Emerging Technology: RFID - PowerPoint PPT Presentation
Title:
Emerging Technology: RFID
Description:
Multiple items can be read at the same time. Ability to change or add data after creation ... of total sales are lost each year due to supply chain information ... – PowerPoint PPT presentation
Number of Views:237
Avg rating:3.0/5.0
Title: Emerging Technology: RFID
1
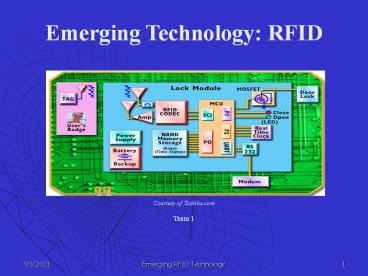
Emerging Technology RFID
Courtesy of
Toshiba.com Team 1
2
Overview
- Introduction
- RFID Technology
- Competitor Technology
- Industry Segmentation
- Inventory Management
- Supply Chain Management
- Return on Investment
- Public Policy
- Case Study Wal-Mart
- Conclusion
3
Introduction to RFID Technology
- RFID Radio Frequency Identification
- RFID System uses the electromagnetic in the radio
frequency of the electromagnetic spectrum to
uniquely identify any object or person - Consists of three components
- A Tag
- Active Tag
- Passive Tag
- A Reader
- An Antenna
4
RFID TechnologyTypical RFID System
Courtesy of rfid.com
5
How RFID Works
- Tags starts emitting a signal
- Reader notices the signal
- Once the tag has decoded the signal as valid, it
then replies to the reader, indicating its
presence by affecting the reader field - Collision might happen if many tags are present
and they all reply at the same time - The reader manages this by using Anti-Collision
Algorithm so that tags will be individually
selected and sorted - Once a tag is selected, the reader is able to do
a number of operations such as read the tags ID
number, or write information to it
6
RFID Tags
- Tags are attached into/onto objects
- Each tag has an internal memory in which it
stores information about its - Objects
- Serial number (unique number)
- Product composition and Manufacture date
- When a tags passes through a field, which is
generated by a reader, it transmits the
information back to the reader to identify the
object
7
Active Tags
- Active tags
- Powered by internal battery
- Memory size varies and it depends to its
application requirement - They are larger than passive tags
- Have longer read range
- Have limited operational life
8
Passive Tags
- Passive tags
- They dont require batteries
- Powered by the reader
- They are lighter and less expensive than active
tags - They have shorter read range
- Have longer operational life
9
RFID Reader (1)
- Provides the means of communicating with tags and
facilitating data transfer - Functions of a reader might include
- Signal Conditioning
- Error Checking
- Error Correction
10
RFID Reader (2)
- Once the signal from a tag is received and
decoded - Algorithms is applied to decide whether the
signal is a repeat transmission - This algorithm is known as Command Response
Protocol and is used to avoid the problem of
reading multiple tags in a short time
11
RFID Reader (3)
- Operating frequencies of a reader
- HF and UHF
- Multi-frequency readers
- Hand-held readers are used to manually check or
update tags offline - The communication process between the tag and the
reader is controlled and managed by one of
several protocols, such as the ISO 15693 and ISO
18000-3 for HF or the ISO 18000-6 and EPC for
UHF. LaranRFID
12
RFID Standards (1)
13
RFID Standards (2)
- Tags are categorize by their ability to read and
write data - EPC (Electronic Product Code) is used to classify
and categorize tags - It is very similar to UPC (Universal Product
Code) used in Barcodes - Ranges from 64 bits to 256 bits
- It has four distinct fields
14
RFID Standards (3)
- Header is 8 bits, indicates the tags
classification whether it is class 0, class 1,
class 2 etc - EPC Manager contains the manufacturer information
- Object class refers to the exact type of the
product like SKU - Serial Number provides the tags unique number
15
RFID Antenna
- RFID antenna emits radio signals to activate the
tag and write and read data to it - It acts as a conduit between the tag and the
reader, which controls the systems data
acquisition and communication - Antennas are available in a variety of sizes and
shapes
16
RFID Antenna (2)
- An antenna produces electromagnetic field which
are constantly present when multiple tags are
expected continually - If constant interrogation is not required, a
sensor device can activate the field
17
Technical Safeguards/Security
- Integrity
- Availability
- Authentication
- Confidentiality
18
Competitor Technologies
- Barcodes
- IButton
- Smart Dust
19
Barcode
- Improve Operational Efficiency
- Save Time
- Reduces Errors
- Barcodes requires direct line of sight between
the readers and the barcode tags - Reader has to scan each item individually
20
RFID vs Barcode
- RFID have many advantages over Barcode
- Multiple items can be read at the same time
- Ability to change or add data after creation
- Tags can withstand hostile environments
- Data can exist in the tag and this eliminates the
need to access a database - Tags are much smaller than barcodes
- They can be reused
- Data can be read and embedded without visible
exposure
21
IButton
- Computer chip enclosed in a 16mm stainless steel
can. - Can withstand tough and rigged environment
- It can hold larger memory than RFID
22
IButton
- IButton is not wireless. It requires the reader
to physically contact the "button" in order to
read or write - Each IButton Costs between 2 and 53 depending
on the implementation
23
Smart Dust
- Example Solar powered mote with bi- directional
communications and sensing - 11.7 mm3 total circumscribed volume
24
Smart Dust
- Small micro-machines fitted with wireless
communication devices. When clustered together,
they automatically create highly flexible,
low-power networks. - Power
- Vibrations in the wall
- Solar light
- Changes in barometric pressure
25
Industry Segmentation of RFID
- Medical and Pharmaceutical
- Fuel and Oil
- Airlines
- Merchandise
- Banking
- Automobile
- Access Control
- Other
26
Inventory Management
- Functions related to the tracking and management
of material. This would include the monitoring
of material moved into and out of stockroom
locations and the reconciling of the inventory
balances. - What is Successful Inventory Management?
- Maintaining a wide assortment of stock
- Increasing inventory turnover
- Keeping stock low
- Obtaining lower prices by making volume purchases
- Having adequate inventory on hand
27
Inventory Management Cycle
28
Supply Chain Management
- The process of how products are designed,
sourced through an often complex network,
manufactured, and distributed from raw material
to the end customer - Many companies do not use automated procedures
instead, they use e-mail, fax or phone to
communicate with suppliers. - Old systems usually dealt with information that
was not current.
29
Supply Chain Management Cycle
30
The Need for Change
- 40 billion (about 3.5) of total sales are lost
each year due to supply chain information
inefficiencies - In 2002 out-of-stock products cost supermarket 6
billion in lost sales - Lack of cooperation within the supply chain
activities - Lack of information sharing within the supply
chain activities - Lack of integration in behavior and functions
- Lack of accurate forecasting
- Must automate process to avoid the above
situations!
31
Return on Investment (ROI)
- The driving factor for change in the market is
profit. - The profit or loss resulting from an investment
transaction, usually expressed as an annual
percentage return. - ROI will not happen right away.
- ROI will benefit larger firms due to the cost of
chips. - Chips currently range from 1835 cents, making
more affordable by larger firms. - Currently chips are expensive for smaller firms.
Perhaps once the chips go down to 8 cents smaller
companies will be able to benefit from RFID and
have high rate of ROI. - Smaller companies want to wait until prices drop
to avoid negative ROI.
32
Value proposition for using RFID
- For suppliers, RFID will achieve the following
(Zebra Technologies) - Lower inventory levels by 5-30
- Lower transportation cost by 2-13
- Higher sales by 1-5
- Reduction in lead times by 10-50
- For the retailer, RFID will achieve the
following (Zebra Technologies) - Better availability on shelf by 5-8
- Lower inventory levels by 5-10
- Higher sales by 2-10
- Lower logistics cost 3-4
33
Public Policy
- Why public policy needed?
Proponents
Opponents
Conflicts
34
Proponents
- Benefits
- Reduce Cost
- Improve Supply-chain management
- Improve Inventory Management
- Wal-Mart
- Top 100 Suppliers
- Save 16.7 Billion/Year
- Deadline January 2005
- DoD
- 20,000 Suppliers
- Close to 24 Million/Year (Food, Paper, Cleaning
Products) - Deadline January 2005
35
Opponents
- Privacy Advocates
- American Civil Liberties Union (ACLU)
- Consumer Action
- Consumers Against Supermarket Privacy Invasion
and Numbering (CASPIAN) - Electronic Frontier Foundation (EFF)
- Electronic Privacy Information Center
- Junkbusters
- Privacy Rights Clearinghouse
36
Opponents Arguments
- Threats
- Hidden placement of tags
- Hidden readers
- Data aggregation
- Individual tracking
- Misuse/Abuse of RFID
- Monitoring Consumers
- Embedded into Human-Beings
- Tracking Cash
- How do you resolve such conflict?
37
Proposed Policy
- Individuals must have a right to know that
products contain RFID tags. - Individuals also must know when, where and why
RFID tags are being read. - Individuals have the right to have RFID tags
removed or permanently deactivated when they
purchase products or otherwise obtain items
containing RFID tags. - Merchants must be prohibited from coercing
customers into keeping the tags live on the
product. - The default option, at checkout, must be to
disable it.
38
Median Path
- Median Path
- Compromise between the Proponents and
Opponents - Technical Safeguards
- Implementation of strong policies and procedures
- Benefit the proponents and Protect the opponents
39
Case Study Wal-Mart
- Wal-Marts initiatives
- Business Process Analysis
- Value proposition to use RFID
- Outstanding issues
40
Wal-Marts Initiatives
- Stated publicly in June 2003
- Carton, case pallet tagging
- Top 100 suppliers
- UHF EPC RFID to be used
- Be compliant by 1/1/2005
- Meetings in Bentonville 11/4/03
- 130 top suppliers
- More than 40 solution providers
- All learnt what Wal-Mart expected
- Source Zebra Technologies
41
Wal-Marts Initiatives
- Requirements
- Accepting UHF Class 0 or Class 1
- 96 bit EPC current GTIN as the base
- Keep barcode technology
- Performance
- 100 pallet read at receiving
- Conveyor100carton tag (540fpm)
- All product types
- Source Zebra Technologies
42
Wal-Marts Initiatives
- Scope of Operation
- More than 100 distribution centers
- More than 3000 stores
- Over 3 billion cases and cartons per year
- Nearly 100 million pallets per year
- All suppliers compliant by end of year 2006
- First Phase of Deployment(1/1/05)
- 3 regional distribution centers
- 150 stores
- All products from top 100 suppliers
- Source Zebra technologies
43
Business Process Analysis
- Current business process
- Identify
- needs
- Identify
- sources
- Select
- supplier
- Place
- orders
Buying process
Buy Inventory
Receive Resource
- Move to Staging
- area
Enter Pallets in WMS
Affix Barcode to Pallet
Move Pallets to Storage
Stages in Inventory Management System
44
Business Process Analysis
- Business process with the use of RFID
Buy Inventory
Receive Resources
- Read EPC in
- RFID system
Send data in WMS
Move pallets to storage
Stages in Inventory Management System using RFID
tags.
- Legend
- WMS Warehouse Management System
- EPC Electronic product Code.
45
Value Proposition to use RFID
- Estimate of Wal-Marts savings
- 6.7 billion Eliminating Scanning
- 600 million Reduce out-of-stock
- 575 million Reduce shrinkage
- 300 million Better tracking
- 180 million Reduce inventory cost
- 8.35 billion Pre-tax saving
- SourceEweek
46
Outstanding Issues
- Supplier may not be able to meet the 1/1/05
deadline - Invasion of Privacy for consumers
- RFID tags expensive for small suppliers
- Compatibility issues
47
Conclusion
- Revolutionary Technology
- Benefits
- Supply-Chain Management
- Inventory Management
- Issues
- Privacy
- Cost
- Median Path
- Benefit the Proponents Protect the Opponents