Prng PowerPoint PPT Presentations
All Time
Recommended
RBG: a device or algorithm which outputs a sequence of ... generating random bit sequence of length lg n 1, ... Test: comparing with expected ...
| PowerPoint PPT presentation | free to view
PRNGs, Linear Congruential Generators to Combined Hybrid Generators ... A finite period is required by the finite number ... P. Patten personal communication. ...
| PowerPoint PPT presentation | free to download
Andrew Cronwright Supervisor: Barry Irwin Overview of this Presentation Randomness Defined PRNG s Introduced Application of PRNG s Focus of PRNG s in this ...
| PowerPoint PPT presentation | free to download
Nickname. Class. 6.857 Lecture - November 2, 2004. Operating ... Implementation requires hash and random number generator. Low-cost PRNG. Physical randomness. ...
| PowerPoint PPT presentation | free to download
Encrypt with pseudo-random number generator (PRNG) ... To use RC4, usually prepend initialization vector (IV) to the key. IV can be random or a counter ...
| PowerPoint PPT presentation | free to download
Algo Proposals. Motivation for PRNG Standard. Increases Security. Complements ... Algo Proposals (due to Bob Baldwin) 1. Cipher Based Single Width Algorithm ...
| PowerPoint PPT presentation | free to view
The pseudorandom random number generator (PRNG), i.e. RC4, is a set of rules ... Pick Random SNonce, Derive PTK = EAPoL-PRF(PMK,ANonce I SNonce I AP MAC Addr I ...
| PowerPoint PPT presentation | free to view
Pseudo Random Number Generation and Random Event Validation through Graphical Analysis What is randomness? A function not affected by any input or state Independent ...
| PowerPoint PPT presentation | free to download
A new image-based steganography technique called triple-A algorithm - is proposed in this paper. It uses the same principle of LSB, where the secret is hidden in ...
| PowerPoint PPT presentation | free to download
Linear Feedback Shift Register (LFSR) L, C(D) Connection polynomial, C(D) ... Initial state [sL-1, sL-2, . . . , s1, s0] LSFR recursion: sj = c1sj-1 c2sj-2 ...
| PowerPoint PPT presentation | free to view
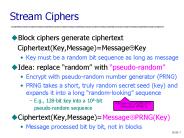
Key must be a random bit sequence as long as message. Idea: replace 'random' with 'pseudo-random' ... To use RC4, usually prepend initialization vector (IV) to the key ...
| PowerPoint PPT presentation | free to download
Criptografia de Chave Sim trica Cap tulo 2
| PowerPoint PPT presentation | free to download
CS 380S 0x1A Great Papers in Computer Security Vitaly Shmatikov http://www.cs.utexas.edu/~shmat/courses/cs380s/ *
| PowerPoint PPT presentation | free to download
Blum-Blum-Shub (BBS) method, named after the authors who ... BBS involves choosing two primes p and q that both have a reminder of 3 when divided by 4 ...
| PowerPoint PPT presentation | free to view
CS 6431 Network Telescopes Vitaly Shmatikov
| PowerPoint PPT presentation | free to download
A random selection of a number from a set or range of numbers is one in which ... Derrick H. Lehmer developed this method in 1951. ...
| PowerPoint PPT presentation | free to view
1997 BIND 16-bit transaction ids not randomized, easily guessable. 2002 BIND sends multiple recursive queries simultaneously, birthday paradox ...
| PowerPoint PPT presentation | free to view
Title: William Stallings, Cryptography and Network Security 5/e Subject: Lecture Overheads - Ch 12 Author: Dr Lawrie Brown Last modified by: Nemo Created Date
| PowerPoint PPT presentation | free to download
CS 6431 Security Protocols Vitaly Shmatikov
| PowerPoint PPT presentation | free to download
ELEC5616 computer and network security matt barrie mattb@ee.usyd.edu.au CNS2010 lecture 4 :: cyphers II *
| PowerPoint PPT presentation | free to view
Generate a random number. not truly random, but uniform in the space of the numbers, so, pseudo. Using a pseudo-random bit generator. There is a seed. ...
| PowerPoint PPT presentation | free to view
Title: Author: snmphost Last modified by: tsaiwn Created Date: 7/2/2000 4:21:46 AM Document presentation format:
| PowerPoint PPT presentation | free to download
How I Met Your Girlfriend: The discovery and execution of entirely new classes of Web attacks in order to meet your girlfriend. Samy Kamkar samy@samy.pl
| PowerPoint PPT presentation | free to download
... how to guess session ids in the Apache Java implementation for Servlet 2.4 ... Seeding can use system based noise/entropy (process scheduling, hard disk timing, ...
| PowerPoint PPT presentation | free to download
Default power analysis is done by probabilistic flipping of ... CRP. 191822. DES3. 206606. CODEC (V0) Area (um^2) 0.165. 2.832. 1.186. 1.647. SPI (V1) 0.250 ...
| PowerPoint PPT presentation | free to view
Cryptography and Network Security Chapter 7 Fifth Edition by William Stallings Lecture s by Lawrie Brown * A typical stream cipher encrypts plaintext one byte at ...
| PowerPoint PPT presentation | free to download
Cryptography and Network Security Chapter 10 Fifth Edition by William Stallings Lecture s by Lawrie Brown * In the Diffie-Hellman key exchange algorithm, there ...
| PowerPoint PPT presentation | free to download
Cryptography and Network Security Chapter 10 Fifth Edition by William Stallings Lecture s by Lawrie Brown * In the Diffie-Hellman key exchange algorithm, there ...
| PowerPoint PPT presentation | free to download
... of the paper 'Your 802.11 Wireless Network has No Clothes' ... ( Parking lot attacks) And a simple eavesdropping attack against 802.11 shared key authentication. ...
| PowerPoint PPT presentation | free to download
Bad cryptography, bad implementations, bad design ... Server just rebooted and needs randomness....is there enough entropy after being ...
| PowerPoint PPT presentation | free to download
Criptografia de Chave Sim trica Cap tulo 2 Introdu o O primeiro tipo bastante pr tico de criptografia chamado de criptografia sim trica.
| PowerPoint PPT presentation | free to download
Encrypting with Block Ciphers CS 470 Introduction to Applied Cryptography Instructor: Ali Aydin Selcuk How to Encrypt with a Block Cipher? Electronic Codebook (ECB ...
| PowerPoint PPT presentation | free to download
Los algoritmos criptogr ficos implementados en hardware son m s seguros. ... El hardware presente la ventaja de procesar un alto volumen de informaci n en ...
| PowerPoint PPT presentation | free to view
Title: CH-5: Confidentiality Subject: Security Author: H. Yoon Last modified by: Technology Created Date: 3/2/1998 8:57:48 AM Document presentation format
| PowerPoint PPT presentation | free to view
software: exploiting the occurences of (pseudo) non deterministic external events ... HAVEG is CPU intensive ... One CPU second worth recommended per phase ...
| PowerPoint PPT presentation | free to download
Create an encrypted audio steganography (information hiding) device ... Artz, Donavan 'Digital Steganography: Hiding Data within Data' IEEE Internet Computing Magazine ...
| PowerPoint PPT presentation | free to view
* A true random number generator (TRNG) uses a nondeterministic source to produce randomness. Most operate by measuring unpredictable natural processes, ...
| PowerPoint PPT presentation | free to download
Secure Programming, Continued CS 236 On-Line MS Program Networks and Systems Security Peter Reiher
| PowerPoint PPT presentation | free to download
PREVIOUS GNEWS 7 Patches 6 Critical 35 CVEs Affected .NET, GDI+, IE, Defender, DirectShow MS13-052 - .NET Framework and Silverlight, Remote Code MS13-053 ...
| PowerPoint PPT presentation | free to download
This deviation is denominated linear probability bias. Symmetric systems. Denominate the probability that the equation holds with pL. ...
| PowerPoint PPT presentation | free to view
... least probable symbols into one composite symbol (sum of probabilities) ... Revise list of symbols using the composite symbol in order of decreasing probability ...
| PowerPoint PPT presentation | free to download
Ha ovac funkce, MD5 a nsk tok To nejlep , co pro v s kryptologov mohou ud lat je, kdy v s p esv d , abyste jim slep ned v ovali.
| PowerPoint PPT presentation | free to download
In other words, flipping bit n in the message results in a deterministic set of ... Because flipping bits carries through after an RC4 decryption, this allows the ...
| PowerPoint PPT presentation | free to view
Both Link and End-to-End. Front-End Processor Function. E-mail Gateway. OSI email gateway TCP. no end-to-end protocol below appl. layer. networks terminate at mail ...
| PowerPoint PPT presentation | free to download
Stream Cipher Random numbers play an important role in the use of encryption for various network security applications. In this section, we provide a brief overview ...
| PowerPoint PPT presentation | free to view
Random Number Generation (RNG) read Numerical Recipes on random numbers and the chi-squared test. Today we discuss how to generate and test random numbers.
| PowerPoint PPT presentation | free to view
A is an arbitrary multiplier of Xn-1. N is the base of the modulus ... to get started we need an arbitrary X0, or seed. Arbitrary Range for Pseudo-Random Numbers ...
| PowerPoint PPT presentation | free to download
Drop-in replacements for adding message to a Digital Audio Stream, or a MIDI Stream. ... storage rate in CD-quality audio streams. Very small devices for ...
| PowerPoint PPT presentation | free to view
security and trusted vs. Vulnerability vs. Structure
| PowerPoint PPT presentation | free to download
RAND Corporation in 1955 released a table of a million random digits. ... a function f defined on an interval (a, b) and having the following properties: ...
| PowerPoint PPT presentation | free to download
Alice and Bob meet once, and set a one-time pad K. Alice encrypt plaintext P with K ... JCP: Servlet 2.4. released 24 November, 2003. Java Session Framework ...
| PowerPoint PPT presentation | free to view
Stream Ciphers CS 470 Introduction to Applied Cryptography Instructor: Ali Aydin Selcuk CS470, A.Selcuk Stream Ciphers * CS470, A.Selcuk Stream Ciphers * Stream ...
| PowerPoint PPT presentation | free to download
Parallel White Noise Generation. on a GPU via Cryptographic Hash. Stanley Tzeng Li-Yi Wei ... algorithm for white noises. independent evaluation for every ...
| PowerPoint PPT presentation | free to download
Alice is eating at Fat Tony's Mafia Diner. Fast Eddie is shopping at Bob's jewelery store ... to any number of diners. elec5610. handout 13 :: crypto protocols ...
| PowerPoint PPT presentation | free to view
Block cipher (PRP), PRG, MAC, Cryptographic hash. Java Cryptography Extension ... Cosmetics. Coding style. Efficiency. Stuck? Use the newsgroup (su.class.cs255) ...
| PowerPoint PPT presentation | free to download
read 'Numerical Recipes' on random numbers and chi-squared test. Today we discuss how to generate and test random numbers. What is a random number? ...
| PowerPoint PPT presentation | free to view