorithm These
calculations produced the same key for Alice and
Bob. Why? Proof K (Jb)Ia mod p (aIb
mod p)Ia mod p (aIb)Ia mod p aIbIa mod
p which is the same as aIaIb mod p By simply
reversing the substitutions (starting at the
bottom) aIaIb mod p (aIa)Ib mod p
(aIa mod p)Ib mod p (Ja)Ia mod p So, (Ja)Ib
mod p (Jb)Ia mod p QED (i.e., which was to be
demonstrated)
10
Diffie/Hellman Key Exchange Algorithm The
secrecy of the key depends on the difficulty of
computing K from Ja aIa mod p for a Where
p, a, and Ja are known (we exchanged them) and a
specific Ia , not known. For example For p
97, a 5, Ia 36 Ib 58 Ja 536 mod 97 R
of 50 also written as 50 mod 97 Jb 558 mod 97
44 mod 97 The secret key is (Jb)Ia mod 97
4436 75 mod 97 i.e., K 75
11
Diffie/Hellman Key Exchange Algorithm So how
hard is it to find 75 given p 97, a 5, Jb
44 Ja 50 We must solve 44Ia k mod 97
50Ib mod 97 for k We know that Ia and Ib are
less than 97. We must compute 44x mod 97 and 50y
mod 97 until we get the same k for each 4496
5096 are the upper bounds so we need 2 x this
of calculations In reality, we know the key must
be between 1 and 96, so we could do a key space
search, return all keys and test. To make this
hard we only need to make the key space large.
12
Diffie/Hellman Key Exchange Algorithm
Communications Channel
Bob
Alice
p,a?
Alice proposes a prime, p, and a primitive root,
a
Bob accepts p and a
OK
Set p 5, a 3
Let p 5, a 3
Select Ia such that 0 lt Ia lt p
Select Ib such that 0 lt Ib lt p
Let Ia 2
Let Ib 4
Compute Ja
Compute Jb
Ja 32 mod 5 4
Jb 34 mod 5 1
Ja 4
Send Ja to Bob
Send Jb to Alice
Jb 1
Compute K
Compute K
K 12 mod 5 1
K 44 mod 5 1
13
Diffie/Hellman Key Exchange - Strength Using the
example numbers, the key appears easy to break.
However, recall we must find I in Ja aIa mod p
I is not disclosed in the exchange between
Alice Bob, a p are. p and a in real systems
are from 512 to 1024 bits long (64 - 128
char.). That is, we must factor p or a to find
trial keys, where p 1024 bits means p lt 21024
and a lt 21024 - 1 (a hard factoring
problem) exponentially difficult!
14
Diffie/Hellman Key Exchange - Weakness The key
exchange is computationally intense (resource use
issue). Some limitations It does not provide
authentication Subject to man-in-the-middle
attacks Assume Alice sends Bob Ja, but an
adversary intercepts Bobs Jb and substitutes
JI, the intruders value and sends to Alice. To
keep Bob from Responding the intruder will launch
a denial of service attack at Bob to crash Bobs
system. As a result, Alice would compute a key
that the intruder can also compute, establish
communications with the intruder and
potentially disclose sensitive information to the
adversary. We shall see how this is overcome in
a later chapter!