Symmetric Encryption - PowerPoint PPT Presentation
1 / 7
Title:
Symmetric Encryption
Description:
Horst Feistel (IBM) invented the basic. algorithm in 1973. Feistel ciphers use. symmetric block ... Data Encryption Standard - an algorithm selected by the ... – PowerPoint PPT presentation
Number of Views:61
Avg rating:3.0/5.0
Title: Symmetric Encryption
1
Symmetric Encryption
2
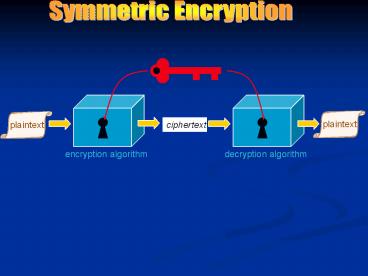
Feistel Ciphers
Key
Horst Feistel (IBM) invented the basic
algorithm in 1973.
Feistel ciphers use symmetric block
encryption relying upon product
transformations.
Encryption decryption use the same
algorithm.
3
DES
DES Data Encryption Standard - an algorithm
selected by the National Institute of Standards
Technology for the encryption of non-classified
data.
The current DES algorithm was adopted by the U.S.
Nat. Bureau of Standards in 1977.
Block size ____ bits Key size ____ bits 8-bit
parity 16-round Feistel encryption (preceded by
one permutation and followed by the permutations
inverse)
Subkeys The key (56-bits) is split in two and
each half is rotated left by 1 or 2 bits. The
resulting two 28-bit values index into a table
to produce a 48-bit subkey. The rotated values
are also forwarded to compute the next subkey.
f function 1) input to f is expanded from 32 to
48 bits via table lookup 2) 48-bit value from
(1) is XORed with subkey 3) 48-bit value from
(2) is partitioned into eight 6-bit values 4)
6-bit values from (3) are separated into outside
2 bits and center 4 bits (outside bits
select row and inside bits select column from
S-box table) 5) eight S-box lookup values (each
4 bits long) are concatenated
4
S-Boxes
The DES cipher substitutes via eight different
S-boxes two are below.
5
DES Crytanalysis
Brute Force
1977 - brute force attacks might be possible in
the future Diffie Hellman IEEE Computer, June
1997 - a distributed collection of 3500
research computers discover DES key in ___ months
1998 - Electronic Frontier Foundation builds
___________________________________.
1999 - Net uses DES Cracker plus 100,000 PCs to
crack DES in under ______________.
REF www.tropsoft.com/strongenc/des.htm
6
Other Symmetric Ciphers
______ - 1979
also called triple DES use two keys and
three DES encryptions cipher Ekey1( Dkey2(
Ekey1( plaintext ) ) ) 3DES has an effective
key size of 112 bits.
______ - 1991
International Data Encryption Algorithm
developers from Swiss Federal Institute of
Technology 128-bit key, but differs from DES in
round function and subkey generation.
___________ - 1993
developed by Bruce Schneier compact,
efficient, algorithm w/ key of 128 bits
______ - 1994
developed by Ron Rivest efficient algorithm
with variable length keys
______ - 1999
Advanced Encryption Standard selected
algorithm Rijndael a product cipher using key
sizes of 128, 192 and 256 bits (128-bit block
size).
7
Symmetric Pro Con
Advantages
only one key to generate relatively
well-tested and established algorithms cipher
algorithms are efficient
Disadvantages
potentially large number of keys
number of private keys
______________________________ (How can this be
accomplished securely?)