Certification Authority Structure - PowerPoint PPT Presentation
1 / 15
Title:
Certification Authority Structure
Description:
... access to the public key of the CA can recover the public key which was ... No party other than the CA can modify the certificate without being detected ... – PowerPoint PPT presentation
Number of Views:258
Avg rating:3.0/5.0
Title: Certification Authority Structure
1
Certification Authority Structure
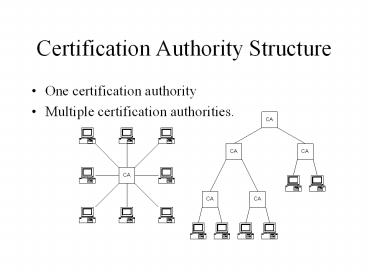
- One certification authority
- Multiple certification authorities.
2
CA Structure (so far)
- CAs are competitors. Every CA want to be root CA.
- So, not centralized, not hierarchy just a big
mess. - Web browsers have to have almost all of
certification authorities public key.
3
Certificate Format
4
Certificate Format
- Certificate ((Version, SerialNumber, SigAlgID,
UserDN, (Time, Time), UserDN, Key), CertSig) - To obtain public key from a certificate use
- Key snd (snd (snd (snd (snd (snd (fst
Certificate)))))) - Let define
- ObtainPublicKey Certificate
- snd (snd (snd (snd (snd (snd (fst
Certificate)))))) - To obtain public key from a certificate use
- Key ObtainPublicKey Certificate
- Where
- fst (a, b) a
- snd (a, b) b
5
Certificate Format
- Define
- ObtainVersion cert fst (fst cert)
- ObtainSerialNumber cert fst (snd (fst cert))
- ObtainSigAlgID cert fst (snd (snd (fst cert)))
- ObtainIssuer cert fst (snd (snd (snd (fst
cert)))) - ObtainValidPeriod cert fst (snd (snd (snd (snd
(fst cert))))) - ObtainStartTime cert fst (ObtainValidPeriod
cert) - ObtainEndTime cert snd (ObtainValidPeriod cert)
- ObtainSubject cert fst (snd (snd (snd (snd (snd
(fst cert)))))) - ObtainPublicKey cert snd (snd (snd (snd (snd
(snd (fst cert)))))) - ObtainContent cert fst cert
- ObtainSignature cert snd cert
6
Proof of Obtain Definitions
- ? a, b, c, d, e, f, g, h, i, cert.
- (cert ((a,b,c,d,(e,f),g,h),i)) ?
- (ObtainVersion cert a) ?
- (ObtainSerialNumber cert b) ?
- (ObtainSigAlgID cert c) ?
- (ObtainIssuer cert d) ?
- (ObtainValidPeriod cert (e,f)) ?
- (ObtainStartTime cert e) ?
- (ObtainEndTime cert f) ?
- (ObtainSubject cert g) ?
- (ObtainPublicKey cert h) ?
- (ObtainContent cert (a,b,c,d,(e,f),g,h)) ?
- (ObtainSignature cert i)
7
Digital Signature
- Digital Signature Generation
- Digital Signature Verification
8
Certificate Properties
- There are two certificates properties specified
in X.509 standard. - Any user with access to the public key of the CA
can recover the public key which was certified. - No party other than the CA can modify the
certificate without being detected (certificates
are unforgeable). - We need the definition of how to verify the
integrity of certificate.
9
isCertIntact
- To verify that certificate arrives intact, we
need to verify the digital signature - Define
- ? decriptP dkey hash cert.
- isCertIntact decryptP dkey hash cert
- decryptP (ObtainSigAlgID cert) dkey
(ObtainSignature cert) - hash (ObtainContent cert)
10
Certificate Properties
- Any user with access to the public key of the CA
can recover the public key which was certified. - ? CAs CAp dkey certVersion serialNumber certAlgID
certIssuer - startTime endTime subject certSig certContent
cert hash decryptP - encryptP.
- (certContent (certVersion, serialNumber,
certAlgID, certIssuer, - (startTime,endTime), subject,
key)) ? - (certSig encryptP certAlgID CAs (hash
certContent)) ? - (cert (certContent,certSig)) ?
- (!msg. decryptP certAlgID CAp (encryptP
certAlgID CAs msg) msg) - ?
- (!msg dkey2. (decryptP certAlgID dkey2
- (encryptP certAlgID CAs msg)
msg) ? (dkey2 CAp)) - ?
- (isCertIntact decryptP dkey hash cert ? (dkey
CAp)) - The result of verifying Certificate using
isIntact will be true if and only if the key that
user use to verify is the public key of
Certification Authority who issue this
Certificate.
11
Certificates Properties
- No party other than the CA can modify the
certificate without being detected (certificates
are unforgeable). - ? CAp CAs ekey certVersion serialNumber certAlgID
certIssuer - startTime endTime subject certSig certContent
cert hash decryptP - encryptP.
- (certContent (certVersion, serialNumber,
certAlgID, certIssuer, - (startTime,endTime), subject,
key)) ? - (certSig encryptP certAlgID ekey (hash
certContent)) ? - (cert (certContent,certSig)) ?
- (!msg. decryptP certAlgID CAp (encryptP
certAlgID CAs msg) msg) - ?
- (!msg ekey2. (decryptP certAlgID Cap
- (encryptP certAlgID ekey2 msg)
msg) ? - (ekey2 CAs)) ?
- (isCertIntact decryptP CAp hash cert ? (ekey
CAs)) - The result of verifying Certificate using
Certification Authoritys public key will be true
if and only if the key that used to sign this
Certificate is the Certification Authoritys
private key.
12
isCertValid
- Verify that the current timestamp fall in the
validity period of the certificate. - Define
- isCertValid currentT cert
- currentT gt ObtainStartTime cert ? currentT lt
ObtainEndTime cert
13
Certificates Specification
- Certificate is certified if and only if
- Certificate is intact.
- Certificate is not expire.
- Certificate has not been revoked.
- ? dkey currentT revTs cert crl decryptP1
decryptP2 hash1 hash2. - isCertify dkey currentT revTs cert crl
decryptP1 decryptP2 hash1 - hash2
- isCertIntact decryptP1 dkey hash1 cert ?
- isCertValid currentT cert ?
- (ObtainIssuer cert ObtainCRLIssuer crl) ?
- isCRLIntact decryptP2 dkey hash2 crl ?
- (isRevoke currentT revTs cert crl)
14
Certificates Specification
- ? CAs CAp key ekey certVersion serialNumber
certAlgID certIssuer startTime endTime subject - certSig certContent cert currentT revTs
crlVersion crlAlgID crlIssuer thisUpdate
nextUpdate - revCert crlSig crlContent crl decryptP1
decryptP2 hash1 hash2. - (!msg. decryptP1 certAlgID CAp (encryptP1
certAlgID CAs msg) msg) gt - (!msg. decryptP2 crlAlgID CAp (encryptP2
crlAlgID CAs msg) msg) gt - (!m ekey2. (decryptP1 certAlgID CAp
(encryptP1 certAlgID ekey2 m) m) gt (ekey2
CAs)) gt - (!m ekey2. (decryptP2 crlAlgID CAp
(encryptP2 crlAlgID ekey2 m) m) gt (ekey2
CAs)) gt - (certContent (certVersion, serialNumber,
certAlgID, certIssuer, (startTime,endTime), - subject, key))
gt - (certSig encryptP1 certAlgID ekey (hash1
certContent)) gt - (cert (certContent,certSig)) gt
- (crlContent (crlVersion,crlAlgID,crlIssue
r,thisUpdate,nextUpdate,revCert)) gt - (crlSig encryptP2 crlAlgID ekey (hash2
crlContent)) gt - (crl (crlContent,crlSig)) gt
- ((ekey CAs) /\
- (certIssuer crlIssuer) /\
- currentT gt startTime /\
- currentT lt endTime /\
- (IS_EL (serialNumber,revTs) revCert /\
currentT lt revTs)
15
Further use of Certificates Specification
- User certificates specification to formalize the
specifications of authentication protocol that
use Certificates as a component for obtaining
trusted public key of principals. - ?? CAp currentT recvrUserDN authenticator1
decryptP hash - isChainCertify ObtainKey isNew1.
- isAuthenticate1 CAp currentT recvrUserDN
authenticator1 decryptP - hash isChainCertify ObtainKey isNew1
- isIntact1 CAp authenticator1 decryptP hash
isChainCertify - ObtainKey ?
- isNew1 (ObtainA1RndNumber authenticator1)
- (ObtainA1Timestamp authenticator1) ?
- isIntendedRcpt1 recvrUserDN authenticator1