B2B and clientside PKI
1 / 1
Title:
B2B and clientside PKI
Description:
The purchasing system receives and validates incoming order-requests by employees. ... changed in one huge step, and for all involved parties (the 'flag day' approach) ... –
Number of Views:32
Avg rating:3.0/5.0
Title: B2B and clientside PKI
1
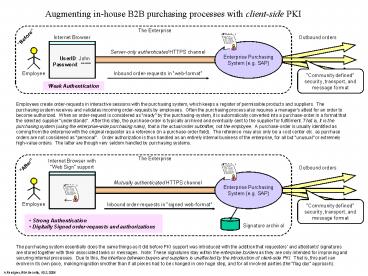
Augmenting in-house B2B purchasing processes with
client-side PKI
The Enterprise
Outbound orders
Before
Enterprise PurchasingSystem (e.g. SAP)
Server-only authenticated HTTPS channel
Inbound order-requests in web-format
Community defined security, transport, and
message format
Weak Authentication
Employees create order-requests in interactive
sessions with the purchasing system, which keeps
a register of permissible products and suppliers.
The purchasing system receives and validates
incoming order-requests by employees. Often the
purchasing process also requires a managers
attest for an order to become authorized. When
an order-request is considered as ready by the
purchasing-system, it is automatically converted
into a purchase-order in a format that the
selected supplier understands. After this
step, the purchase-order is typically archived
and eventually sent to the supplier for
fulfillment. That is, it is the purchasing system
(using the enterprise-wide purchasing rules),
that is the actual order submitter, not the
employee. A purchase-order is usually identified
as coming from the enterprise with the original
requester as a reference (in a purchase-order
field). The reference may also only be a cost
center etc. as purchase orders are not considered
as personal. Order authorization is thus
handled as an entirely internal business of the
enterprise, for all but unusual or extremely
high-value orders. The latter are though very
seldom handled by purchasing systems.
The Enterprise
Internet Browser with Web Sign support
After
Outbound orders
Enterprise PurchasingSystem (e.g. SAP)
Mutually authenticated HTTPS channel
Inbound order-requests in signed web-format
Community defined security, transport, and
message format
Strong Authentication Digitally Signed
order-requests and authorizations
Signature archival
The purchasing system essentially does the same
things as it did before PKI support was
introduced with the addition that requesters and
attestants signatures are stored together with
their associated tasks or messages. Note These
signatures stay within the enterprise borders as
they are only intended for improving and securing
internal processes. Due to this, the interface
between buyers and suppliers is unaffected by the
introduction of client-side PKI. That is, this
part can evolve in its own pace, making migration
smother than if all pieces had to be changed in
one huge step, and for all involved parties (the
flag day approach).
A.Rundgren,RSA Security, V0.2, 2006