Rc4 PowerPoint PPT Presentations
All Time
Recommended
Title: Intro Author: Mark Stamp Last modified by: Mark Stamp Created Date: 6/9/2003 3:34:05 PM Document presentation format: On-screen Show Other titles
| PowerPoint PPT presentation | free to download
Diffie: RC4 is 'too good to be true' Used lots of places: SSL, ... WEP: 'Swiss cheese' of ... Trudy watches IVs until she sees 3-byte IV of the form: ...
| PowerPoint PPT presentation | free to download
Title: RC4 dan A5 Author: Customer Last modified by: Customer Created Date: 9/30/2006 4:26:31 AM Document presentation format: On-screen Show Company
| PowerPoint PPT presentation | free to view
RC4 ...break up. Initialize an array of 256 bytes. Run the KSA on them ... XOR keystream with the data to generated encrypted stream. Transmit Encrypted stream. ...
| PowerPoint PPT presentation | free to view
Rent Aqua Data Flostick RC4 at Hoskin Scientific. We offer Canada rentals for current meters, profilers, echo sounders and lease of other environmental tools.
| PowerPoint PPT presentation | free to download
Blowfish, RC5 Block Ciphers M. Sakalli, Marmara Univ. Chapter 6 of Cryptography and Network Security by William Stallings Modified from the original s of Lawrie ...
| PowerPoint PPT presentation | free to view
Blowfish, RC5 Block Ciphers M. Sakalli, Marmara Univ. Chapter 6 of Cryptography and Network Security by William Stallings Modified from the original s of Lawrie ...
| PowerPoint PPT presentation | free to download
RC4 generates a pseudorandom stream of bits (keystream) ... Generates a sequence of pseudorandom numbers and combines it with the data using ...
| PowerPoint PPT presentation | free to view
Non-fortuitous Predictive States of the RC4 Keystream Generator ... Definition of a Non-fortuitous Predictive State. Main Contributions ...
| PowerPoint PPT presentation | free to view
RC4 Cryptanalysis. XOR is a weak operation ... RC4 Cryptanalysis ... Automated cryptanalysis of XOR plaintext strings. Cryptologia, (2):165-181, April 1996. ...
| PowerPoint PPT presentation | free to view
based on an exchange shuffle paradigm. the algorithm Runs in Two Phases. key-scheduling algorithm ... exchange shuffle model. RC4A: Description ...
| PowerPoint PPT presentation | free to view
Broadcast encryption. analysis. optimization. Other work. RC4 stream cipher ... Broadcast encryption. source. receivers. k1, k2, k3, k4, k5,..., kn. k1. k2. k3 ...
| PowerPoint PPT presentation | free to download
RC4 with 40-bit keys. RC4 with 128-bit keys. CBC Block Ciphers. RC2 with 40 bit key ... Verisign. InterSSL. WorldTrust. NOTE: Anyone can act as a CA ...
| PowerPoint PPT presentation | free to view
Broadband VPNs - Outsourcing ISP Services to Cable TV and ... Indian Outhouse PPTP Point-to-Point Tunneling Protocol Developed by Microsoft Uses 40 or 128-bit RC4 ...
| PowerPoint PPT presentation | free to view
Data Integrity (checksum, anti-tampering) WEP. RC4 stream cipher ... Message Integrity Code (MIC) - 64-bit message calculated using 'Michael' ...
| PowerPoint PPT presentation | free to download
Wireless LAN Security Security Basics Three basic tools Hash function. SHA-1, SHA-2, MD5 Block Cipher. AES, RC4, Public key / Private key. RSA. Cryptographic ...
| PowerPoint PPT presentation | free to download
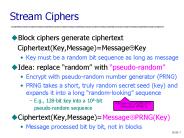
Encrypt with pseudo-random number generator (PRNG) ... To use RC4, usually prepend initialization vector (IV) to the key. IV can be random or a counter ...
| PowerPoint PPT presentation | free to download
None. RC4 encryption algorithm. Chapter 7. Access Rights Access Settings ... Chapter 7 Filterable Event Log. Logging Screen. Filter events by: Class. Severity ...
| PowerPoint PPT presentation | free to view
Implementation of multiple security zones for wireless Viaduct. Huaiyu Liu ... WaveLAN 802.11 IEEE PC Card (Orinoco) Security support -- RC4 encryption ...
| PowerPoint PPT presentation | free to view
Native support in most modern Operating Systems ... 3DES, AES (Rijndael), Blowfish, RC4, CAST5, IDEA. One key used to encrypt & decrypt. ...
| PowerPoint PPT presentation | free to download
Examples are DES, RC4, Blowfish, IDEA. Public Key Algorithms. Two, ... And there is a bevy of unpatented ones, RC4 ,SAFER, and Blowfish. Triple-DES Algorithm ...
| PowerPoint PPT presentation | free to view
Very popular open-source package, written by Darren Reed. Runs on many UNIX/Linux versions, ... Confidentiality: AES, DES, 3DES, blowfish, cast128, RC4 ...
| PowerPoint PPT presentation | free to download
Data stream encryption , WEP 40,128,256 bit RC4 encryption mechanism ... Channel number, SSID, WEP. ACL MAC access control list. Client access status ...
| PowerPoint PPT presentation | free to view
(kbytes/sec.) PRB optimized (kbytes/s) TEA. 128. 700. DES. 56. 350. 7746. Triple-DES. 112. 120 ... Confidentiality: using one of DES, Triple DES, IDEA, RC2, RC4, ...
| PowerPoint PPT presentation | free to view
Message packet uses the RC4 encryption algorithm, a stream cipher. ... Encryption Algorithm of WEP. 4. Some ... Uses the Advanced Encryption Standard (AES) ...
| PowerPoint PPT presentation | free to view
Ben Rothke, CISSP CISM. Security Consultant BT INS ... DES, Triple-DES, AES, IDEA, Blowfish, CAST, MARS, Twofish, Rijndael, RC2, RC4, ...
| PowerPoint PPT presentation | free to view
WEP misuses the RC4 encryption algorithm in a way that exposes the protocol ... fresh encryption and integrity keys, undoing the threat of attacks stemming from ...
| PowerPoint PPT presentation | free to download
A cipher suite based on old hardware (RC4 cipher) ... Note: priority is set to be all 0 and is reserved for the future. Michael ...
| PowerPoint PPT presentation | free to download
History The Mechanical Era. Invention of cipher machines. Examples ... Blowfish. 17. Symmetric Algorithms. RC4. RC5. CAST. SAFER. Twofish. 18. Asymmetric Algorithms ...
| PowerPoint PPT presentation | free to view
The examination of security systems which are implemented primarily by means of an electronic ... (credit for this image: Vitaly Shmatikov) RC4 keystream = IV ...
| PowerPoint PPT presentation | free to view
Blowfish, RC5, RC4, etc. 8/25/09. Tutorial on Network Security: Sep 2003 ... Blowfish. Developed in 1993. block cipher. up to 448 bit keys. no known attacks ...
| PowerPoint PPT presentation | free to download
802.1 Higher Layer LAN Protocols Working Group. 802.3 Ethernet Working Group ... to Scott Fluhrer, Itsik Mantin, and Adi Shamir (FSM) RC4 key scheduler attack ...
| PowerPoint PPT presentation | free to view
What is WEP (Wired Equivalent Privacy)? WEP uses a RC4 cipher (stream cipher) which attempts to keep the ... AP will reassemble it and relay as large frame ...
| PowerPoint PPT presentation | free to download
In other words, flipping bit n in the message results in a deterministic set of ... Because flipping bits carries through after an RC4 decryption, this allows the ...
| PowerPoint PPT presentation | free to view
Shared Key Easily Cracked. RC4 has a large amount of weak keys ... Fundamentally much harder to crack. Weakness still lies in the key ...
| PowerPoint PPT presentation | free to download
128-bit challenge text based on RC4 stream cipher ... Host/AP share 40-bit symmetric key. Semi-permanent WEP key. May be longer (e.g., 128 bits) ...
| PowerPoint PPT presentation | free to view
An algorithm (or cipher) and a key are required in order to ... Blowfish: a faster and more secure replacement of DES. RC4 (Rivest's Code 4): a stream cipher ...
| PowerPoint PPT presentation | free to download
Measuring of the time consumption of the WLAN's security ... CRC-32 checksum. Average latency = 142 ms. Time = 12,8 ms. Results. WEP 128-bit. Stream cipher RC4 ...
| PowerPoint PPT presentation | free to view
Key must be a random bit sequence as long as message. Idea: replace 'random' with 'pseudo-random' ... To use RC4, usually prepend initialization vector (IV) to the key ...
| PowerPoint PPT presentation | free to download
IEEE 802.11 Security and 802.1X Dan Simon, Bernard Aboba, Tim Moore Microsoft Corporation IEEE 802.11 Attempts to provide privacy of a wire RC4 stream cipher ...
| PowerPoint PPT presentation | free to download
Preamble to Lectures 3 and 4. What is missing so far in terms of making ... others including IDEA, Blowfish, RC4, SEAL, ... PGP - Pretty Good Privacy ...
| PowerPoint PPT presentation | free to view
The pseudorandom random number generator (PRNG), i.e. RC4, is a set of rules ... Pick Random SNonce, Derive PTK = EAPoL-PRF(PMK,ANonce I SNonce I AP MAC Addr I ...
| PowerPoint PPT presentation | free to view
'the enemy knows the system' by Claude Shannon ... DES, AES, Blowfish, etc. Stream. A5/1, A5/2, RC4, etc. Asymmectric. Public key Cipher ...
| PowerPoint PPT presentation | free to view
Stream Cipher Random numbers play an important role in the use of encryption for various network security applications. In this section, we provide a brief overview ...
| PowerPoint PPT presentation | free to view
... and Computer Privacy,' Scientific American, v. 228, n. 5, May 73, pp. 15-23. ... stops casual disclosure. doesn't give people a false sense of security ...
| PowerPoint PPT presentation | free to download
Resolved packets can leak information about the subsequent byte of the current ... each key byte before any packet gives us information about a later key byte. ...
| PowerPoint PPT presentation | free to view
Title: Security Issues in 802.11b WLANs Author: Mahendran Velauthapillai Last modified by: Mahendran Velauthapillai Created Date: 4/28/2003 2:14:22 AM
| PowerPoint PPT presentation | free to download
Stream Ciphers CS 470 Introduction to Applied Cryptography Instructor: Ali Aydin Selcuk CS470, A.Selcuk Stream Ciphers * CS470, A.Selcuk Stream Ciphers * Stream ...
| PowerPoint PPT presentation | free to download
Title: 1 . Author: SEJONG Last modified by: SEC Created Date: 8/27/2003 3:33:37 AM Document presentation format: (4:3)
| PowerPoint PPT presentation | free to view
Keystream leaks, under known-plaintext attack ... the xor of plaintexts leaks (P P' = C C'), which ... Or, if we can guess one plaintext, the other is leaked ...
| PowerPoint PPT presentation | free to view
Internet. The Problem: Security! Wireless networking is just radio communications ... Overview of the Talk. In this talk: Security evaluation of WEP. The ...
| PowerPoint PPT presentation | free to download
802.11b Security CSEP 590 TU Osama Mazahir Introduction Packets are sent out into the air for anyone to receive Eavesdropping is a much larger concern in wireless ...
| PowerPoint PPT presentation | free to download
Cryptography and Network Security Chapter 7 Fifth Edition by William Stallings Lecture s by Lawrie Brown * A typical stream cipher encrypts plaintext one byte at ...
| PowerPoint PPT presentation | free to download
SSID was intended to be used much like a strong password (long, non-meaningful strings, symbols) ... This defeats the WEP authentication protocol ...
| PowerPoint PPT presentation | free to download