Cryptographic Protocols - PowerPoint PPT Presentation
1 / 3
Title:
Cryptographic Protocols
Description:
Informal analysis and design of CP is error prone. Properties are subtle ... Can read, alter, destroy any message. Can do everything, an honest principal can do ... – PowerPoint PPT presentation
Number of Views:45
Avg rating:3.0/5.0
Title: Cryptographic Protocols
1
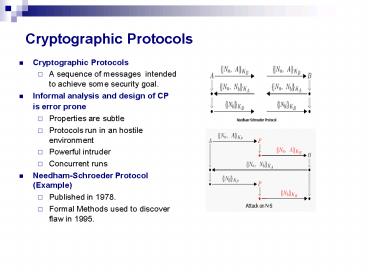
Cryptographic Protocols
- Cryptographic Protocols
- A sequence of messages intended to achieve some
security goal. - Informal analysis and design of CP is error prone
- Properties are subtle
- Protocols run in an hostile environment
- Powerful intruder
- Concurrent runs
- Needham-Schroeder Protocol (Example)
- Published in 1978.
- Formal Methods used to discover flaw in 1995.
2
Formal Analysis of Cryptographic Protocols
- Dolev-Yao Intruder
- Complete control over channel
- Can read, alter, destroy any message
- Can do everything, an honest principal can do
- Dolev-Yao Problem
- Given a cryptographic protocol,
- Specify its goals
- Prove correctness or provide counter-examples
highlighting its failure - Assuming underlying cryptosystem is perfect.
- Existing Formal Mechanisms
- Proof Generation Mechanisms
- Use Theorem Proving Techniques
- Attack Construction Mechanisms
- Use Model Checking
3
CryPA Our Tool
- Cryptographic Protocol Analyzer
- Based on Strand Spaces Formalism
- GUI Specification of cryptographic protocols
- Generation of PVS Theories, which axiomatize -
- Cryptographic Operations
- Intruder Capabilities
- Message Exchange
- Protocol Goals and Assumptions
- Proofs of Protocol Properties
- Construction of Attacks on Protocols
GUI
CAPSL
CryPA
PVS Connector
Attack Constructor